Guest blogger Steve Chabinsky, former CrowdStrike General Counsel and Chief Risk Officer, now serves as Global Chair of the Data, Privacy and Cybersecurity practice at White & Case LLP.
For those not keeping track, the NIST Cybersecurity Framework received its first update on April 16, 2018. If you're already familiar with the original 2014 version, fear not. Everything you know and love about version 1.0 remains in 1.1, along with a few helpful additions and clarifications.
Among the most important clarifications, one in particular jumps out: If your company thought it complied with the old Framework and intends to comply with the new one, think again.
Your company hasn't been in compliance with the Framework, and it never will be. Why?
Click to learn more
Because NIST says so. According to NIST, although companies can comply with their own cybersecurity requirements, and they can use the Framework to determine and express those requirements, there is no such thing as complying with the Framework itself. In the words of NIST, saying otherwise is confusing. The Framework should instead be "used" and "leveraged." Which leads us to a second important clarification, this time concerning the Framework Core.
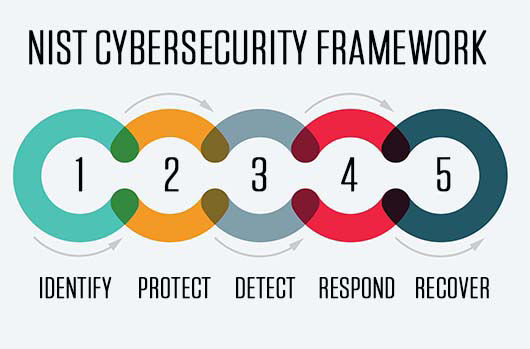
Perhaps you know the Core by its less illustrious name: "Appendix A." Regardless, the Core is a 20-page spreadsheet that lists five Functions (Identify, Protect, Detect, Respond, and Recover); dozens of cybersecurity categories and subcategories, including such classics as "anomalous activity is detected;" and, provides Informative References of common standards, guidelines, and practices. Practitioners tend to agree that the Core is an invaluable resource when used correctly. For NIST, proper use requires that companies view the Core as a collection of potential "outcomes" to achieve rather than a checklist of "actions" to perform. Expressed differently, the Core outlines the objectives a company may wish to pursue, while providing flexibility in terms of how, and even whether, to accomplish them. So, why are these particular clarifications worthy of mention? Simply put, because they demonstrate that NIST continues to hold firm to risk-based management principles. A company cannot merely hand the NIST Framework over to its security team and tell it to check the boxes and issue a certificate of compliance. Instead, to use NIST's words: "The Framework focuses on using business drivers to guide cybersecurity activities and considering cybersecurity risks as part of the organization's risk management processes." Wait, what?
That sentence is worth a second read. Its importance lies in the fact that NIST is not encouraging companies to achieve every Core outcome. Instead, organizations are expected to consider their business requirements and material risks, and then make reasonable and informed cybersecurity decisions using the Framework to help them identify and prioritize feasible and cost-effective improvements. Which leads us to discuss a particularly important addition to version 1.1. The new Framework now includes a section titled "Self-Assessing Cybersecurity Risk with the Framework." In fact, that’s the only entirely new section of the document. Companies are encouraged to perform internal or third-party assessments using the Framework. Leading this effort requires sufficient expertise in order to accurately inform an organization of its current cybersecurity risk profile, foster discussions that lead to an agreement on the desired or "target" profile, and drive the organization’s adoption and execution of a remediation plan to address material gaps between what the company has in place and what it needs. Of course, there are many other additions to the Framework (most prominently, a stronger focus on Supply Chain Risk Management). Still, despite its modifications, perhaps the most notable aspect of the revised Framework is how much has stayed the same and, as a result, how confident NIST has become in the Framework's value. After receiving four year's worth of positive feedback, NIST is firmly of the view that the Framework can be applied by most anyone, anywhere in the world. The following excerpt, taken from version 1.1 drives home the point: The Framework offers a flexible way to address cybersecurity, including cybersecurity’s effect on physical, cyber, and people dimensions. It is applicable to organizations relying on technology, whether their cybersecurity focus is primarily on information technology (IT), industrial control systems (ICS), cyber-physical systems (CPS), or connected devices more generally, including the Internet of Things (IoT). The Framework can assist organizations in addressing cybersecurity as it affects the privacy of customers, employees, and other parties. Additionally, the Framework’s outcomes serve as targets for workforce development and evolution activities. Yes, you read that last part right, “evolution activities.” To avoid corporate extinction in today’s data- and technology-driven landscape, a famous Jack Welch quote comes to mind: "Change before you have to." Considering its resounding adoption not only within the United States, but in other parts of the world, as well, the best time to incorporate the Framework and its revisions into your enterprise risk management program is now. Finally, if you need help assessing your cybersecurity posture and leveraging the Framework, reach out. As the old adage goes, you don't need to know everything. You just need to know where to find what you need when you need it.
Click to learn more
about CrowdStrike’s assessment, compliance and certification capabilities,
or download the report to see how CrowdStrike Falcon® can assist organizations in their compliance efforts with respect to National Institute of Standards and Technology (NIST).






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)