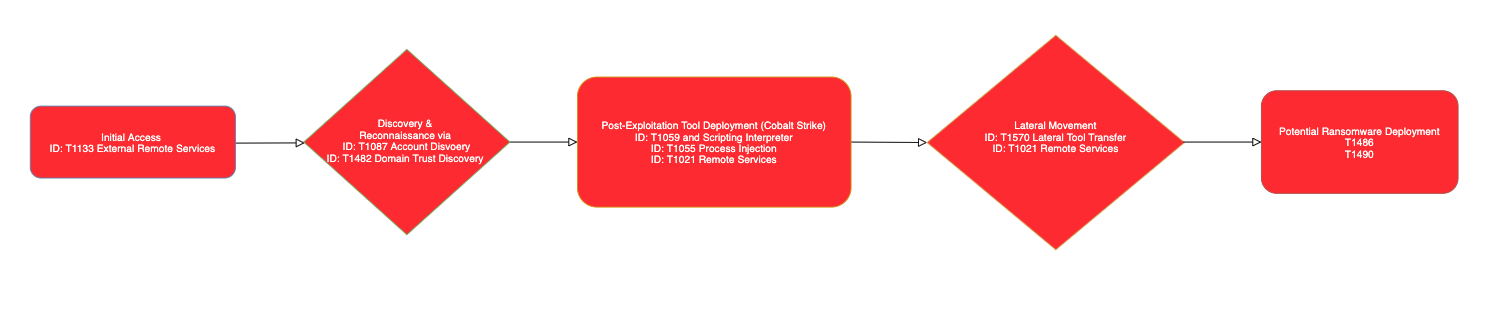
In this blog, we describe a string of recent incidents in which the CrowdStrike Falcon® Complete™ team observed a financially motivated eCrime operator (likely WIZARD SPIDER) use compromised external remote services (Microsoft Remote Desktop Protocol, or RDP) along with Cobalt Strike in an unsuccessful attempt to deploy ransomware. This activity indicates a notable increase in the adversary’s tactics to include RDP brute forcing along with their more traditional modus operandi for initial access via phishing or leveraging their partner networks of access brokers.
We will provide a brief overview of the observed tactics, techniques and procedures (TTPs) in these cases along with an outline of the Falcon Complete team’s approach to quickly detect and contain the interactive attacker before the threat actor was able to complete actions on objective.
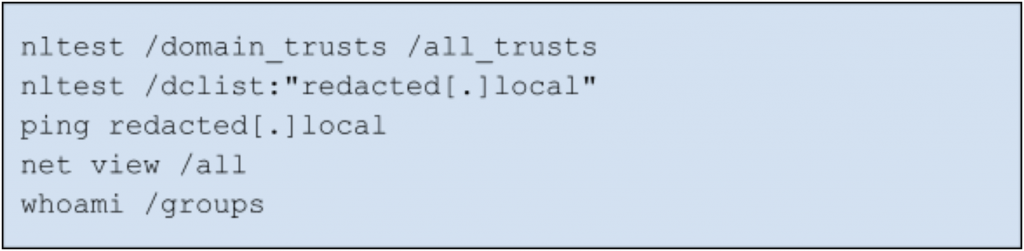 Figure 2. Example reconnaissance commands
The threat actor then installed additional tooling for post-exploitation activities. This typically included Cobalt Strike for command and control, where the stager DLLs were written to the user's
Figure 2. Example reconnaissance commands
The threat actor then installed additional tooling for post-exploitation activities. This typically included Cobalt Strike for command and control, where the stager DLLs were written to the user's Containment and Investigation
At this point, we were confident that an adversary was interactive and had compromised the victim host. We observed them attempting to perform reconnaissance in preparation for privilege escalation and lateral movement. The next steps were to contain and identify the full scope of the incident. Figure 8. Alternative method for event logs
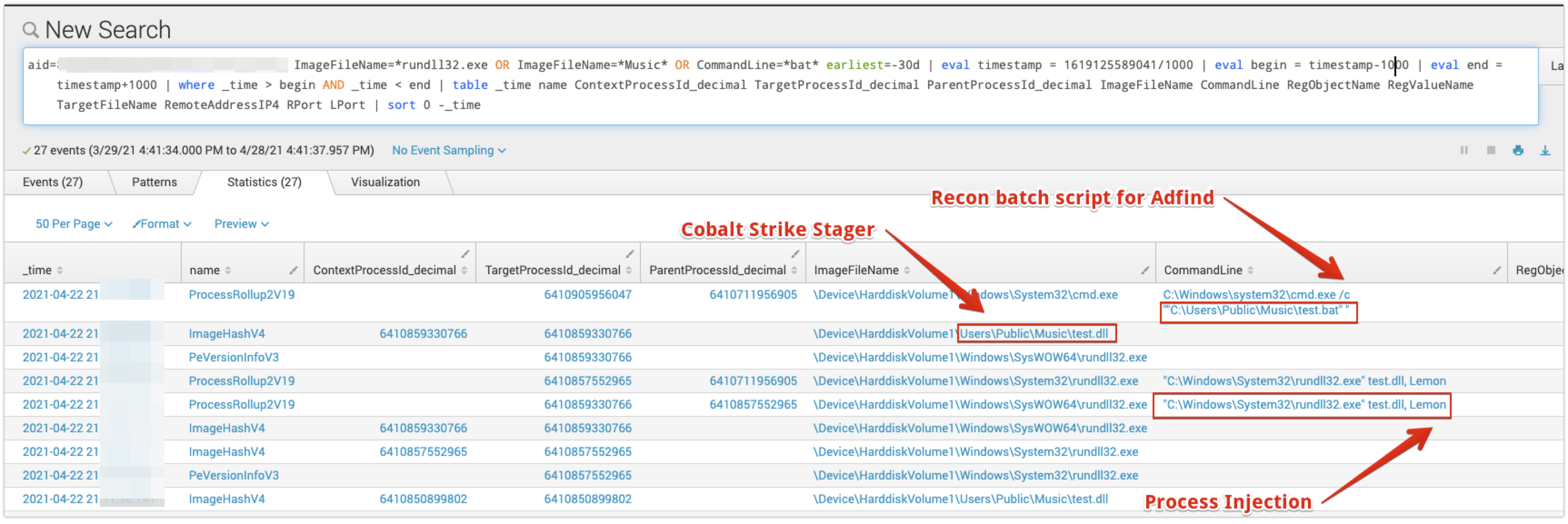
The EAM application can also be used to search for residual host artifacts that the adversary may have left behind on the system. From the initial detection triage, we can then pivot from data points such as the injected process, directory locations and specific file types of interest. A basic query is shown in Figure 9 to identify the artifacts of interest that remain on disk.
Based on observations from previous intrusions, we knew that a batch file may be present in the same directory as the Cobalt Strike stager. As noted before, this batch file is responsible for conducting further reconnaissance with Adfind to explore the Active Directory environment. As shown in Figure 9, the EAM query also captured the command
Figure 8. Alternative method for event logs
The EAM application can also be used to search for residual host artifacts that the adversary may have left behind on the system. From the initial detection triage, we can then pivot from data points such as the injected process, directory locations and specific file types of interest. A basic query is shown in Figure 9 to identify the artifacts of interest that remain on disk.
Based on observations from previous intrusions, we knew that a batch file may be present in the same directory as the Cobalt Strike stager. As noted before, this batch file is responsible for conducting further reconnaissance with Adfind to explore the Active Directory environment. As shown in Figure 9, the EAM query also captured the command  In this case, we have rated this remediation as “Easy,” based on the velocity and total effort required for proper recovery. Due to the rapid response time to contain and evict the adversary, there was not an extensive list of clean-up actions to be taken.
STEP 1. Finding and Killing the Malicious Process
Falcon did a lot of the work for us here and had already terminated the injected processes. The running process was reviewed to ensure no injected threads were still executing malicious code. We have provided more details for finding injected process in previous blogs:
In this case, we have rated this remediation as “Easy,” based on the velocity and total effort required for proper recovery. Due to the rapid response time to contain and evict the adversary, there was not an extensive list of clean-up actions to be taken.
STEP 1. Finding and Killing the Malicious Process
Falcon did a lot of the work for us here and had already terminated the injected processes. The running process was reviewed to ensure no injected threads were still executing malicious code. We have provided more details for finding injected process in previous blogs:The Efficiency of Falcon Complete
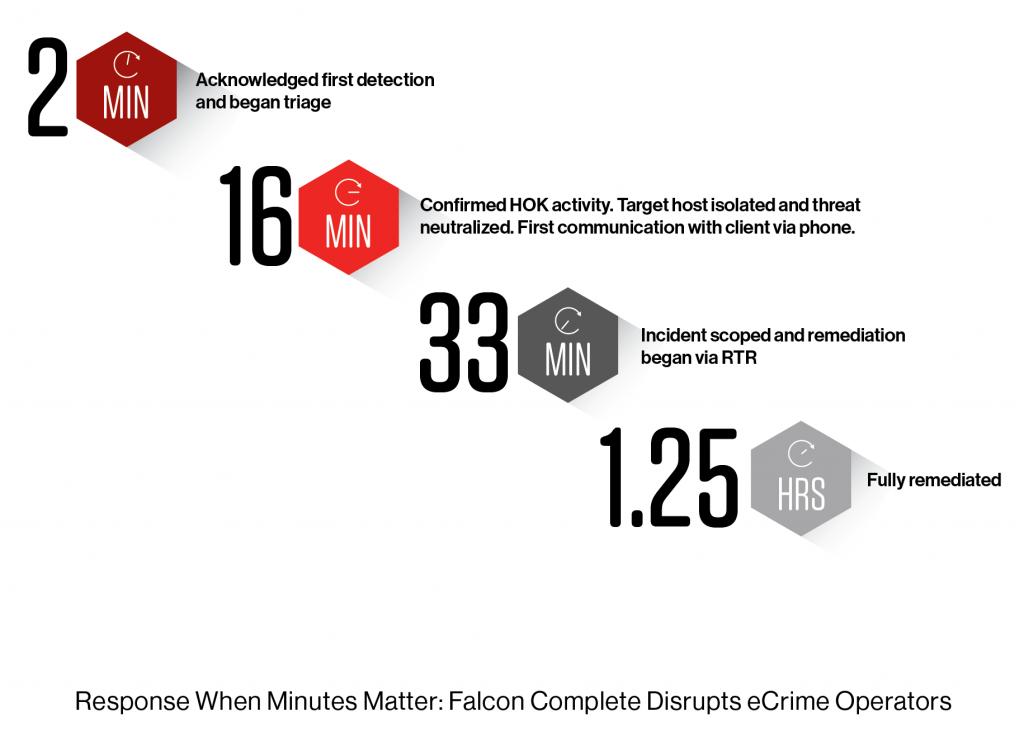
The Falcon Complete team identified an interactive adversary that had compromised an external remote service and gained illicit access to a managed host in our client’s environment. This threat actor attempted to download and execute additional tooling in a likely attempt to stage ransomware. The team quickly contained, scoped and remediated this threat with the Falcon RTR capability without requiring any reboots, reimages or other disruption to the client’s business operations. The following figure highlights the significant milestones during our detection and response efforts.
 This activity was attributed to the financially motivated adversary tracked as WIZARD SPIDER.
This activity was attributed to the financially motivated adversary tracked as WIZARD SPIDER.
Campaign TTPs Overview
In recent weeks, the Falcon Complete team has conducted several response operations to incidents involving compromised RDP credentials as an initial infection vector. This was followed by execution of reconnaissance commands, installation of Cobalt Strike and additional tooling. CrowdStrike Intelligence assesses that the threat actor responsible for this activity is likely WIZARD SPIDER due to the following overlapping TTPs with WIZARD SPIDER activity clusters:- Cobalt Strike stager DLLs executed from the victim's Music directory
- Network indicators identified via hunting for related samples and infrastructure exhibiting attributes of WIZARD SPIDER infrastructure
- Using nltest and net Windows utilities to conduct reconnaissance activity
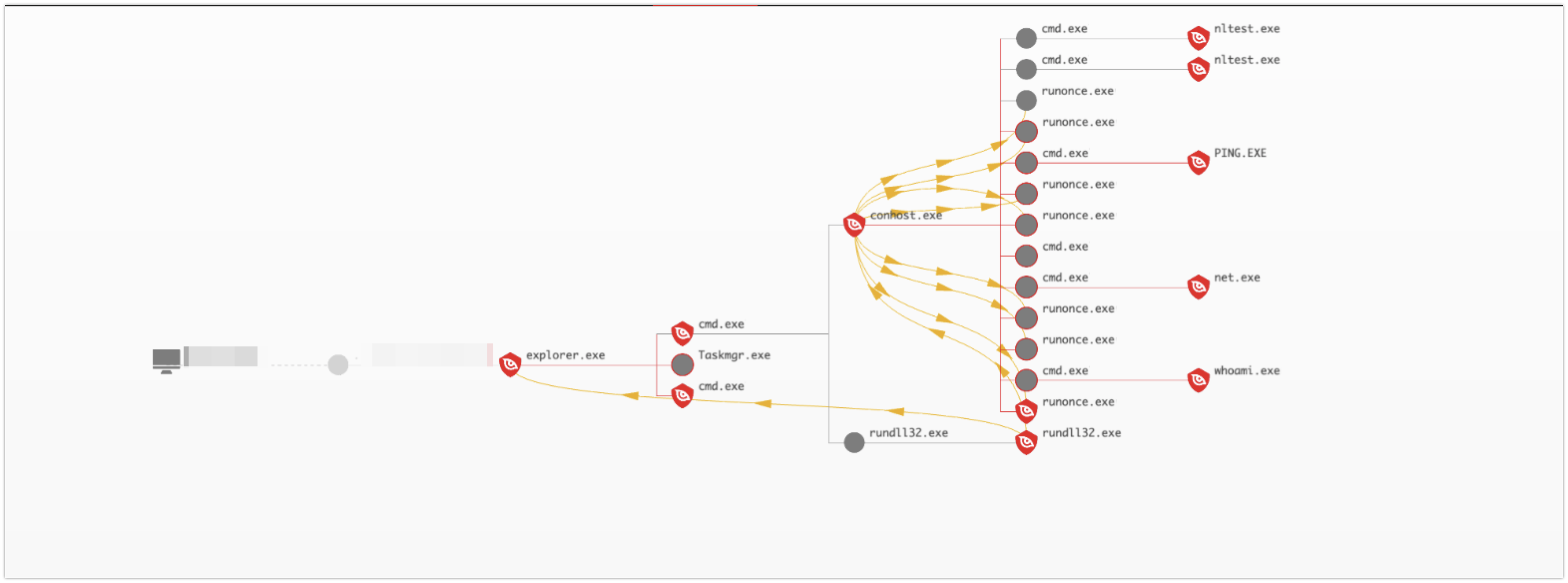
Once the actor has established a foothold within an environment, they will proceed with reconnaissance activities to enumerate accounts and systems that may represent high-value targets. Multiple reconnaissance commands were observed — in particular, nltest appears to be a hallmark of this activity. Shown in Figure 2, the adversary first enumerated the trusted domains in the environment, and then a list of domain controllers. Their goal was likely to move laterally to one of these systems.
 Figure 2. Example reconnaissance commands
Figure 2. Example reconnaissance commandsMusic directory. BloodHound or Adfind were pulled down from an external resource for additional account enumeration in preparation for lateral movement. This secondary reconnaissance is handled by a BAT file written to the same Music directory.
Figure 3 presents many of the common patterns related to the observed activity cluster as seen in the Falcon console. This process tree graph view indicates the initial process injection under the explorer.exeprocess via
rundll32.exe, along with the initial reconnaissance commands such as nltest under the conhost.exe process.
Falcon Complete Detection and Response
Initial Detection and Triage
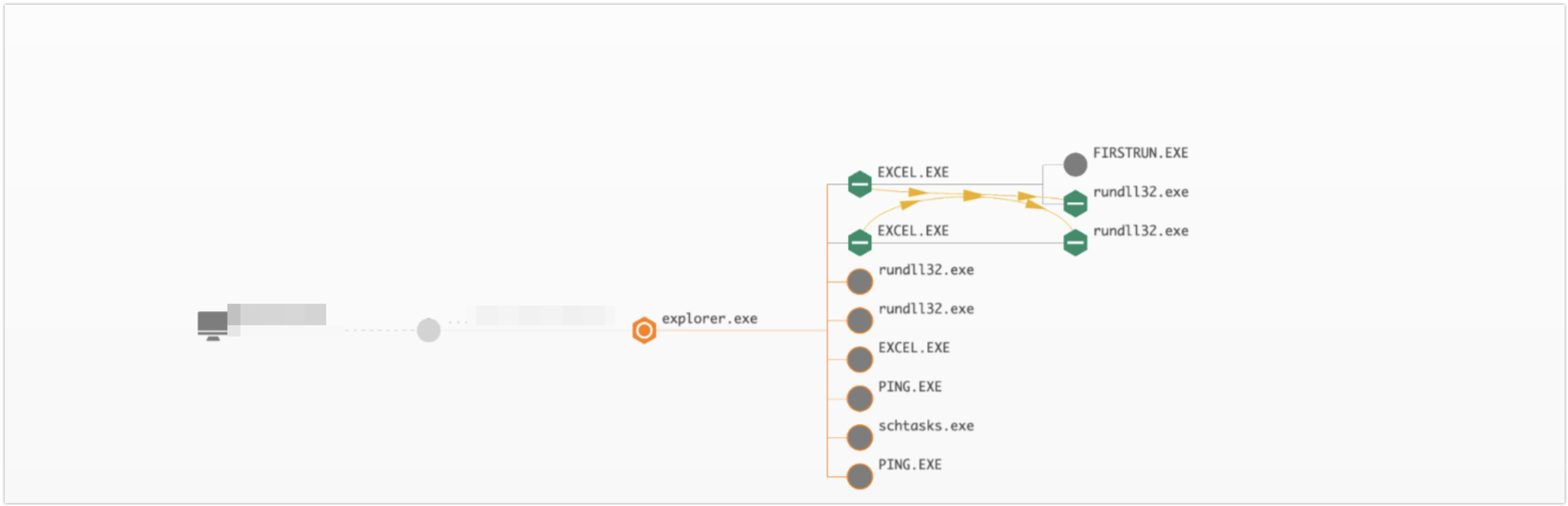
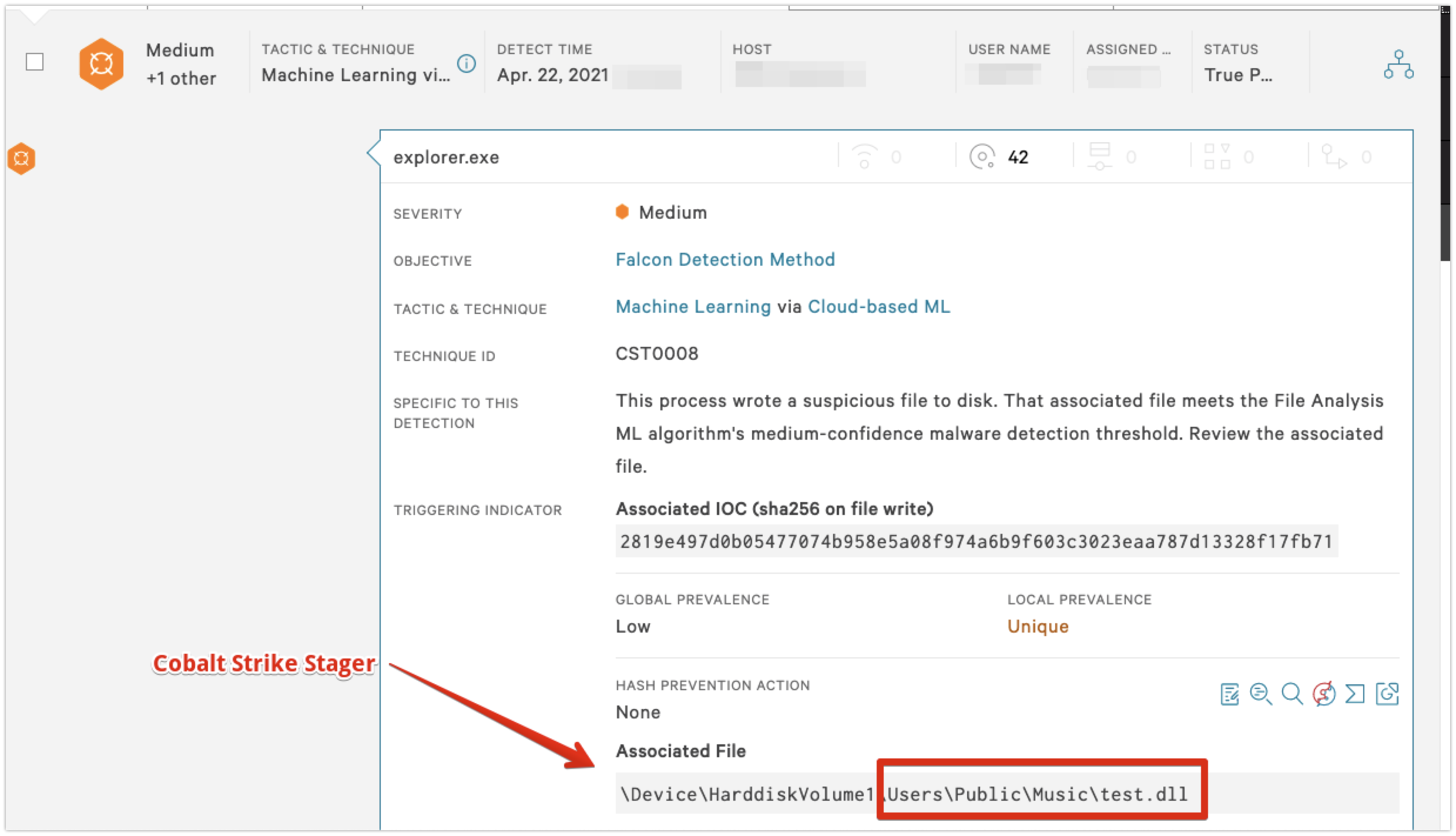
The Falcon Complete team has observed multiple related incidents over the past several weeks that share common TTPs, as noted above. Below, we present a case study of these contextual indicators observed during a specific incident. The response process began when the Falcon Complete team received a high-severity machine learning (ML) detection for a suspicious process injection viarundll32.exe. Further investigation indicated that this process injection was related to the threat actor abusing Microsoft Office Visual Basic for Applications (VBA) macros in an uncommon way.
This shellcode was a typical stager that functioned as a downloader to fetch a Cobalt Strike payload from the attacker-controlled command and control (C2). These resources were written to the C:\Users\Public\Music directory.
Adversaries utilizing Microsoft Office documents weaponized with VBA macros is nothing new, but the activity described above differs significantly from phishing campaigns leveraging macro documents to achieve initial access. Instead, the document was being used to execute code after initial access had been achieved on a system via a compromised account.
We have observed multiple instances of files written that were named either "New Microsoft Word Document.docx" or "New Microsoft Excel Worksheet.xlsx," which are the default naming schemes for new document templates in Windows. Next, a macro executes a shellcode payload via the rundll32.exe process, which is a Cobalt Strike stager, but the macro’s shellcode is never written to disk.
This is likely an evasion technique attempting to bypass host-based security controls to execute shellcode. What appears to be happening is the threat actors are copying and pasting the malicious macro directly into a blank document template over the RDP session. The advantage of this approach is that the macros are not written to disk and are only executed in memory. This activity was then followed by similar reconnaissance commands observed in Figure 2 above.
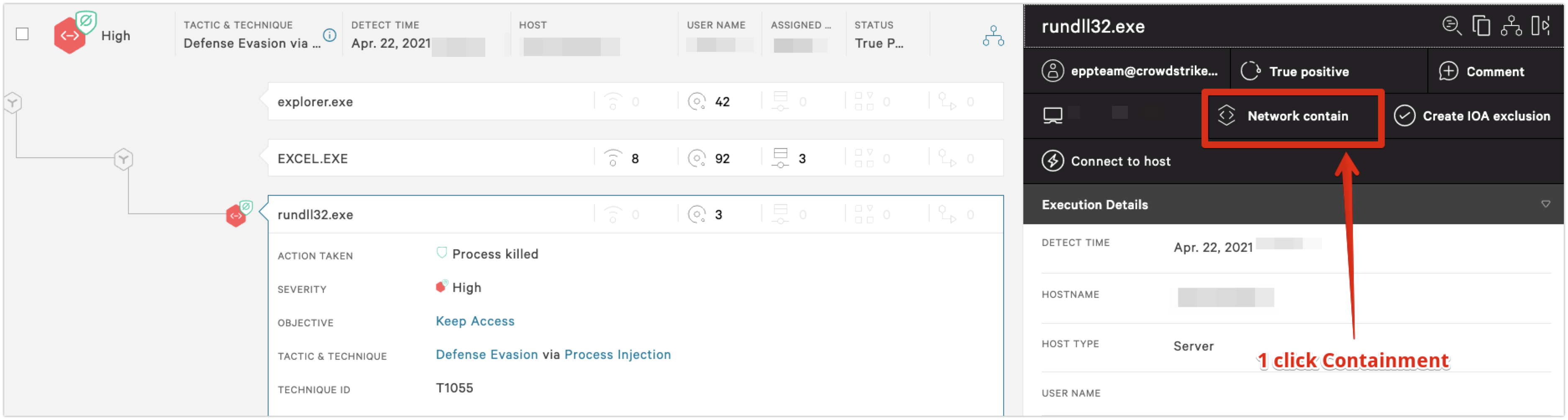
Containment and Investigation
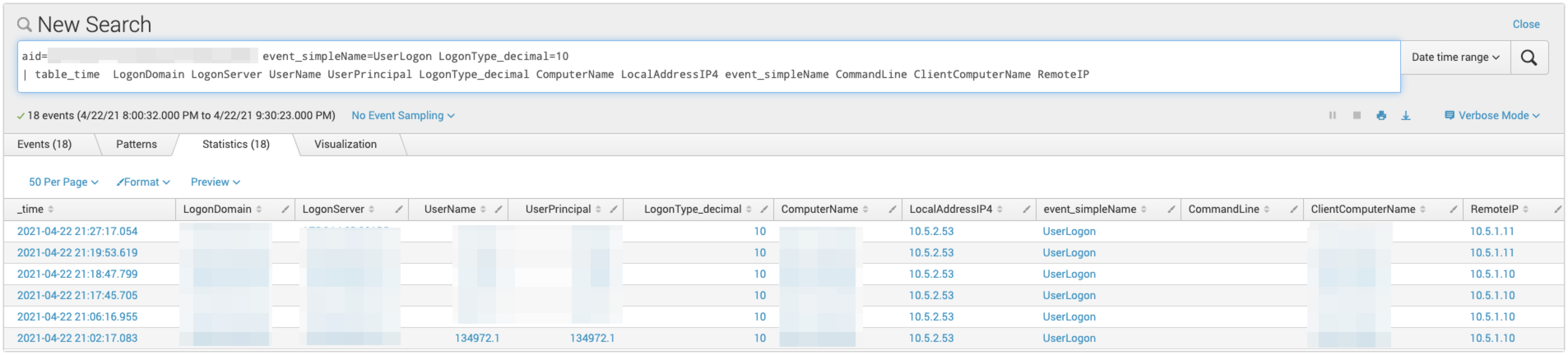
At this point, we were confident that an adversary was interactive and had compromised the victim host. We observed them attempting to perform reconnaissance in preparation for privilege escalation and lateral movement. The next steps were to contain and identify the full scope of the incident.Our analysts have the capability to network-contain a host to prevent the lateral spread of the adversary within the environment. This immediately denies the adversary remote access by only allowing the host to communicate with the CrowdStrike Security Cloud. The next objective of the investigation was to properly scope the intrusion by identifying the affected systems/user accounts and host/network indicators of compromise. We can pivot into our endpoint activity monitoring (EAM) application, which provides endpoint telemetry so we can gain further context and determine the origin of the intrusion. The goal here was determining the user account that the threat actor compromised and leveraged for remote access. In Figure 7, a simple query for
type 10 logons can determine this account. This query also gives us the Remote IP, which is the source host of the RDP logon. This information could also be gleaned from a Falcon Real Time Response (RTR) session on the host to query the security event logs via PowerShell, such as the following snippet:
 Figure 8. Alternative method for event logs
Figure 8. Alternative method for event logsrundll32.exe test.dll, Lemon. This command is responsible and is used for process injection via rundll32.exe. Previously, the Falcon Complete team has observed similar patterns regarding one-word export functions such as "Lemon" in this case, and "Lime" in similar instances. These one-word export functions likely suggest a possible common naming convention for exports, related to Cobalt Strike DLLs across the intrusions observed. Investigators can use this indicator to pivot or enrich related data sets of potentially linked activity clusters.
Next, the team performed dynamic malware analysis on the Cobalt Strike stager sample. We discovered that the binary’s code was configured to reach out to the domain serviapd<.>com for C2. At this point in the investigation, we had determined both the system and user scopes, identified host artifacts and extracted network indicators of compromise (IOCs) from the malware. Armed with this information, the Falcon Complete team could now begin removing the actor's malware from the affected systems.
Remediation
The Falcon Complete team directly performs many of the critical remediation actions for our customers via Falcon RTR. A typical remediation can be broken into three distinct steps:- Killing the malicious processes (e.g., injected rundll, explorer, conhost)
- Locating and removing the persistence mechanism (e.g., compromised accounts, services)
- Removing disk artifacts (e.g., binaries and directories)
 In this case, we have rated this remediation as “Easy,” based on the velocity and total effort required for proper recovery. Due to the rapid response time to contain and evict the adversary, there was not an extensive list of clean-up actions to be taken.
STEP 1. Finding and Killing the Malicious Process
Falcon did a lot of the work for us here and had already terminated the injected processes. The running process was reviewed to ensure no injected threads were still executing malicious code. We have provided more details for finding injected process in previous blogs:
In this case, we have rated this remediation as “Easy,” based on the velocity and total effort required for proper recovery. Due to the rapid response time to contain and evict the adversary, there was not an extensive list of clean-up actions to be taken.
STEP 1. Finding and Killing the Malicious Process
Falcon did a lot of the work for us here and had already terminated the injected processes. The running process was reviewed to ensure no injected threads were still executing malicious code. We have provided more details for finding injected process in previous blogs:
- Automating Remote Remediation of TrickBot: Part 1
- Duck Hunting with Falcon Complete: Remediating a Fowl Banking Trojan, Part 3
- Using multifactor authentication (MFA) for remote access services
- Disabling RDP or any services that are not required
- Using non-standard ports if required
- Deploying technical controls such as Web Application Firewall (WAF) in front of remote services
C:\Users\Public\Music directory.The steps outlined above are the general process for successfully remediating a host for the artifacts of this intrusion set.
The Efficiency of Falcon Complete
The Falcon Complete team identified an interactive adversary that had compromised an external remote service and gained illicit access to a managed host in our client’s environment. This threat actor attempted to download and execute additional tooling in a likely attempt to stage ransomware. The team quickly contained, scoped and remediated this threat with the Falcon RTR capability without requiring any reboots, reimages or other disruption to the client’s business operations. The following figure highlights the significant milestones during our detection and response efforts.
 This activity was attributed to the financially motivated adversary tracked as WIZARD SPIDER.
This activity was attributed to the financially motivated adversary tracked as WIZARD SPIDER.The Falcon Complete team has observed multiple similar TTPs in several recent intrusions that indicate a general tactical increase or preference for compromising external remote services (such as RDP) as an initial infection vector. It is unclear but possible that this activity is simply in addition to this actor’s “normal” email phishing operations. We also noted an interesting usage of a technique leveraging Microsoft Office macros following initial access. It is likely that eCrime actors will continue to use this technique going forward. The Falcon Complete team will continue to track this threat and monitor our clients’ environments for any notable developments.
Additional Resources
- Read more blogs from the Falcon Complete team: Falcon Complete Disrupts Malvertising Campaign Targeting AnyDesk, Response When Minutes Matter: Rising Up Against Ransomware and Falcon Complete Stops Microsoft Exchange Server Zero-Day Exploits.
- Learn more by visiting the Falcon Complete product webpage.
- Read a white paper: CrowdStrike Falcon® Complete: Instant Cybersecurity Maturity for Organizations of All Sizes.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)