On March 22, the city of Atlanta, Georgia, was crippled by a ransomware attack that has since been identified as a SamSam (aka Samas and SamSa) ransomware variant — the work of a threat actor tracked by CrowdStrike Falcon® Intelligence™as BOSS SPIDER. The attack left 8,000 city employees without their computers, while IT staff worked to clean and restore them. Although some systems were restored relatively quickly, several days after the attack citizens were still unable to pay their water bills and parking tickets, and the police were having to manually write reports. According to an April 9 article in Homeland Security Today, “Atlanta’s recovery has been slow, and a vast amount of data may be unrecoverable.”
Falcon Intelligence previously reported that they had identified new samples of this ransomware — stating that the operators continue to distribute the threat at a steady pace and in a targeted manner. The samples they identified are all believed to have been used in successful infections based on the time-to-payment countdowns observed on the ransom payment sites.
A New Twist on Ransomware Attacks
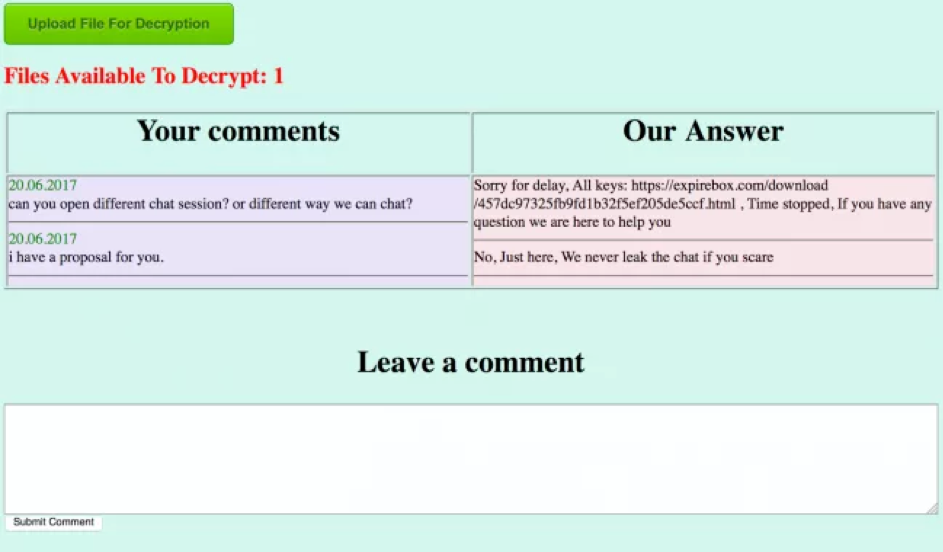
Unlike traditional malware-based ransomware attacks, SamSam breaks into the system as a targeted intrusion, with most of the attack actions being executed manually by the adversary. This is why this type of attack is so difficult to block with traditional antivirus prevention that is trained only to stop known malware. SamSam may seem like just another variant in a growing number of targeted, enterprise ransomware families. However, what makes it unique is how it uses unpatched software to reach its intended targets. SamSam attackers typically scan the web to find unpatched server-side software as their entrance into an environment. They then create a backdoor, giving them easy access to collect data and credentials and move laterally through the network. These steps are taken before encryption of the victim’s files begins. When they finally deploy their strain of SamSam, they use the compromised server to spread ransomware throughout the organization’s machines and network-based backups. The targeted nature of these attacks is likely providing more consistent and profitable results — as indicated by the higher than normal ransom requests that accompany them. In the case of Atlanta’s attackers, for example, the demand was for $51,000 in Bitcoin. These actors often gain a foothold within an organization’s network and then deploy ransomware to those areas of the environment most likely to yield results, targeting key servers and systems to limit the operations of the organization, increasing the pressure on victims to pay the ransom quickly. This seems to have been the case with the Atlanta attack. Once the victim pays, the attacker sends a response. The screenshot below shows an example of a typical response from the SamSam operators once a ransom demand has been paid. The response features a URL to download the victim’s decryption keys.
Best Practices for Preventing, Detecting and Responding to SamSam and Similar Attacks
CrowdStrike believes that attacks of this nature are highly likely to continue, as publicly successful incidents provide a powerful incentive for eCrime actors to continue their operations. It’s more important than ever for organizations to make cybersecurity a priority.Here are some critical areas that will help you avoid being victimized by SamSam or a similar threat:
- IT Hygiene: Basic IT hygiene practices must start with visibility across everything on your network, but legacy vulnerability scanning may not be enough to get an accurate assessment that clearly shows where you have security gaps. Many scanners rely on data extracted from the registry or other repositories, where minor inconsistencies in the patch installation process may cause the scan to report incorrect patch status. This leaves organizations with major blind spots that can turn into massive vulnerabilities.
- Be Proactive, Not Reactive: Relying solely on signature-based detection technology is no longer a viable strategy —
it won’t stop unknown malware and ransomware, nor will it prevent fileless attacks. First, organizations should arm themselves with next-gen antivirus (NGAV) that includes machine learning to detect unknown zero-day ransomware attacks, because today’s threats are designed to evade traditional endpoint security. In addition, while being able to detect indicators of compromise (IOCs) is important, they are only present after an incident has occurred. What’s needed are behavioral analysis capabilities with the ability to detect indicators of attack (IOAs). This can help you identify and block adversary behavior related to unknown variants of ransomware and protect against new categories of ransomware that don’t use files to encrypt systems. Another powerful weapon you should have in your arsenal is exploit blocking, to stop the execution and spread of ransomware via unpatched systems. - “Breakout Time” is Critical: Breakout time is another important metric that organizations should focus on as they prepare their defense against sophisticated attacks. Breakout time measures how long it takes for an intruder to escape the initial compromised machine and bury themselves deeper into your network. In the CrowdStrike 2018 Global Threat Report, it was estimated that the average breakout time is one hour and 58 minutes – meaning organizations must detect and remediate attacks within that time frame.
And breakout time is not the only window of opportunity organizations should heed. The most sophisticated organizations in the world strive to meet the following deadlines:
-
- Detect an intrusion within an average of one minute
- Investigate it in under 10 minutes
- Eject the adversary in under one hour






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)