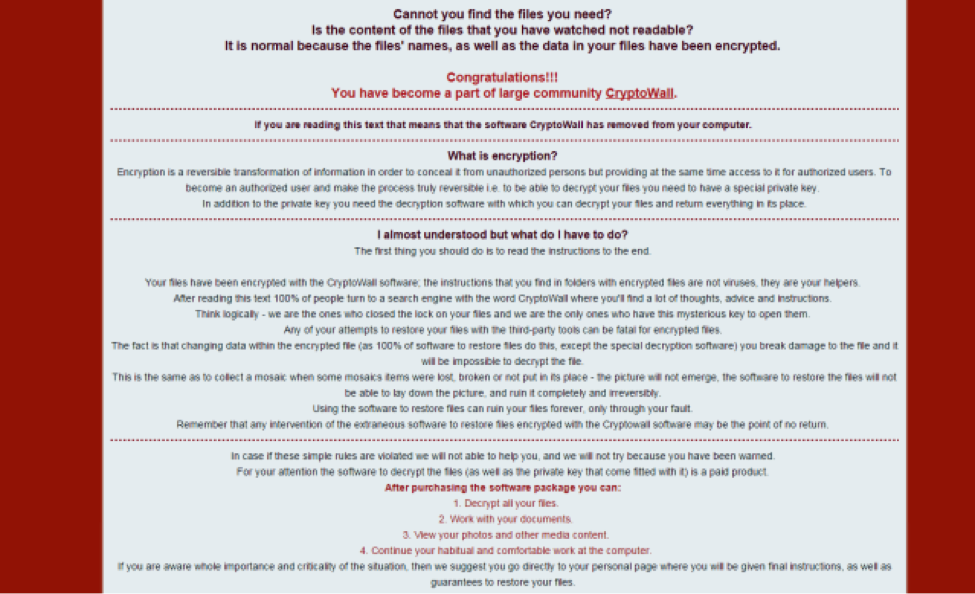
 What's New?
The 4.0 version of CryptoWall shares many similarities with its predecessors. One of the most important distinctions is that filenames and extensions are now also encrypted. This is very nefarious, in the fact that most users will not be able to determine exactly what data they have lost. Ostensibly this increases the chances that they will pay up to decrypt their data. Additionally, the tell tale ransomware file extensions (.xxxx, .yyyy, .zzzz) are no longer present to aid in quick visual detection. Another distinction observed upon execution is the malware no longer attempts to leverage bcdedit to disable the Windows Startup Repair service . It now will first check to see if administrator privileges exist and then leverage API calls, namely SRRemoveRestorePoint, to delete system restore points directly. While some have reported that the new command and control routine was dramatically improved and difficult to detect, we have found no evidence of this. In fact infrastructure reuse was quite high, with the same clear text HTTP with an RC4 encrypted payload. Within 48 hours of first being seen in the wild, AntiVirus detection was very broad across the industry.
What's New?
The 4.0 version of CryptoWall shares many similarities with its predecessors. One of the most important distinctions is that filenames and extensions are now also encrypted. This is very nefarious, in the fact that most users will not be able to determine exactly what data they have lost. Ostensibly this increases the chances that they will pay up to decrypt their data. Additionally, the tell tale ransomware file extensions (.xxxx, .yyyy, .zzzz) are no longer present to aid in quick visual detection. Another distinction observed upon execution is the malware no longer attempts to leverage bcdedit to disable the Windows Startup Repair service . It now will first check to see if administrator privileges exist and then leverage API calls, namely SRRemoveRestorePoint, to delete system restore points directly. While some have reported that the new command and control routine was dramatically improved and difficult to detect, we have found no evidence of this. In fact infrastructure reuse was quite high, with the same clear text HTTP with an RC4 encrypted payload. Within 48 hours of first being seen in the wild, AntiVirus detection was very broad across the industry.
 Kill Chain Modeling
Reconnaissance: Website drive-by, Email harvesting, Regional campaigns
Disrupt: Web filtering, OSINT alerts, threat intelligence sharing
When it comes to preventing Cryptowall infections, the first line of defense is a strong web security filtering solution. Because ransomware is typically conducted as a large campaign, vendors often have updated detections in place within 48 hours of the malicious websites going active. A key gap in most environments is the lack of web filtering for endpoints once they leave the corporate network. An agent on the endpoint or a proxy in the cloud solution can assist in closing this gap. Creating alerts based on either real or fake corporate email addresses found in Open Source Intelligence (OSINT) sources (i.e pastebin) can often provide early warning to email harvesting, or even worse, a data breach. Finally, threat intelligence sharing within your company vertical or geographic region can help aid your security team in early detection or blocking of a campaign.
Weaponization: Malicious PDF/HTML file, Malicious JavaScript
Disrupt: Restrict downloads & JavaScript
While not always feasible to the business, restricting downloads from the Internet is a valuable control to consider. Blocking the download of an EXE is often much easier than business buy-in on blocking the download of PDF files. Either leveraging specific AD groups with Internet download rights or providing a click to continue prompt are often a more palatable solution. Similarly, limiting JavaScript execution from unknown or untrusted websites can prevent a considerable amount of commodity malware in addition to ransomware. Trying to manage this centrally for a large user base can be a significant workload. Browser add-ins like NoScript and QuikSet can give the user more control in the browsing experience, but still default to no active scripting.
Delivery: Browser exploit kits, Email spam
Disrupt: Exploit kit signatures, Email filtering
Exploit kits are considered an essential tool for the majority of the less sophisticated cyber criminals targeting the public. Nuclear, Angler, SweetOrange and Magnitude exploit kits have picked up where the Blackhole exploit kit has faded away in recent years. Mila Parkour of Contagio Dump maintains a great list of exploit kit capabilities. Similarly, Emerging Threats has very good detection for popular exploit kits available in their Current_Events rule set. Email security products will often do an adequate job blocking ransomware emails, like those from the Cutwail botnet, however this doesn’t necessarily protect you when the email comes in private webmail or the end user decides to release it from quarantine. End user training on how to handle suspicious web links and emails should still be a pillar of your security awareness program.
Exploitation: Adobe Flash/Reader, IE, Java, Silverlight, ActiveX
Disrupt: Software patching, EMET 5.x
A robust patching program can mitigate the threat posed by exploit kits. A majority of the exploits used are typically older than a year after a software patch was made available. The notable exception to this is Adobe Flash, which has been a major thorn in security practitioners’ side for quite some time. In addition, running older versions of Internet Explorer is quite common to support legacy applications. A great free control to address these gaps is Microsoft’s EMET tool. It is configurable using Group Policy and can prevent quite a few attack vectors used by adversaries. Limiting the ability to install software often will prevent rogue software installs that are not managed by the corporate patching process.
Installation
Kill Chain Modeling
Reconnaissance: Website drive-by, Email harvesting, Regional campaigns
Disrupt: Web filtering, OSINT alerts, threat intelligence sharing
When it comes to preventing Cryptowall infections, the first line of defense is a strong web security filtering solution. Because ransomware is typically conducted as a large campaign, vendors often have updated detections in place within 48 hours of the malicious websites going active. A key gap in most environments is the lack of web filtering for endpoints once they leave the corporate network. An agent on the endpoint or a proxy in the cloud solution can assist in closing this gap. Creating alerts based on either real or fake corporate email addresses found in Open Source Intelligence (OSINT) sources (i.e pastebin) can often provide early warning to email harvesting, or even worse, a data breach. Finally, threat intelligence sharing within your company vertical or geographic region can help aid your security team in early detection or blocking of a campaign.
Weaponization: Malicious PDF/HTML file, Malicious JavaScript
Disrupt: Restrict downloads & JavaScript
While not always feasible to the business, restricting downloads from the Internet is a valuable control to consider. Blocking the download of an EXE is often much easier than business buy-in on blocking the download of PDF files. Either leveraging specific AD groups with Internet download rights or providing a click to continue prompt are often a more palatable solution. Similarly, limiting JavaScript execution from unknown or untrusted websites can prevent a considerable amount of commodity malware in addition to ransomware. Trying to manage this centrally for a large user base can be a significant workload. Browser add-ins like NoScript and QuikSet can give the user more control in the browsing experience, but still default to no active scripting.
Delivery: Browser exploit kits, Email spam
Disrupt: Exploit kit signatures, Email filtering
Exploit kits are considered an essential tool for the majority of the less sophisticated cyber criminals targeting the public. Nuclear, Angler, SweetOrange and Magnitude exploit kits have picked up where the Blackhole exploit kit has faded away in recent years. Mila Parkour of Contagio Dump maintains a great list of exploit kit capabilities. Similarly, Emerging Threats has very good detection for popular exploit kits available in their Current_Events rule set. Email security products will often do an adequate job blocking ransomware emails, like those from the Cutwail botnet, however this doesn’t necessarily protect you when the email comes in private webmail or the end user decides to release it from quarantine. End user training on how to handle suspicious web links and emails should still be a pillar of your security awareness program.
Exploitation: Adobe Flash/Reader, IE, Java, Silverlight, ActiveX
Disrupt: Software patching, EMET 5.x
A robust patching program can mitigate the threat posed by exploit kits. A majority of the exploits used are typically older than a year after a software patch was made available. The notable exception to this is Adobe Flash, which has been a major thorn in security practitioners’ side for quite some time. In addition, running older versions of Internet Explorer is quite common to support legacy applications. A great free control to address these gaps is Microsoft’s EMET tool. It is configurable using Group Policy and can prevent quite a few attack vectors used by adversaries. Limiting the ability to install software often will prevent rogue software installs that are not managed by the corporate patching process.
Installation
- Download
- Javascript downloads and executes 10-digit EXE to %TEMP%
- Runtime
- Inject into Explorer.exe
- Disable System Restore
- Delete VSS copies
- Inject into svchost.exe
- File Persistence
- Random Process Names (%AppData%, %AppDataLocal%, %AppDataRoaming%, %ProgramData%, %userprofile%, %Temp%, C:\<random>, %WinDir%, %AppDataRoaming%\Microsoft\Windows)
- Registry Persistence
- Current User Registry Hive ( Software\Microsoft\Windows\CurrentVersion\Run & RunOnce, Software\<RandomName>, <unique computer id>\<random id>, ControlPanel\Desktop\Wallpaper)
POST /BMzH_7.php?c=dy8xua4ie5i5yjm HTTP/1.1 Accept: */* Content-Type: application/x-www-form-urlencoded Connection: Close Content-Length: 124 User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E) Host: <removed> Cache-Control: no-cache m=31716334647368686636721ec65ae3288e319bccce2ff1750f3d13b78c1ad3d920009b3de9932cf1272e8b5744de1c21b7e72767c2f863e5a4c4c4f919
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"ET TROJAN CryptoWall? Check-in"; flow:established,to_server; urilen:<134; content:"="; offset:1; depth:1; http_client_body; content:" MSIE "; fast_pattern; http_user_agent; content:"Accept|3a 20|*/*|0d 0a|Content-Type|3a 20|application/x-www-form-urlencoded|0d 0a|"; depth:62; http_header; content:!"|0d 0a|Accept-"; nocase; http_header; content:!"Referer|3a|"; http_header; pcre:"/<\/=>{8,}$/U"; pcre:"/^={80,}$/P"; reference:md5,3c53c9f7ab32a09de89bb44e5f91f9af; classtype:trojan-activity; sid:2018452; rev:15;)
Blocking the Tor protocol, .onion sites, and any traffic inbound from known Tor exit nodes is a very easy defense that will aid in other areas, specifically limiting adversarially reconnaissance options. Another great control is DNS Sinkholing, such as CrowdStrike’s FalconDNS, which will block any traffic to known malicious domains at the time of name resolution. Web filtering has another chance to block the initial check in, post exploitation. Lastly, proxy authentication, which is very much preferred over transparent proxying, can stop variants that are not proxy aware and rely on permissive firewall rules to egress the network.
Actions on Target:
- Download Public RSA Encryption Key
- Encryption of files (Office Docs, Photos, Music, Source code, etc)
- AES, RSA-2048, MS CryptoAPI
- File extension renamed (older versions)
- Filename and extension encrypted (new in 4.0)
- EXEs, DLLs and other system related files and directories are excluded from encryption to maintain system stability
- Includes Mapped Drives & Cloud Storage (dropbox, onedrive, googledrive, etc)
- User Splash Screen once encryption is complete
- Collect $$$ for private decryption key (Paypal, Bitcoin, litecoin, MoneyPak, prepaid cards)
- Volume Shadow Copy deletions
Applying the controls detailed above with a focus on the combination of essentials of patching, backups, and web filtering will help mitigate the ransomed are threat; however, more can be done. CrowdStrike’s Falcon Host uses behavioral Indicators of Attack (IOAs) to detect and prevent CryptoWall infections. These IOAs detect the activities that ransomware has to undertake in order to accomplish it's ultimate objective of encrypting user's data and preventing recovery without payment of ransom, making it very difficult for CryptoWall to avoid detection even when new polymorphic versions are released. Unlike approaches that use only signatures or machine learning algorithms that can only examine the contents of a malware binary, something that is easy for an attacker to bypass, Falcon Host IOAs examine and correlate the runtime effects of CryptoWall malware family by leveraging the CrowdStrike Threat Graph and can take automatic detection and prevention actions before the encryption of data can take effect.
Please click to find out more about
Falcon Host.
If you are struggling with advanced malware and
sophisticated attacks, let CrowdStrike Services help you with our proactive and response service offerings. Click here to learn more about how our world class consultants can help you stop breaches in their tracks.
CrowdStrike will be announcing new capabilities to its Falcon Platform in the coming weeks that will be made available to customers pertaining to CryptoWall protection, Linux availability, and more.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)

































