The month of July 2021 has been particularly challenging for organizations relying on Microsoft products. Along with the ongoing PrintNightmare out-of-band patch bypass situation affecting Windows Print Spooler, attackers are targeting other Microsoft products, with Scripting Engine and Windows Kernel both seeing active exploitation. And, as mentioned in previous Patch Tuesday reports, companies continue to be plagued by numerous vulnerabilities affecting Microsoft’s DNS — a cornerstone product for most organizations. In this month’s Patch Tuesday release, Microsoft attempts to stem the vulnerabilities in these products, offering the greatest number of patches to date this year. We review these patches and offer recommendations on those that are most important to prioritize.
Let’s get started.
Three Microsoft Exchange Server Remote Code Execution Vulnerabilities Patched
This month, Microsoft patched a total of seven vulnerabilities within Microsoft Exchange Server. Three of those are remote code execution (RCE) vulnerabilities. CVE-2021-34473 has the highest CVSS ranking, coming in at 9.1.
Back in March 2021, CrowdStrike reported on a mass exploitation event surrounding Microsoft Exchange Server — a highly sophisticated adversary used multiple zero-day vulnerabilities to create a massive campaign. Given the recent attention to Exchange Server from threat actors, along with the severity of the vulnerabilities, we strongly recommend accelerating the patching of these Exchange Server hosts.
Also, Microsoft has now provided a patch for CVE-2021-31206, another RCE vulnerability uncovered during the Pwn2Own hacking contest.
Analyzing DNS Server Vulnerabilities
Windows DNS Server has seen the largest amount of update activity in July, with 13 vulnerabilities being patched for this module this month alone. While none of these vulnerabilities have seen in-the-wild exploitation, organizations should review these vulnerabilities and consider their prioritization in their current patching strategy.
Additional Resources
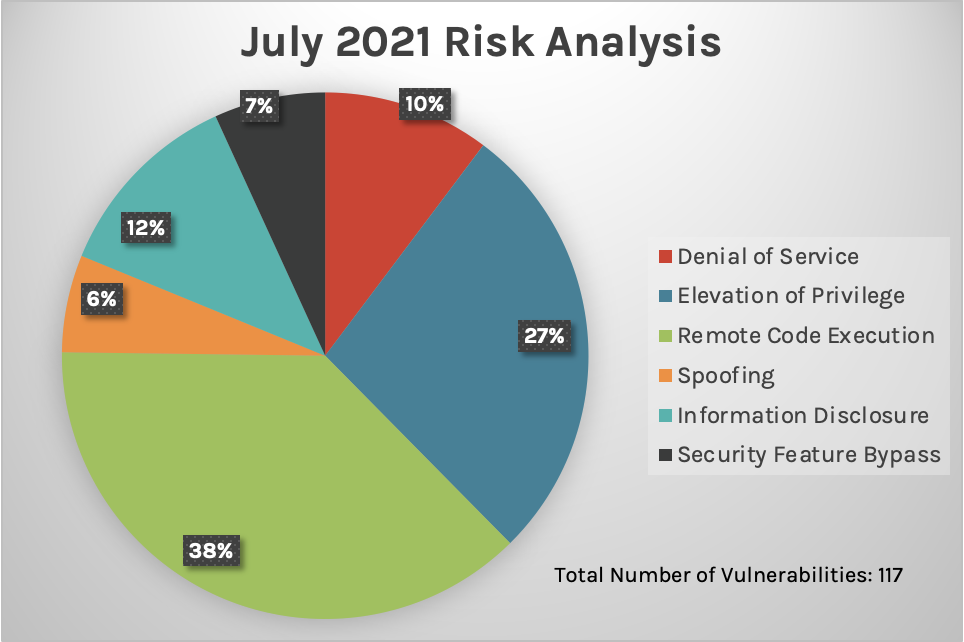
New Patches for 117 Vulnerabilities
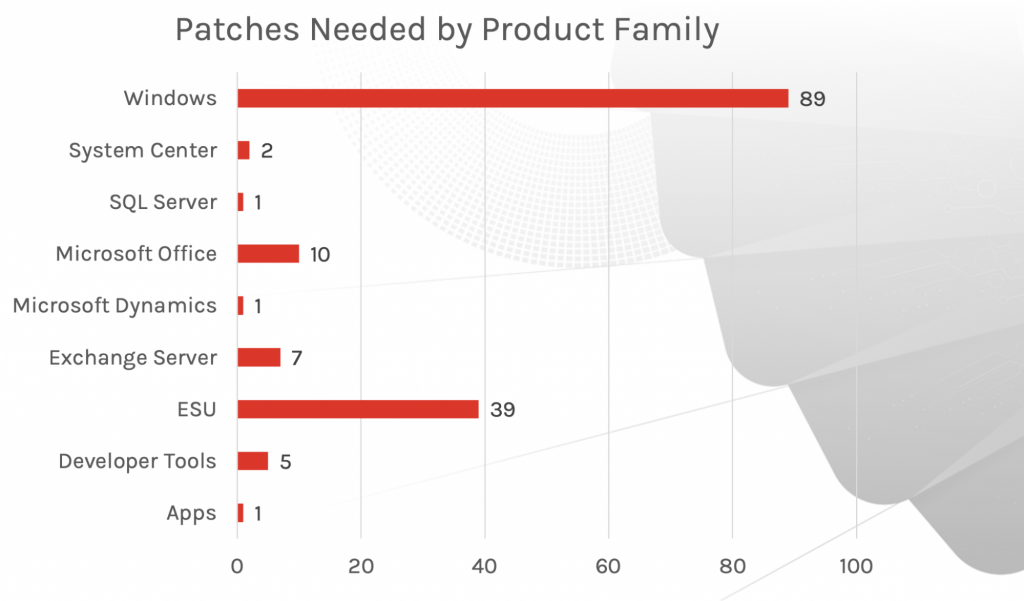
This month’s Patch Tuesday updates include fixes for 117 vulnerabilities. As we’ve seen the story unfold in the days before July’s release, Microsoft has rushed to address CVE-2021-34527 (referenced as PrintNightmare) with public exploits that affect almost all Windows versions. June’s Patch Tuesday update covered this CVE; however, it was considered incomplete. As a result, additional patches have been released, and the data surrounding these patches has been included in this month’s update. (Please note that PrintNightmare is still a developing situation.) We also see fixes for numerous products, with remote code execution (RCE) vulnerabilities continuing to lead for patching coverage, as was the case in June’s update. These fixes cover products for Microsoft Exchange Server, DNS and SharePoint.SecOps teams will have to patch workstations and servers to address these vulnerabilities, paying particular attention to Microsoft Exchange Servers and those that run DNS Services.


Critical Vulnerabilities
The CVE with the highest score in this month’s release is a remote code execution (RCE) vulnerability in the Windows kernel. CVE-2021-34458 has been given a CVSS score of 9.9, followed by multiple RCE vulnerabilities affecting Microsoft Exchange (CVE-2021-34473), Windows DNS Server (CVE-2021-34494) among others (see chart below). CVE-2021-34458 An attacker can utilize CVE-2021-34458A — a vulnerability that only affects Windows Server installations 2016 and newer —with a guest virtual machine by leveraging a compromise in the host kernel or other guests’ kernel. CVE-2021-34522 and CVE-2021-34464 Two RCE vulnerabilities, CVE-2021-34522 and CVE-2021-34464, have similar ratings and affect Microsoft Defender. No updates have been released for these vulnerabilities. However, if updates are appropriately configured, patches will be downloaded and installed automatically. CVE-2021-34448 According to Microsoft, this remote code execution vulnerability has seen in-the-wild exploitation. CVE-2021-34448 is a memory corruption vulnerability that affects Microsoft’s scripting engine.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.9 | CVE-2021-34458 | Windows Kernel Remote Code Execution Vulnerability |
| Critical | 9.1 | CVE-2021-34473 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2021-34527 | Windows Print Spooler Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2021-34494 | Windows DNS Server Remote Code Execution Vulnerability |
| Critical | 8.5 | CVE-2021-34450 | Windows Hyper-V Remote Code Execution Vulnerability |
| Critical | 8 | CVE-2021-34474 | Dynamics Business Central Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-34522 | Microsoft Defender Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-34464 | Microsoft Defender Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-34503 | Microsoft Windows Media Foundation Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-34439 | Microsoft Windows Media Foundation Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-33740 | Windows Media Remote Code Execution Vulnerability |
| Critical | 6.8 | CVE-2021-34448 | Scripting Engine Memory Corruption Vulnerability |
| Critical | 6.8 | CVE-2021-34497 | Windows MSHTML Platform Remote Code Execution Vulnerability |
Important Vulnerabilities, Including an In-the-Wild Windows Kernel Exploit
Microsoft reports having seen active exploitation of two Important vulnerabilities in the Windows kernel. As shown in the chart below, both have the same rating on the CVSS scale. While CVE-2021-31979 affects all Windows platforms dating as far back as Windows 7 and Server 2008 versions, CVE-2021-33771 only has updates for Windows 8.1 and newer. Although the updates for these vulnerabilities are ranked as “Important” instead of “Critical,” IT staff should prioritize them because of active exploitation.| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2021-33771 | Windows Kernel Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-31979 | Windows Kernel Elevation of Privilege Vulnerability |
Three Microsoft Exchange Server Remote Code Execution Vulnerabilities Patched
This month, Microsoft patched a total of seven vulnerabilities within Microsoft Exchange Server. Three of those are remote code execution (RCE) vulnerabilities. CVE-2021-34473 has the highest CVSS ranking, coming in at 9.1.
Back in March 2021, CrowdStrike reported on a mass exploitation event surrounding Microsoft Exchange Server — a highly sophisticated adversary used multiple zero-day vulnerabilities to create a massive campaign. Given the recent attention to Exchange Server from threat actors, along with the severity of the vulnerabilities, we strongly recommend accelerating the patching of these Exchange Server hosts.
Also, Microsoft has now provided a patch for CVE-2021-31206, another RCE vulnerability uncovered during the Pwn2Own hacking contest.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.1 | CVE-2021-34473 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Important | 9 | CVE-2021-34523 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| Important | 8 | CVE-2021-34470 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| Important | 8 | CVE-2021-33768 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| Important | 7.3 | CVE-2021-31206 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Important | 7.2 | CVE-2021-31196 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Important | 6.5 | CVE-2021-33766 | Microsoft Exchange Information Disclosure Vulnerability |
Analyzing DNS Server Vulnerabilities
Windows DNS Server has seen the largest amount of update activity in July, with 13 vulnerabilities being patched for this module this month alone. While none of these vulnerabilities have seen in-the-wild exploitation, organizations should review these vulnerabilities and consider their prioritization in their current patching strategy.
| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2021-34525 | Windows DNS Server Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2021-33756 | Windows DNS Snap-in Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2021-33752 | Windows DNS Snap-in Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2021-33750 | Windows DNS Snap-in Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2021-33749 | Windows DNS Snap-in Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2021-34494 | Windows DNS Server Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2021-33780 | Windows DNS Server Remote Code Execution Vulnerability |
| Important | 8 | CVE-2021-33754 | Windows DNS Server Remote Code Execution Vulnerability |
| Important | 8 | CVE-2021-33746 | Windows DNS Server Remote Code Execution Vulnerability |
| Important | 7.5 | CVE-2021-34442 | Windows DNS Server Denial of Service Vulnerability |
| Important | 6.5 | CVE-2021-33745 | Windows DNS Server Denial of Service Vulnerability |
| Important | 6.5 | CVE-2021-34499 | Windows DNS Server Denial of Service Vulnerability |
| Important | 6.5 | CVE-2021-34444 | Windows DNS Server Denial of Service Vulnerability |
Noting Active Directory Vulnerabilities
Two security feature bypass vulnerabilities occur in Active Directory. Although Microsoft has shared information that the likelihood of exploitation of these vulnerabilities (CVE-2021-33781 and CVE-2021-33779) is low, we recommend considering prioritizing this set. If exploitation were to occur, organizations using Active Directory could see a potential high negative impact.| Rank | CVSS Score | CVE | Description |
| Important | 8.1 | CVE-2021-33781 | Active Directory Security Feature Bypass Vulnerability |
| Important | 8.1 | CVE-2021-33779 | Active Directory Security Feature Bypass Vulnerability |
Patch Tuesday Is Important — But Consider All Microsoft Vulnerability Activity
With all of the OOB patches and ongoing updates occurring around Microsoft products, IT staff should take full advantage of their vulnerability management and patching solutions. Active exploits, patching failures and a steady stream of vulnerabilities affecting key Microsoft products could result in access for those attempting to breach an organization. While Patch Tuesday research blogs, such as this one, may help IT staff quickly consider which patches to prioritize immediately, using a solution such as CrowdStrike Falcon® Spotlight will provide ongoing visibility for an organization’s security posture. Falcon Spotlight is an intuitive, scanless solution providing immediate visibility to help your team organize, prioritize and remediate vulnerabilities that are critical to your organization.Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Learn more on how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- See how Falcon Complete stops Microsoft exchange server zero-day exploits.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Read last month’s Patch Tuesday for more information on critical vulnerabilities your organization should prioritize.
- Learn about the recent Baron Samedit vulnerability and CrowdStrike’s custom dashboard.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)
































