- Sandbox Scryer is an open-source tool for producing threat hunting and intelligence data from public sandbox detonation output
- The tool leverages the MITRE ATT&CK Framework to organize and prioritize findings, assisting in assembling indicators of compromise (IOCs), understanding attack movement and hunting threats
- By allowing researchers to send thousands of samples to a sandbox for building a profile for use with the ATT&CK technique, Sandbox Scryer can help solve use cases at scale
- The tool is intended for cybersecurity professionals who are interested in threat hunting and attack analysis leveraging sandbox output data
- Sandbox Scryer consumes output from the free and public Hybrid Analysis malware analysis service to help analysts expedite and scale threat hunting as part of security operations center (SOC) operations
Introducing Sandbox Scryer
Using the MITRE ATT&CK Framework to organize and prioritize its findings, the Sandbox Scryer tool leverages sandbox detonation output to provide key information, including observed MITRE ATT&CK techniques and associated metadata. It can do so at scale, allowing researchers to send hundreds or even thousands of files to a sandbox. Sandbox Scryer produces a layer file that can be imported into the ATT&CK Navigator for analysis (including graphical representation of techniques used), and provides a human-readable format for manual examination.Defending against advanced and sophisticated threats requires answering the question “What’s next?” after an initial detection. Understanding how threats behave and evolve enables defenders to improve defensive capabilities to identify and prevent future attack attempts and stages. Sandbox Scryer was initially developed to consume output from the free and public Hybrid Analysis malware analysis service that detects and analyzes unknown threats using a unique Hybrid Analysis technology. Designed to be extendable, Sandbox Scryer can also process output from other malware analysis services that offer sandbox detonation reports.
How Sandbox Scryer Helps to Make Sense of Threats Hidden in Sandbox Detonation Data
Threat behavior data coming from sandbox detonations can help provide the needed signal to inform focused answers to the question “What’s next?” Sandbox Scryer allows threat hunters to easily scale their investigations by sending a large number of samples to a sandbox at once and building a comprehensive profile that shows the tactics, techniques and procedures (TTPs) being used so protection gaps can quickly be identified, enhancing intelligence and threat hunting operations.Sandbox Scryer supports the prioritization of IOCs and ATT&CK behaviors and produces information that can easily integrate into SOC and security orchestration, automation and response (SOAR) operations at scale, improving defensive capabilities.
For example, having a heat map that visually depicts a technique such as the use of Remote Desktop Protocol (T1021.001) being shared across all samples submitted for analysis enables analysts to take immediate action and improve their defense posture by enabling identity protection mechanisms or additional policies.
For another example, consider that most endpoint detection and response (EDR) and extended detection and response (XDR) solutions support threat hunting by ATT&CK Techniques. Using Sandbox Scryer to combine multiple reports can reveal common techniques that can be included in a hunting package to search for similar threats in the enterprise. Sandbox Scryer helps organize and express the plethora of sandbox behavioral data so analysts can better understand and respond to attacks. Its primary output is a layer file analysts can import into the MITRE ATT&CK Navigator. This layer file collates data from the sandbox results using the set of sample submissions analyzed and includes metadata and a ranking of ATT&CK techniques. Besides being importable into the Navigator, the layer file is also a human-readable (JSON) format usable by itself for examining the collated data. In fact, it may be easier to examine details of the metadata noted in the layer file from techniques of interest than by viewing in the Navigator. In addition to generating the layer file, Sandbox Scryer creates custom output for each sandbox submission report analyzed. This output consists of:
- A graphical (.png) file showing observed MITRE ATT&CK techniques
- A text file for human consumption that includes observed techniques, metadata and a ranking of techniques
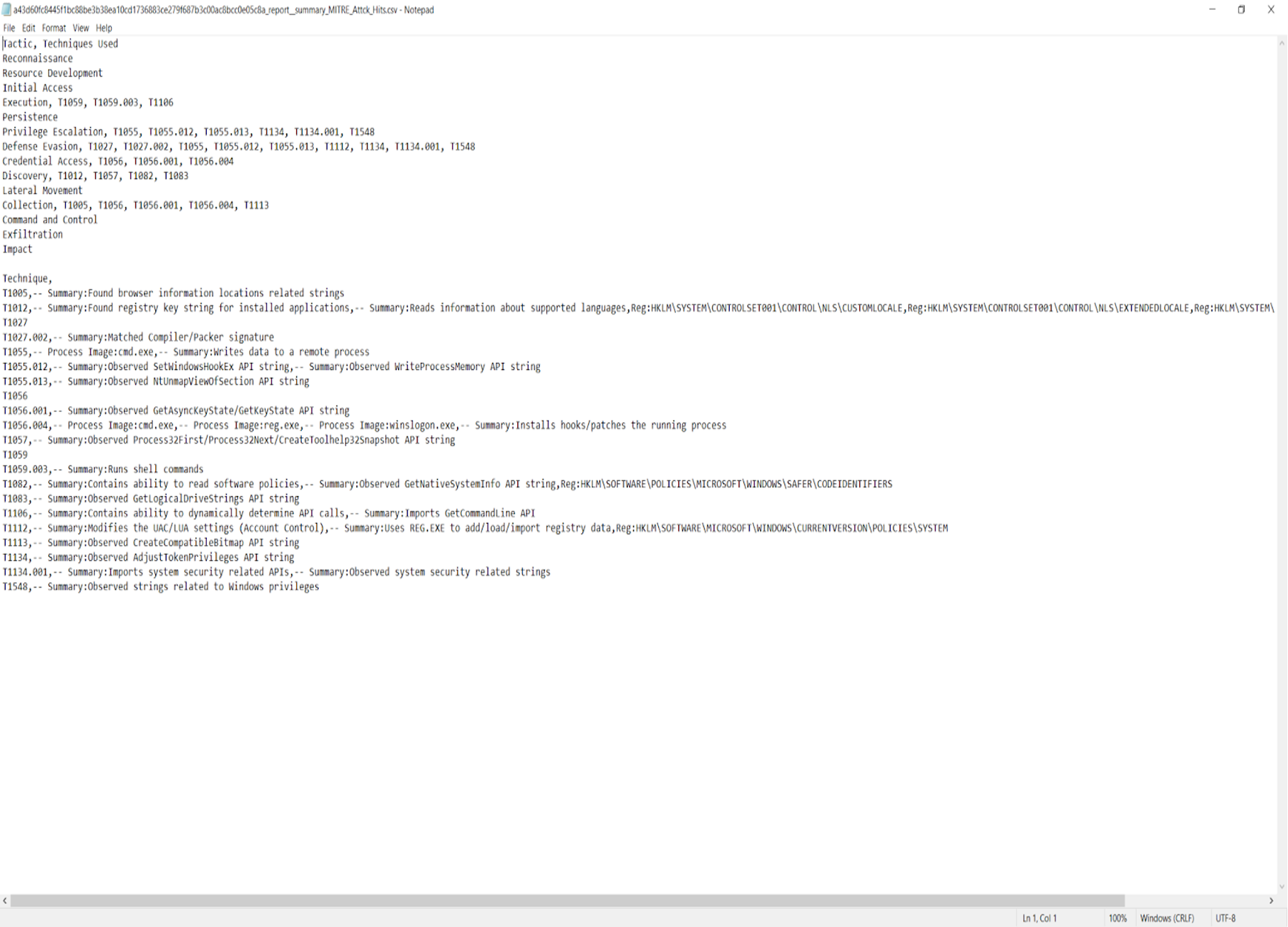
- A .csv file for import into collating tools that is used by Sandbox Scryer to assemble the collated data placed in the Navigator layer file
How to Use the Sandbox Scryer Tool
Figure 1 shows the major workflow steps for using Sandbox Scryer.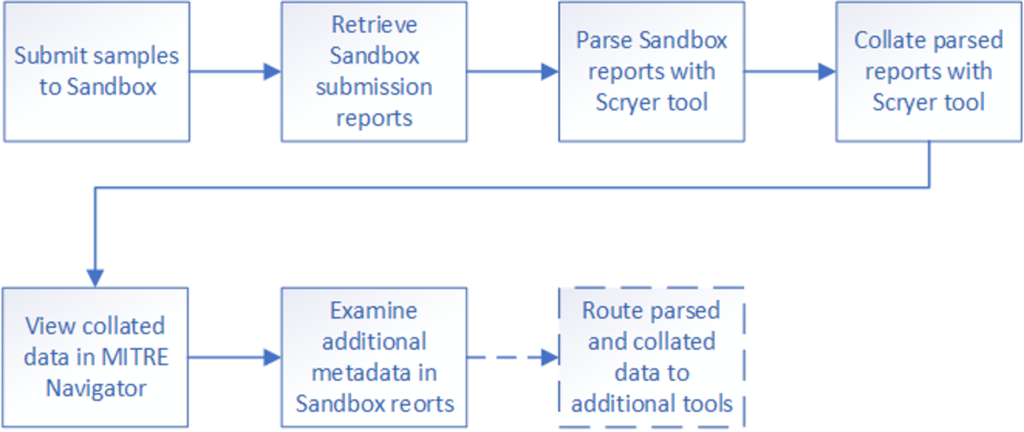 Figure 1. The Sandbox Scryer tool workflow
Figure 1. The Sandbox Scryer tool workflowStep 1. Submitting Samples
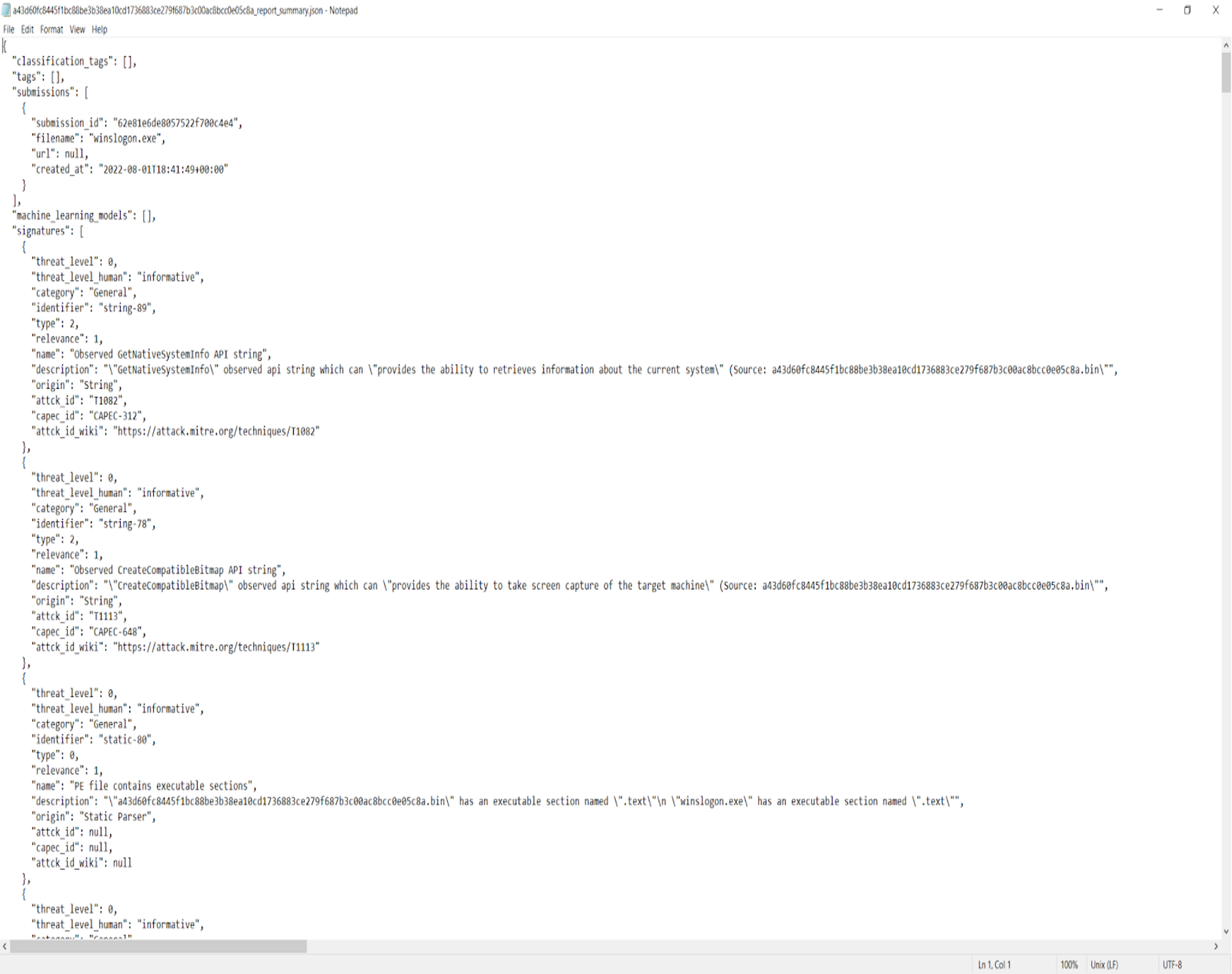
Usage begins with submitting a selected set of samples for detonation to the free Hybrid Analysis malware analysis service and then retrieving detonation results in the form of report summaries. This is done either using the Hybrid Analysis web user interface or through the documented and available endpoint API. The Sandbox Scryer tool retrieves the output (submission reports) using the endpoint API. The tool could be expanded to handle submitting samples and retrieving results directly, as a later enhancement. The report summary includes entries for sandbox signatures that triggered processing the submission. Metadata is included for each triggered signature and detected MITRE ATT&CK technique usage.Step 2. Retrieve Sandbox Report
Once the sandbox report summaries are retrieved for the submissions, the Sandbox Scryer tool is invoked for each report summary with theparse command specified via command-line arguments. This command will parse the report summary and extract the MITRE techniques from the detonation report, along with a subset of metadata for these techniques. It will produce a .csv file with this data, a corresponding human-readable format of the data and graphical representation of the techniques in the format of the MITRE ATT&CK Framework.
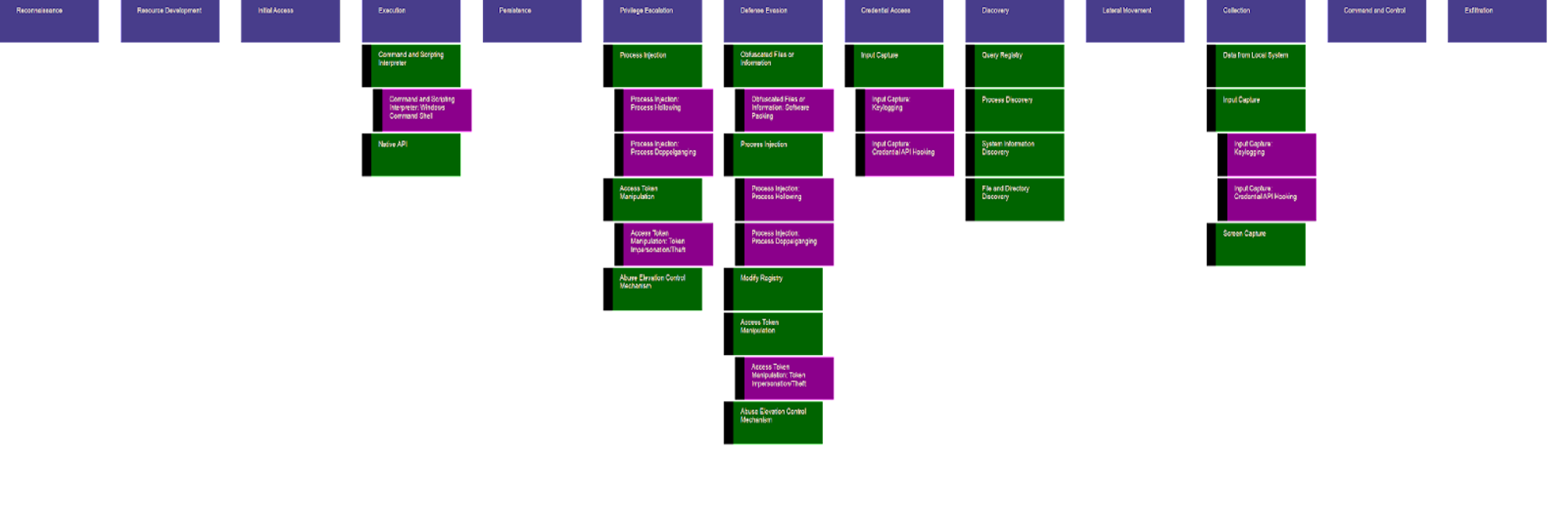 Figure 3. Individualized graphic showing MITRE techniques observed during the detonation for a specific sample (Click to enlarge)
Figure 3. Individualized graphic showing MITRE techniques observed during the detonation for a specific sample (Click to enlarge)collate command to collect the extracted MITRE data from each report summary and combine it into a layer file that can be imported into the MITRE Navigator.
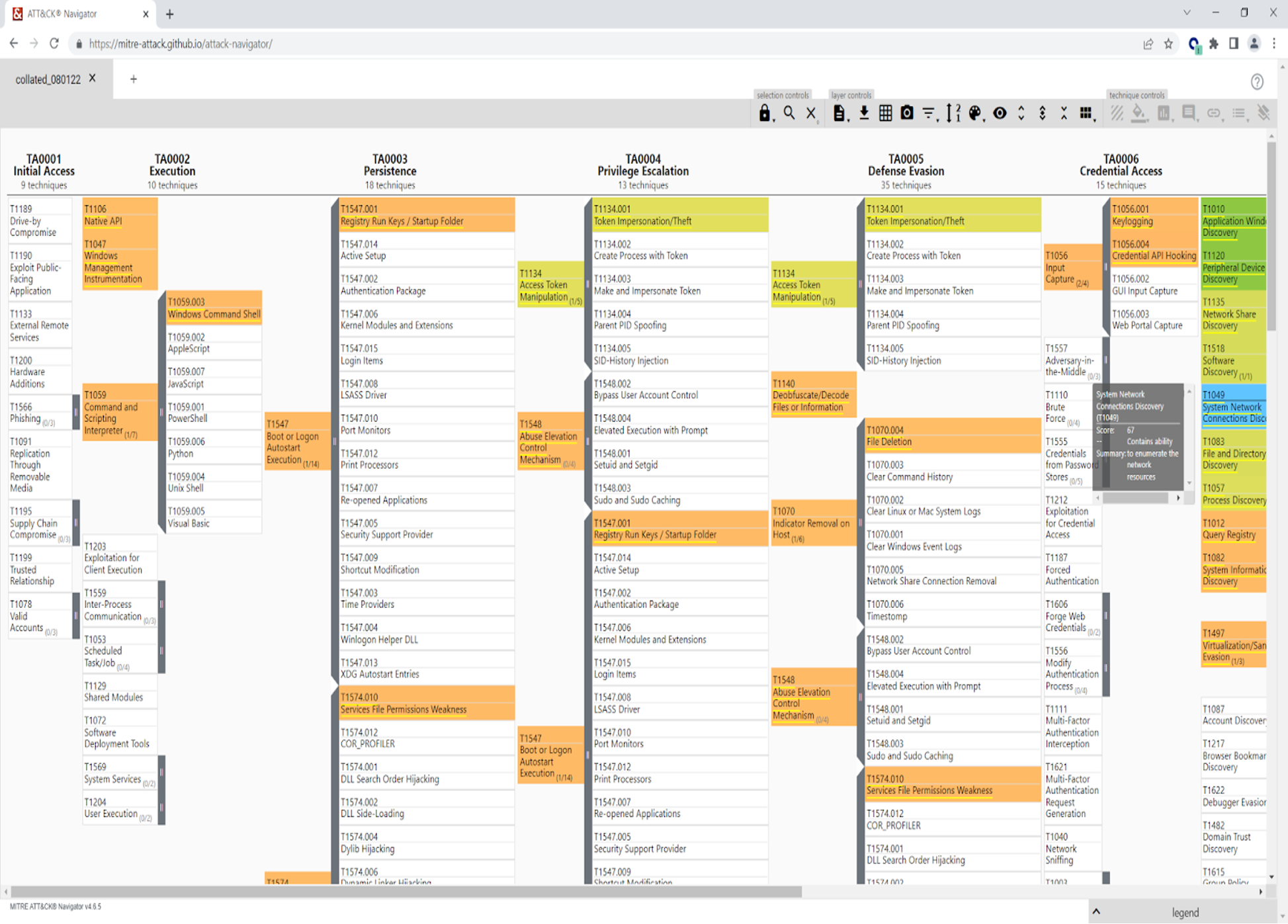
Following this, the MITRE ATT&CK Navigator may be launched to load the layer file and view the collated data.
The Navigator shows a view of the techniques and tactics observed by Sandbox Scryer while analyzing a set of submitted samples, with prevalence and prioritization shown via a heat map. This graphical view allows for easier human understanding of trends and priorities within the set of samples.
Hovering over techniques shows noted metadata such as the score used to generate the heatmap coloring, Windows Registry paths involved and more.
To analyze a particular technique more completely, an analyst would return to the sandbox report summaries and search for signature entries that note the MITRE technique, using grep or any similar tool.
The report summaries located within the search contain a complete set of metadata for the signature(s). This includes the technique (what is included in the Navigator view and other Scryer tool output is a subset of available metadata). More than one signature may note the technique. Additionally, other signatures triggered for the submission may be examined along with their metadata.
It’s worth noting that the output from the Sandbox Scryer tool can be sent to other tools for additional analysis.
A Free Tool to Advance Threat Hunting
The open-source Sandbox Scryer tool enables security professionals to understand threat attack movement by correlating behavior across multiple threats to understand and improve defenses where coverage gaps exist.
Cybersecurity professionals interested in threat hunting and attack analysis leveraging sandbox output data can grab the Sandbox Scryer tool from the GitHub repository and start using it as part of their toolset.
The repository contains additional details on how the tool operates, its source code, test data and corresponding output. Collaboration and feedback is welcome, so please see the tool for contact information on how to get in touch.
Additional Resources
- Register now to join us in Las Vegas, Sept. 19-21, for Fal.Con 2022, the cybersecurity industry’s most anticipated annual event!
- Check out CrowdStrike’s free Community Tools.
- Learn more about the industry-leading protection of the CrowdStrike Falcon® platform.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and see how true next-gen AV performs against today’s most sophisticated threats.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)