August’s Patch Tuesday covered less than half as many patched vulnerabilities as July. Two of the vulnerabilities patched this month (CVE-2021-34481 and CVE-2021-36934) were previously disclosed and have been exploited. Patches include those related to Windows Print Spooler Service; an in-the-wild exploit for a vulnerability relating to Windows Update Medic Service (WaaSMedicSVC); and a vulnerability associated with PetitPotam, a tool used to launch an NTLM relay attack. On top of that, other vulnerabilities have been flagged as “exploitation more likely” by Microsoft, meaning that either attackers have previously exploited similar vulnerabilities or there is a higher probability an exploit will be developed. We also discuss other critical vulnerabilities, common attack types and patching priorities your organization should consider for a strong security posture.
Let’s get started.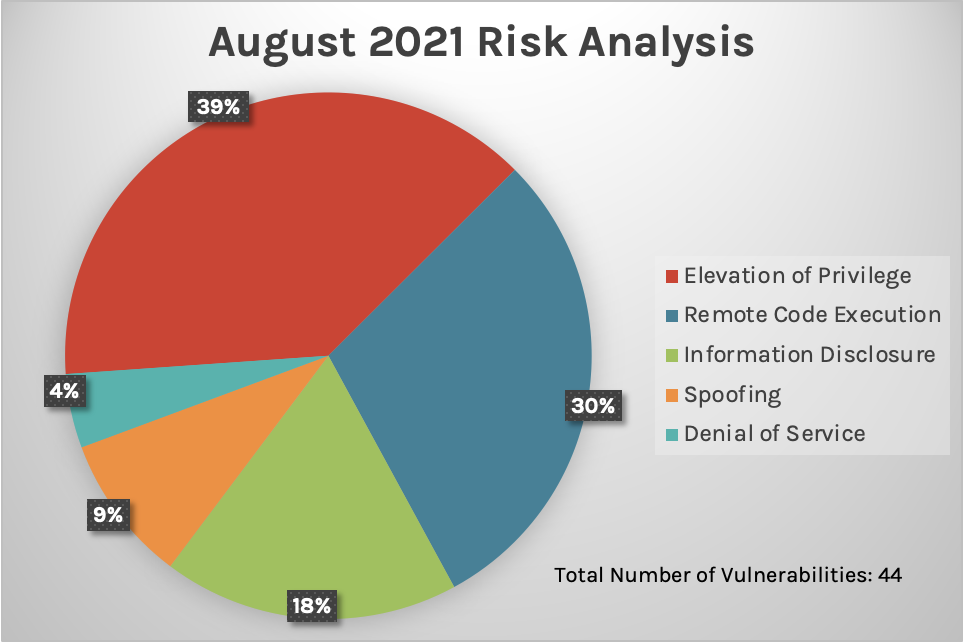 Figure 1. Breakdown of August’s Patch Tuesday attack impact
Figure 1. Breakdown of August’s Patch Tuesday attack impact
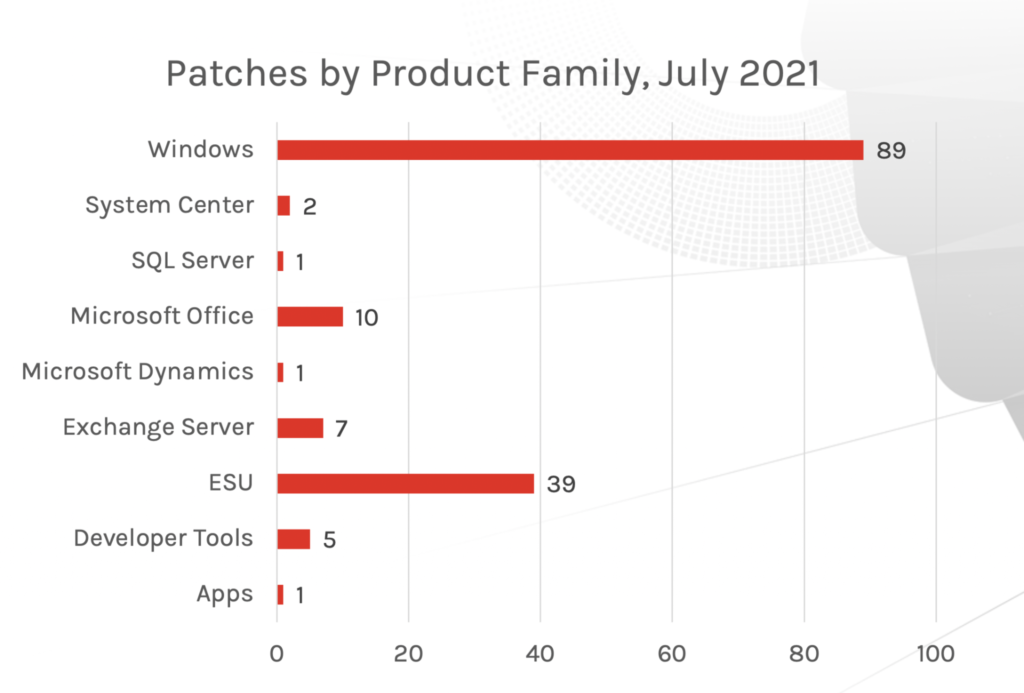 Figure 2: Patch updates by product family, July 2021
Figure 2: Patch updates by product family, July 2021
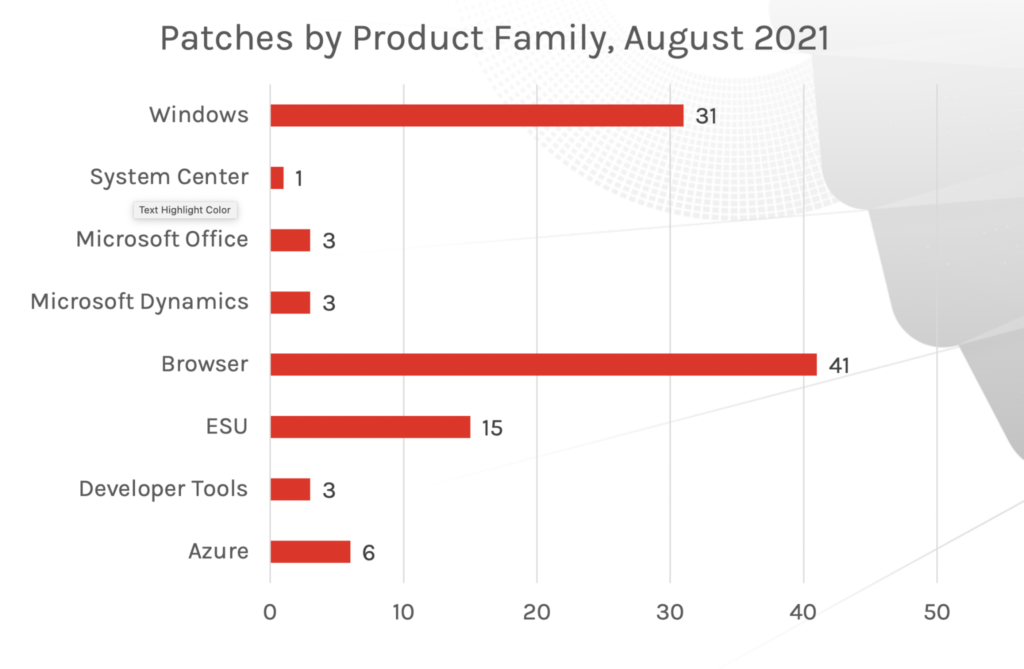 Figure 3: Patch updates by product family, August 2021
Figure 3: Patch updates by product family, August 2021
In-the-Wild Exploit for CVE-2021-36948
CVE-2021-36948 saw active exploitation prior to a patch update. This vulnerability is an elevation of privilege that takes advantage of Windows Update Medic Service (WaaSMedicSVC). Because of its exploitation status, it’s possible that CVE-2021-36948 is a variant of CVE-2020-17070, which was reported in November 2020.
These two vulnerabilities could indicate a possible increased risk on this service, if more variants of this vulnerability come out in the future. CrowdStrike recommends that organizations implement patches for environments running Windows 10, Server 2019 and later.
Other important vulnerabilities to consider:
Additional Resources
New Patches for 44 Vulnerabilities
This month’s Patch Tuesday update includes fixes for 44 vulnerabilities. As 2021 continues to unfold, we’ve seen critical vulnerabilities that have received patches and several vulnerabilities that have failed to receive a patch within the typical Patch Tuesday cadence. While this month’s release provides a relatively low quantity of patches, it's important to recognize both in- and out-of-band patches offered by Microsoft, as numerous vulnerabilities have been successfully exploited, and actors have been able to bypass some patching solutions offered in the Patch Tuesday updates, rendering them insufficient. When it comes to risk analysis, we see again, as with previous months, remote code execution and elevation of privilege as common attack types. Last month, we introduced a new graph, “Patches by Product Family,” and this month, Windows products and browsers are the two areas requiring the most patches (last month, Windows products and ESU took the lead for most patches required). What does this mean? If your organization heavily uses one of these Microsoft product areas, you might want to consider your patching policies and prioritize those that pose more risk. As we have stated before, the quantity of vulnerabilities may not necessarily indicate increased risk — but for the best defense, a thorough review of these products could prove to be useful for robust security defense. Figure 1. Breakdown of August’s Patch Tuesday attack impact
Figure 1. Breakdown of August’s Patch Tuesday attack impact Figure 2: Patch updates by product family, July 2021
Figure 2: Patch updates by product family, July 2021 Figure 3: Patch updates by product family, August 2021
Figure 3: Patch updates by product family, August 2021Critical Vulnerabilities
We see patches being rolled out for seven critical vulnerabilities (see table below) for this month. Here are a few that we recommend you patch at the earliest opportunity: CVE-2021-26424:CVE-2021-26424 is a remotely triggerable vulnerability in Windows TCP/IP in which a compromise can be leveraged from a Hyper-V guest virtual machine to host by sending malicious IPv6 ping packets. Patches have rolled out for all versions of Windows going back as far as Windows 7. Microsoft labels this as exploitation more likely, which means this could be low-hanging fruit for attackers. CVE-2021-26432: A critical vulnerability in the Window Services for NFS ONCRPC XDR Driver, CVE-2021-26432 appears to be particularly risky for organizations. This vulnerability does not require any privilege or user interaction and can be triggered remotely from the network. Updates have rolled out for Windows releases going back from Windows 8.1 and Server 2012. CVE-2021-34535:
The CVE-2021-34535 remote code execution vulnerability targets the remote desktop client. An attacker-controlled machine can leverage code execution in the victim machines that it connects to via remote desktop protocol. This can also affect the Hyper-V host when a victim uses the interface to access the attacker-controlled guest machine. This vulnerability was patched for Windows versions as old as Windows 7. CVE-2021-36936:
CVE-2021-36936, another remote code execution vulnerability, affects Windows Print Spooler. It was disclosed before this Patch Tuesday update, but according to Microsoft, it has not seen any active exploitation. Patches have rolled out for this vulnerability for versions as old as Windows 7. CVE-2021-34534:
This remote code execution vulnerability affects the MSHTML component in the browser engine. CVE-2021-34534 has only affected recent Windows 10 versions. To successfully exploit this vulnerability, an attacker would need to trick the user into browsing to a webpage. Other Critical vulnerabilities include remote code execution in Windows Graphics and a memory corruption in Scripting Engine for Internet Explorer.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.9 | CVE-2021-26424 | Windows TCP/IP Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2021-26432 | Windows Services for NFS ONCRPC XDR Driver Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2021-34535 | Remote Desktop Client Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2021-36936 | Windows Print Spooler Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-34530 | Windows Graphics Component Remote Code Execution Vulnerability |
| Critical | 6.8 | CVE-2021-34534 | Windows MSHTML Platform Remote Code Execution Vulnerability |
| Critical | 6.8 | CVE-2021-34480 | Scripting Engine Memory Corruption Vulnerability |
In-the-Wild Exploit for CVE-2021-36948
CVE-2021-36948 saw active exploitation prior to a patch update. This vulnerability is an elevation of privilege that takes advantage of Windows Update Medic Service (WaaSMedicSVC). Because of its exploitation status, it’s possible that CVE-2021-36948 is a variant of CVE-2020-17070, which was reported in November 2020.
These two vulnerabilities could indicate a possible increased risk on this service, if more variants of this vulnerability come out in the future. CrowdStrike recommends that organizations implement patches for environments running Windows 10, Server 2019 and later.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2021-36948 | Windows Update Medic Service Elevation of Privilege Vulnerability |
PetitPotam and CVE-2021-36942
Last month, a security researcher released a tool called PetitPotam to launch a classic attack type: NTLM relay. NTLM is an authentication protocol for Microsoft, and in this type of attack, the adversary intercepts authentication traffic between a client and server on a network. If successful, the adversary can exploit Windows Domain Controllers (DCs). Microsoft offered an advisory in July 2021 on attacks by the PetitPotam tool, acknowledging the issue and offering mitigation options. This month, a patch was released to further mitigate PetitPotam and CVE-2021-36942. When the patch is implemented, this Windows local security authority (LSA) spoofing vulnerability is blocked from the affected API call. Patches are available for Windows Server from 2008 and later.| Rank | CVSS Score | CVE | Description |
| Important | 7.5 | CVE-2021-36942 | Windows LSA Spoofing Vulnerability |
More on PrintNightmare and Print Spooler Vulnerabilities
As we have seen, vulnerabilities affecting Windows Print Spooler, especially those relating to the PrintNightmare situation, have created urgent and potentially dangerous openings for organizations relying on those services. In this month’s release, three updates have been offered for Windows Print Spooler: two for remote code execution and one for privilege elevation. For companies utilizing the Windows Print Spooler service, an in-depth review around these and other vulnerabilities relating to PrintNightmare would be prudent. For the latest on PrintNightmare, check out this piece by CrowdStrike’s threat intelligence team.| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2021-36947 | Windows Print Spooler Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2021-34481 | Windows Print Spooler Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-34483 | Windows Print Spooler Elevation of Privilege Vulnerability |
| Rank | CVSS Score | CVE | Description |
| Important | 8.1 | CVE-2021-34524 | Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-34478 | Microsoft Office Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-34486 | Windows Event Tracing Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-34536 | Storage Spaces Controller Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-34537 | Windows Bluetooth Driver Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-26425 | Windows Event Tracing Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-36937 | Windows Media MPEG-4 Video Decoder Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-36941 | Microsoft Word Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-36948 | Windows Update Medic Service Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-34471 | Microsoft Windows Defender Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-34533 | Windows Graphics Component Font Parsing Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-34484 | Windows User Profile Service Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-26431 | Windows Recovery Environment Agent Elevation of Privilege Vulnerability |
Be Proactive to Improve Security Posture
A proactive security posture will help organizations to minimize the exposure to vulnerabilities. CrowdStrike Falcon® Spotlight is a scanless solution that provides immediate visibility to help teams remediate vulnerabilities that are critical to your organization. CrowdStrike helps organizations prevent potential exploitation such as what users have been experiencing with CVE-2021-34481 and CVE-2021-36934 — especially useful when there is knowledge that an attack vector is present but the vendor has not yet provided a patch to secure the systems.Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Learn more on how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- See how Falcon Complete stops Microsoft exchange server zero-day exploits.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Read last month’s Patch Tuesday for more information on critical vulnerabilities your organization should prioritize.
- Learn about the recent Baron Samedit vulnerability and CrowdStrike’s custom dashboard.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)
































