How will your security team react when a sophisticated adversary has you in their sights? Will your team act in time to stop the breach?
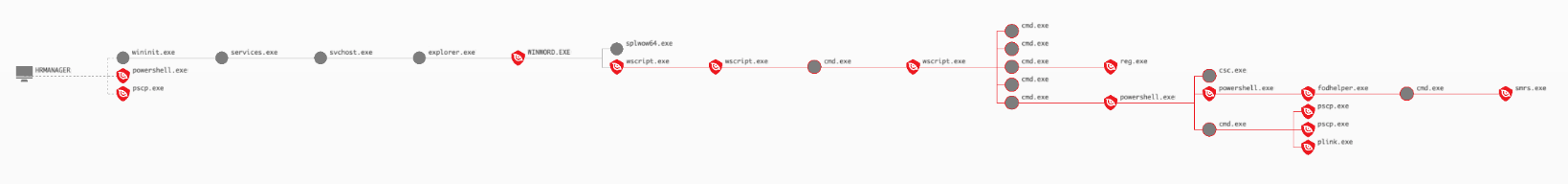
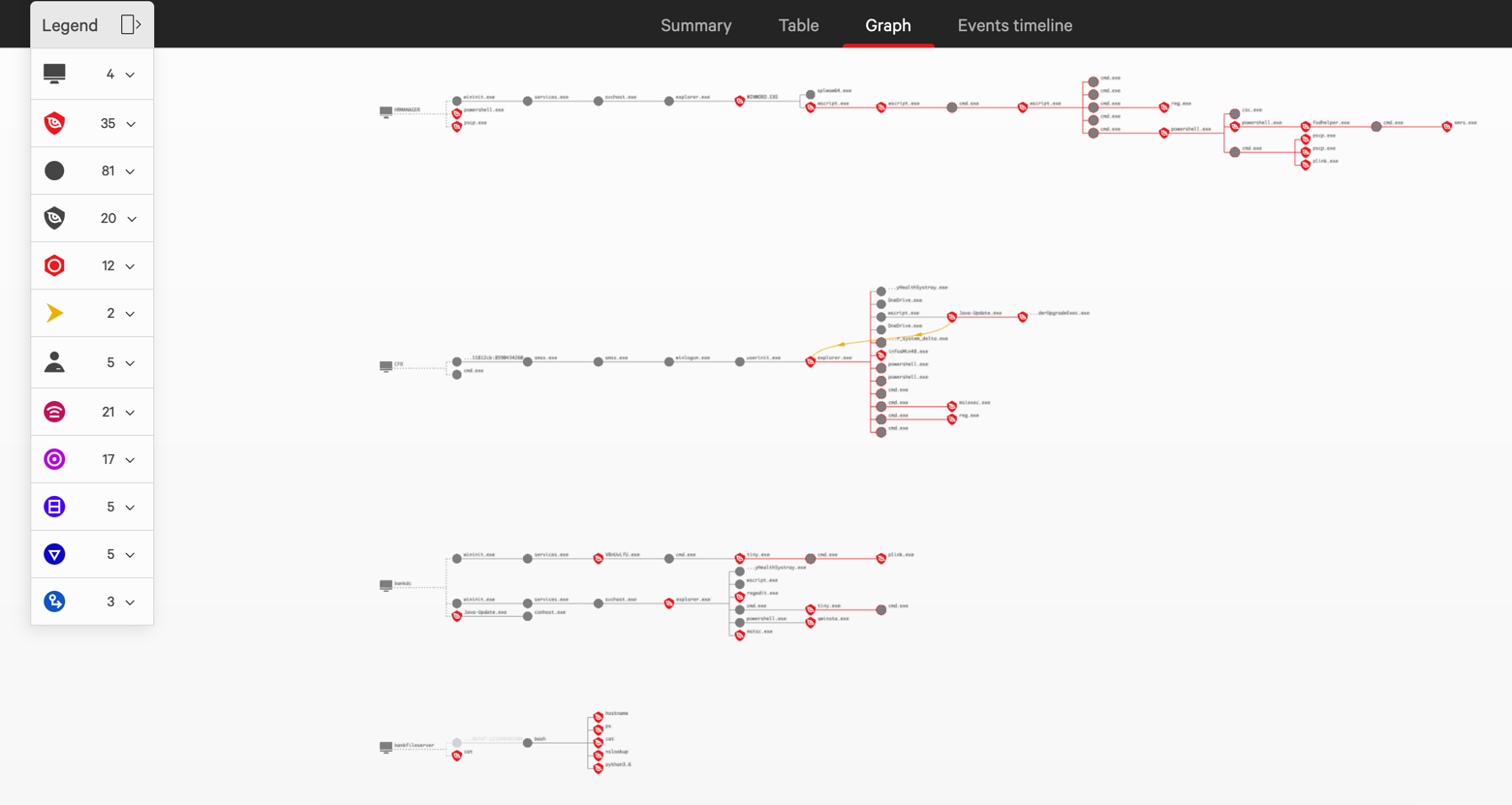
In last year’s MITRE Engenuity ATT&CK® Evaluation vs. COZY BEAR, we talked about the importance of the human element of detection and response. MITRE evaluations provide valuable insights for the cybersecurity community but also paint a static picture of a targeted intrusion, which can be a very fast-moving and chaotic situation. While technology is critical to enabling effective response, it does not account for the human factor.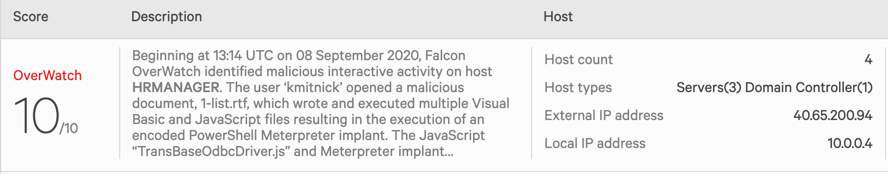 Figure 1. One OverWatch incident encompasses a highly sophisticated intrusion from beginning to end (Click to enlarge)
Let’s now walk through this intrusion step-by-step and see how the attack would have unfolded over time.
Figure 1. One OverWatch incident encompasses a highly sophisticated intrusion from beginning to end (Click to enlarge)
Let’s now walk through this intrusion step-by-step and see how the attack would have unfolded over time.
We have already shown how the CrowdStrike Falcon® platform provided comprehensive visibility into every stage of this year’s simulated attacks and effectively stopped the intrusion cold at multiple stages. In this blog, we’ll drill down further and explore how a world-class security team might deal with a sophisticated emerging eCrime threat as it happens. We’ll use one of MITRE’s simulated attacks to explore how the expert threat hunters of the CrowdStrike Falcon® OverWatch™ team provide the critical boost that security teams need to continuously stay ahead of sophisticated adversaries, leaving them with nowhere to hide.
Experts on the Falcon OverWatch team engage in continuous threat hunting across the Falcon platform, 24/7/365. They use their proprietary SEARCH methodology to uncover, reconstruct and communicate active intrusions to Falcon customers as they happen. OverWatch and similar managed services have been part of previous MITRE evaluations, but in this most recent evaluation, MITRE chose to focus solely on technology, and CrowdStrike Falcon® achieved extensive visibility without any assistance from the human threat hunters. Regardless, OverWatch is a core part of CrowdStrike’s solution set, and the team remained engaged throughout the evaluation process, providing continuous insights that we discuss below. Since this test was a known attacker using established tradecraft, threat hunting wasn’t critical to gaining visibility. However, in the real world, having an elite team of experts on your side can make a huge difference in speeding the time it takes to mount an effective response. For an in-depth discussion of the Round 3 MITRE ATT&CK evaluation, join our experts in this CrowdCast.
Diving In
OverWatch communicates with customers primarily through the CrowdStrike Falcon® console. An active intrusion is captured via an incident report, with continuous updates as the attack progresses. In the case of MITRE’s simulated attack by Carbanak, a single OverWatch incident captures the full intrusion, from initial access, to pivoting across four different hosts, to final exfiltration and deployment of persistence. Figure 1. One OverWatch incident encompasses a highly sophisticated intrusion from beginning to end (Click to enlarge)
Figure 1. One OverWatch incident encompasses a highly sophisticated intrusion from beginning to end (Click to enlarge)The Intrusion Begins
We begin by taking a look at the first phase of the MITRE test intrusion, a simulated attack against a bank that kicks off with a humble phish. Drilling into the initial incident report, we are presented with a graph view of the intrusion, enriched with annotations, interpretation and guidance from the OverWatch team. Beginning at 13:14 UTC on September 8, 2020, Falcon OverWatch identified malicious interactive activity on host HRMANAGER. The user “kmitnick” opened a malicious document, 1-list.rtf, which wrote and executed multiple Visual Basic and JavaScript files, resulting in the execution of an encoded PowerShell Meterpreter implant. The JavaScript “TransBaseOdbcDriver.js” and Meterpreter implant communicated with IP address 192.168.0.4, which does not have Falcon installed.Additionally, the operator leveraged a “fodhelper” privilege escalation technique, transferred files to 10.0.0.7, and moved laterally to 10.0.0.7 (BANKFILESERVER). You may consider utilizing the “Network Contain” feature within the Falcon UI to isolate/contain the host HRMANAGER to limit further attack activity. Falcon OverWatch will continue to investigate and will report on any new findings. OverWatch also highly recommends resetting credentials for the account “kmitnick,” which is likely compromised. Within the first critical minutes of the attack, OverWatch has identified the initial breach activity, and neatly summarized the adversary’s actions so far, covering the initial breach, the execution of a Meterpreter payload and the first stage of lateral movement. The summary also includes information on immediate actions that defenders can take to help contain the intrusion. In a real-world scenario, defenders are provided with actionable options for addressing in-progress intrusions early, in the critical moments before the attacker has attained a secure foothold and done real damage. In most situations, this is where the story would end. The OverWatch notification gives defenders the key information and coaching they need, in near real-time, to take immediate and decisive action to disrupt the intrusion in its earliest stages. It also curates all of the relevant context to understand where the threat originated, and highlights indicators that defenders can use to identify future follow-on intrusions more quickly and effectively.
Playing Hopscotch
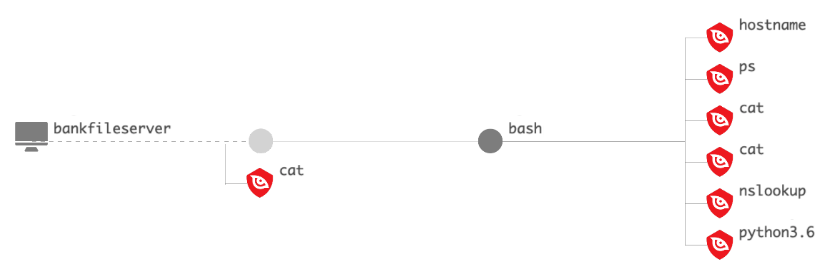
In this test, however, all prevention capabilities of the Falcon platform had been disabled, and no one intervened during the simulated intrusion in order to allow the full test to play out. As the intruder pivots to a Linux file server, the OverWatch team continues to closely monitor the intrusion and provide timely updates as the attacker advances. At 13:36 UTC on September 8, 2020, the operator laterally moved from HRMANAGER to the BANKFILESERVER host, leveraging the operator-placed plink utility. During this session, the operator inspected multiple XML and TXT files, and subsequently moved laterally to 10.0.0.4 (BANKDC) leveraging psexec.py. The PsExec session on BANKDC was used to launch tiny.exe, likely TinyMet based on the command line arguments, configured to communicate with 192.168.0.4. You may consider utilizing the “Network Contain” feature within the Falcon UI to isolate/contain the host BANKFILESERVER to limit further attack activity. Falcon Overwatch will continue to investigate and will report on any new findings. These continuous and timely updates ensure that your security team always remains aware of the current state of this hands-on-keyboard intrusion as it evolves.Approaching the Prize
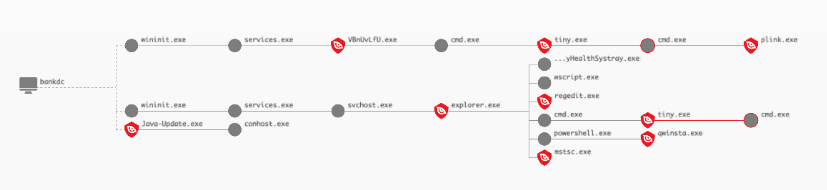
As our simulated adversary continues to march through the test environment, they move laterally to the organization’s Domain Controller, which provides them with the ideal staging grounds for the final phases of their attack. At 14:02 UTC on September 8, 2020, the operator initiated a type 10 interactive session on BANKDC with the “kmitnick” account.During this session, the actor placed, executed and established persistence for the Java-Update.exe implant also communicating with 192.168.0.4. Additionally, the operator launched the TinyMet implant and moved laterally to 10.0.0.5 (CFO) leveraging mstsc.exe. You may consider utilizing the “Network Contain” feature within the Falcon UI to isolate/contain the host BANKDC to limit further attack activity. Please ensure that it will not critically impact operations by isolating the host from your environment. Falcon Overwatch will continue to investigate and will report on any new findings.
Ringing the Bell
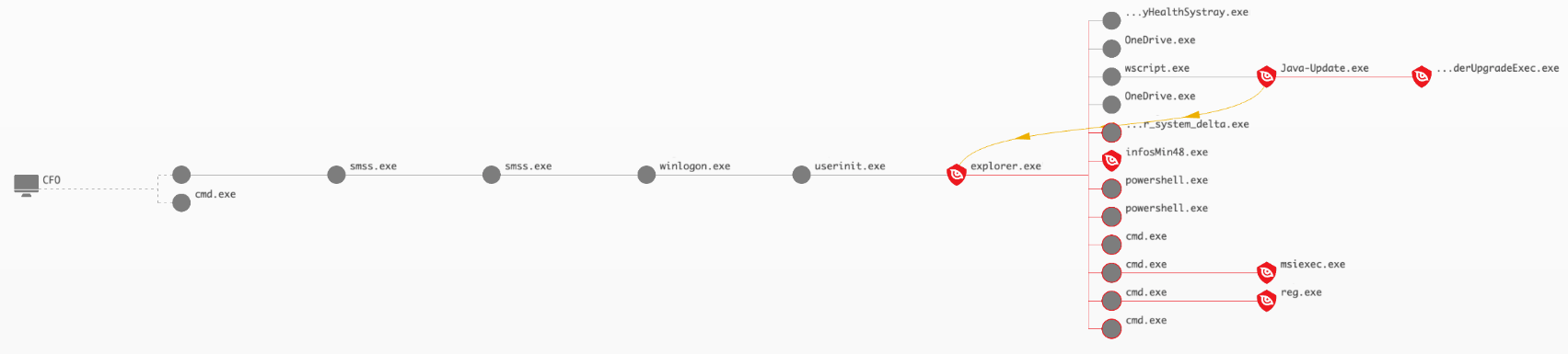
The adversary has now reached their goal by gaining access to the laptop belonging to the bank’s chief financial officer. OverWatch remains on the job and reports the results of these final stages. At 14:31 UTC on September 8, 2020, the operator initiated a type 10 interactive session on CFO with the “jsmith” account. During this session, the actor placed, executed and established persistence for the Java-Update.exe implant matching that was observed on BANKDC. The operator also wrote and executed the “infosMin48.exe” binary, installed a TightVNC client likely for continued access, and cleaned up their tools and registry persistence. You may consider utilizing the “Network Contain” feature within the Falcon UI to isolate/contain the host CFO to limit further attack activity. Further, OverWatch highly recommends resetting credentials for the likely compromised account “jsmith.” With that, our story ends. Over a period of approximately 90 minutes, this simulated attacker executed a stealthy hands-on intrusion featuring a wide range of advanced tradecraft, much of it focused on evading detection by security teams. They also left behind multiple implants and backdoors to allow them to return at will for days, weeks and months to come.Is Your Team Ready for the Race?
Visibility provides the pieces of the puzzle — your job as defender is to race to assemble the complete picture so you know what you’re up against and can act before the intrusion can become a major breach. Is your team prepared for the challenge? A typical security team takes an average of 11 hours to triage and investigate an emerging threat. By that time, the race is likely already lost to the adversary. The OverWatch team delivers clear understanding in minutes. The team’s experts provide the 24/7 vigilance and expertise needed to identify hidden, sophisticated threats in the earliest stages, and to quickly and completely understand the scope of the threat. OverWatch provides a turbo boost to your security team, ensuring you have the tools to win the race against your adversaries.Additional Resources
- Join this CrowdCast for an in-depth overview of MITRE’s Round 3 evaluation.
- Read about recent trends in adversaries’ TTPs in the CrowdStrike 2021 Global Threat Report.
- Learn about the powerful, cloud-native CrowdStrike Falcon® platform by visiting the product webpage.
- To find out how to incorporate intelligence on threat actors into your security strategy, visit the CROWDSTRIKE FALCON® INTELLIGENCE™ Threat Intelligence page.
- Get a full-featured free trial of CrowdStrike Falcon® Prevent™ and learn how true next-gen AV performs against today’s most sophisticated threats.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)