What is Shift Left Security?
Shift Left security embeds security into the earliest phases of the application development process. Vulnerable code is identified as it is developed rather than in the testing phase, which reduces costs and results in more secure apps.
App security and workload protection are growing concerns as organizations advance their digital transformations and place more of their assets in the cloud. The speed of software releases, the use of cloud-based services, the incorporation of automation into the software development process, and the rate of innovation in the development toolchain are all trends that erode app security.
Attackers and adversary actors are always looking for soft spots they can exploit to reach their payload. As organizations of all sizes have hardened their cybersecurity, hackers have turned their attention to leveraging vulnerable apps and workloads to achieve their goals. And now that “every company is a software company,” opportunities to exploit apps are plentiful.
Traditionally, code is subjected to security as the last phase before release. This creates a time crunch, as developers are usually working till the last minute, leaving the security team with little time to ensure the code is secure. When vulnerabilities are exposed, either the release is delayed or the development team has to scramble to correct each security issue while the security team has to scramble to check the revisions. This creates a great deal of expense and slows down application release and launches – and if iterations are released in haste, the chances of overlooking or under-prioritizing a vulnerability are significant. Application security is an essential part of the software development life cycle, and getting it right must be a top priority.
Organizations are seeking ways to make security a key aspect of the development process and give developers the ability to deliver secure, reliable solutions without having to become security experts themselves – and without putting the brakes on the application development process. Shift Left security helps them achieve this by significantly reducing the security concerns around cloud-native software and application development.
Benefits of Shift Left Security
Automation
Automated processes result in fewer human errors and fewer production issues. Test coverage is increased because multiple tests can be conducted at the same time, and testers are freed up to focus on other tasks.
Increased delivery speed
Shift Left security reduces the time between releases by enabling DevOps and security to work in parallel. Software quality is also improved because teams have time to identify and resolve issues as early as possible in the development process.
Secured application and development
Testing is one of the top reasons for release delays. Shift Left security supports faster application delivery because there is no pause in coding while security performs its reviews. Continuous testing means security flaws are caught sooner, so fixes are smaller in scale and less time-consuming. DevOps and security teams are saved from a lot of frustration and late nights, while new user-pleasing features are deployed faster.
Types of Shift Left Security Tools and Technologies
Shift Left security tools can be categorized into two types: security scanning tools and run-time protection tools. Security scanning tools are testing tools that streamline the integration of security with DevOps, and run-time protection tools are cybersecurity tools that protect an app during its execution.
Security Scanning Tools/ Image Assessment
Static Application Security Testing (SAST)
SAST is an application security methodology used to find vulnerabilities in an application. It is a “white box” method of testing, which means it tests the inner workings of an application, rather than its functionality. SAST represents the way a developer looks at code, rather than a hacker. A SAST tool analyzes source code without executing the application, so it can find vulnerabilities early in the software development life cycle. That makes fixes less expensive to implement. While SAST supports all types of software, it cannot discover run-time and environment-related issues because it scans static code only.
Software Composition Analysis (SCA)
SCA identifies open source code within a codebase. Open source licenses have limitations that are difficult to track manually. SCA automates the process of inspecting package managers, manifests, source code, binary files, container images, etc., and compiles its findings into a “bill of materials” (BOM), which in turn is compared to numerous databases to expose vulnerabilities, licensing issues, and code quality issues. The results enable security teams to rapidly identify critical security and legal vulnerabilities and prioritize them appropriately for mitigation.
Dynamic Application Security Testing (DAST)
DAST is a method of “black box” testing used in web application security that focuses finding vulnerabilities in a running app’s functionalities. DAST represents a hacker’s approach, as the tester has no visibility into the app’s inner workings. This form of testing finds vulnerabilities at the end of the software development life cycle. Because DAST dynamically analyzes a running application, it only supports web apps and services.
Runtime Protection Tools
Runtime Application Self-Protection (RASP)
RASP detects attacks on an application in real-time by analyzing the app’s behavior in context. It intercepts all calls from the app to a system and validates data requests from inside the app, effectively using the app itself to monitor its own behavior. RASP can be used on both web and non-web apps because its protective features operate on the app’s server and launch when the app is launched.
Web Application Firewalls (WAF)
WAFs filter, monitor, and block malicious traffic trying to enter an app and block unauthorized data from leaving the app. Their behavior is determined by sets of policies that help them distinguish malicious traffic from safe traffic, so their effectiveness is only as strong as the organization’s security policies. Because an enterprise may have thousands of WAFs and millions of policies, automation is key to ensuring all WAFs are up to date.
Bot Management
Bot management detects and prevents malicious bots from executing attacks like DDoS attacks on the application layer (L7), SQL injection, and credential stuffing through the use of solutions like block/allow lists, bot traps, and rate limiting. Caution is necessary, because overly-strict bot management can block legitimate web traffic and can also block bots built in-house for testing and automation purposes. Bot management is on track to overtake WAFs in the next few years, as bot attacks take on a new prominence in a digitally-transformed world.
Container Image and Serverless Function Scanning
Application development today uses containers to bundle an app’s source code with all of its dependencies in a single file. A container image is a file that is merged with the container file. The container image holds the app’s code, runtime, system tools, system libraries, and settings. Container image scanning analyzes the contents of a container and the build process of a container image to expose security issues and poor practices.
The need for serverless computing scanning is rising as most modern apps use some type of serverless computing to acquire functions that are too complicated or costly to be worth an in-house build. The use of these services, which are hosted on AWS, Azure, etc., requires the movement of data from the corporate infrastructure to the cloud services provider and elsewhere. Protecting that data in transit and at rest is the responsibility of the app’s owner – not the cloud services provider, which only secures its own infrastructure. Serverless function scanning requires a different type of monitoring and debugging than traditionally-hosted apps. Cloud-native solutions are the best choice for this purpose.
Workload Protection
Modern applications are distributed across the cloud infrastructure in containers, Kubernetes, and serverless architectures. These environments are always evolving. The addition of new services increases the attack surface, and visibility across such a complex, shifting ecosystem is hard to achieve.
Workload protection places security controls at the level of individual application workloads. It enables organizations to identify and remediate vulnerabilities across the application lifecycle, enforcing compliance and implementing security configuration and best practices across containers, kubernetes and any workload. A cloud workload protection solution should contain lateral movement, expose behavioral anomalies, track compliance, and reduce the attack surface.

The Complete Guide to CNAPPs
Download CrowdStrike's Complete Guide to CNAPPs to understand why Cloud-Native Application Protection Platforms are a critical component of modern cloud security strategies and how to best integrate them to development lifecycles.
Download NowBest Practices for Shifting Security Left
Build security into new application development
How far left should security be shifted? All the way. Security should be part of the development process from the first moment developers begin coding. Use APIs to integrate security into dev tool sets so security teams can find problems before code is pushed to the main branch.
Integrate application and container security into the DevOps toolchain
Shift Left app security starts with scans, but those scans aren’t helpful unless the results are available to the DevOps team. The power of shifting left is in providing the means for DevOps to work in tandem with security, so place those results in a web IDE and web pipeline report where developers can consume them. Automate the creation of a “software bill of materials” (SBOM) that compiles an inventory of all the dependencies in a project, and use container image scanning and serverless function scanning to expose known vulnerabilities that exist within a container image, project directory, or serverless service.
Combine scans to improve visibility and get prioritization right
Different scans serve different purposes. SAST and DAST complement each other and each is fundamental to app security. An organization using open source libraries, which is the norm, will also benefit from SCA. All scans should be integrated into multiple steps of the Continuous Integration/Continuous Delivery pipeline to block vulnerabilities before they can reach a registry. Run-time scans should be executed to protect the app from new Common Vulnerabilities and Exposures (CVEs).
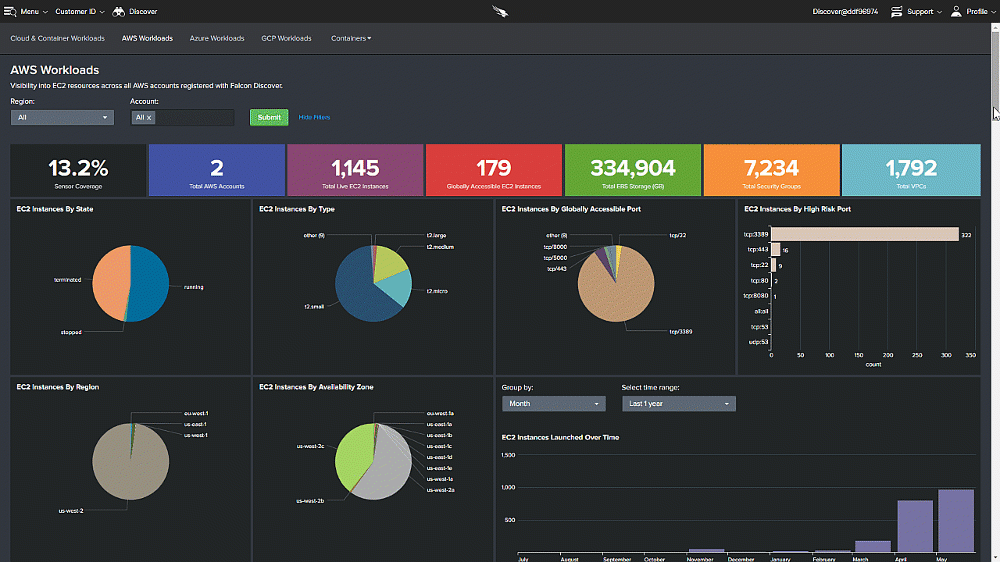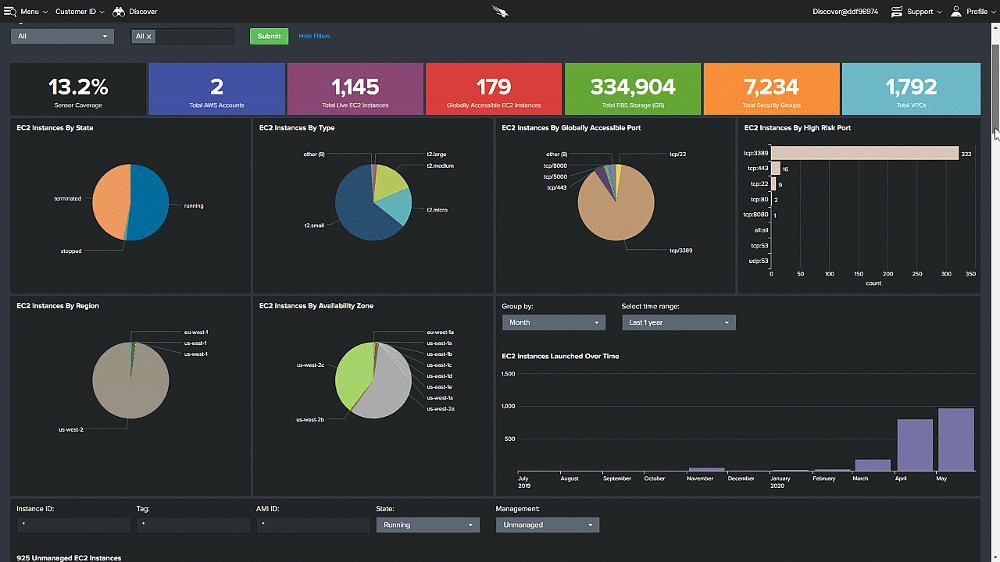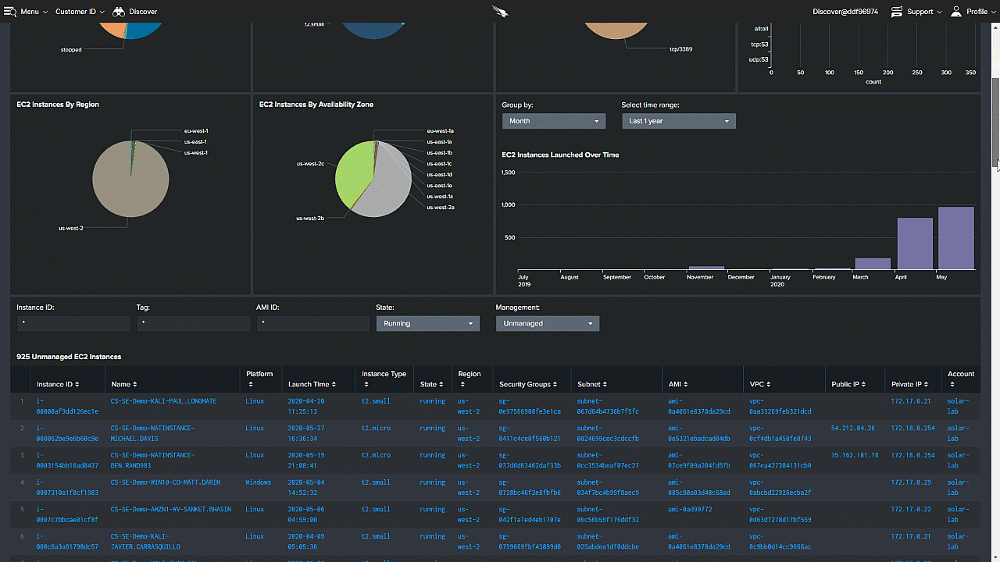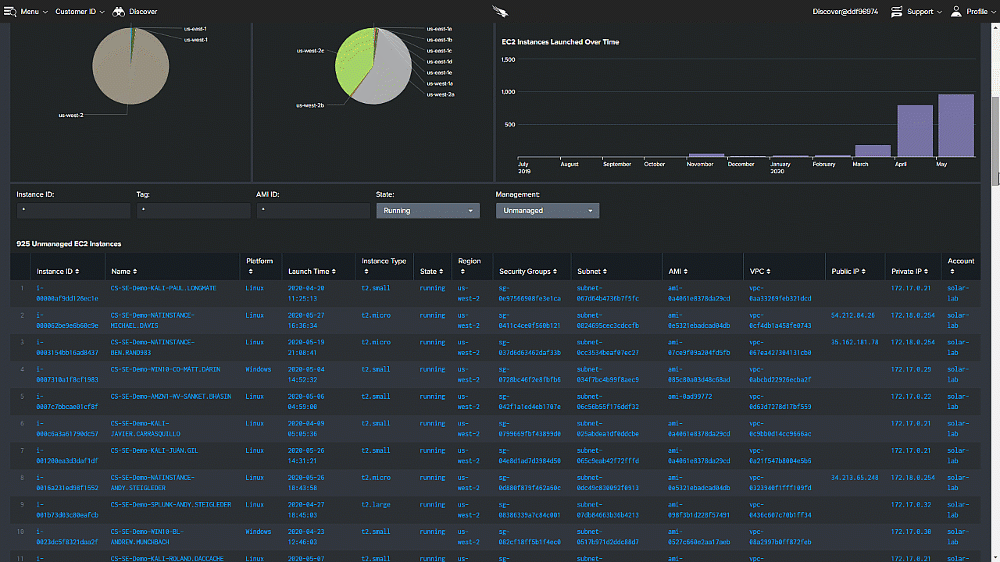
The CrowdStrike Approach
At CrowdStrike we stop breaches.
CrowdStrike has redefined security with the world’s most advanced cloud-native platform, protecting any workload in the cloud, preventing breaches and enabling organizations to build, run, and secure cloud-native applications.
CrowdStrike Falcon® Cloud Security automates security, detecting and stopping suspicious activity, zero-day attacks, and risky behavior on all of your clouds, containers, and Kubernetes applications. Integration with CI/CD workflows means that workloads can remain secure while DevOps works at speed without any performance hit.
Powered by the CrowdStrike Security Cloud, the CrowdStrike Falcon® Platform leverages real-time indicators of attack, threat intelligence, evolving adversary tradecraft and enriched telemetry from across the enterprise to deliver hyper-accurate detections, automated protection and remediation, elite threat hunting services, and prioritized observability of vulnerabilities.
We also offer fully-managed detection and response for cloud workloads, and our industry-leading Breach Prevention Warranty that covers up to $1 million in breach response expenses if there is a security incident within the environment protected by CrowdStrike Falcon® Complete.
Learn more about how Shift Left security can improve the security posture of your applications.



