The year 2021 has required a lot of attention from cyber-savvy Microsoft users so far, considering the quantity and severity of vulnerabilities requiring updates and also the increased urgency to release updates for vulnerabilities that several threat actors have been actively exploiting.
This month is no different. For April’s Patch Tuesday, 108 vulnerabilities have received updates, and of those, 19 were flagged as critical, and at least one of them (CVE-2021-28310) has seen exploitation in the wild. This latest zero-day vulnerability has been reported by security vendors but is not currently attributed to a specific advanced persistent threat (APT) group.
Our April 2021 blog also covers a Kerberos Key Distribution Center (KDC) vulnerability, CVE-2020-17049, which is in the second phase of updates. In addition, we discuss updates for vulnerabilities within Win32k, SMB, TCP/IP and RPC. Other applications include Microsoft Exchange, Visual Studio Code, Microsoft Office and more.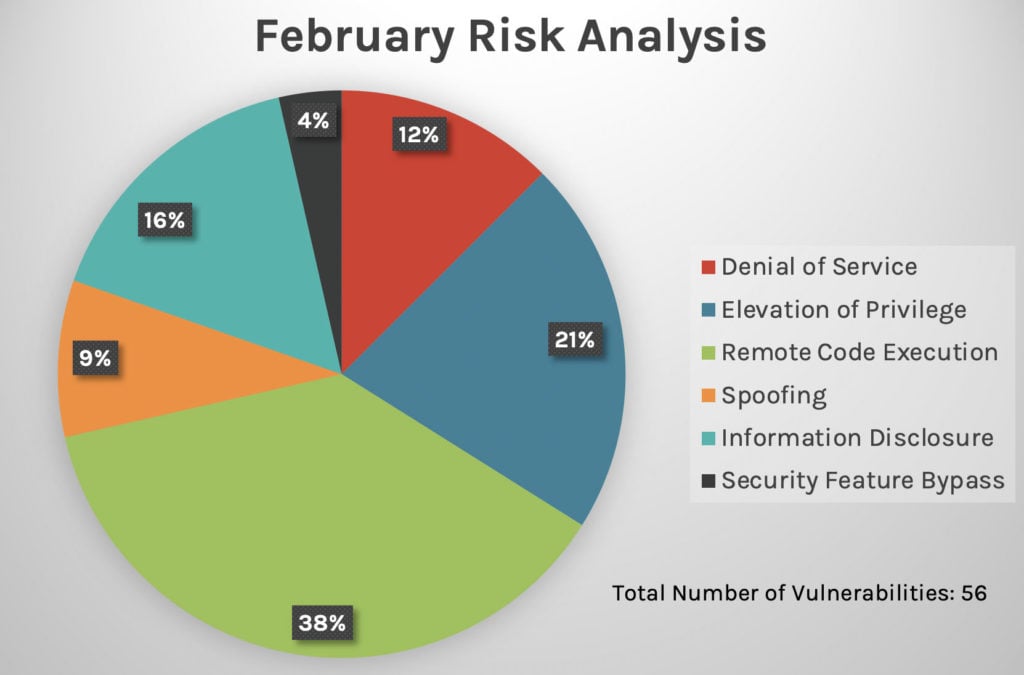 Figure 1. Risk analysis breakdown by vulnerability type, February 2021
Figure 1. Risk analysis breakdown by vulnerability type, February 2021
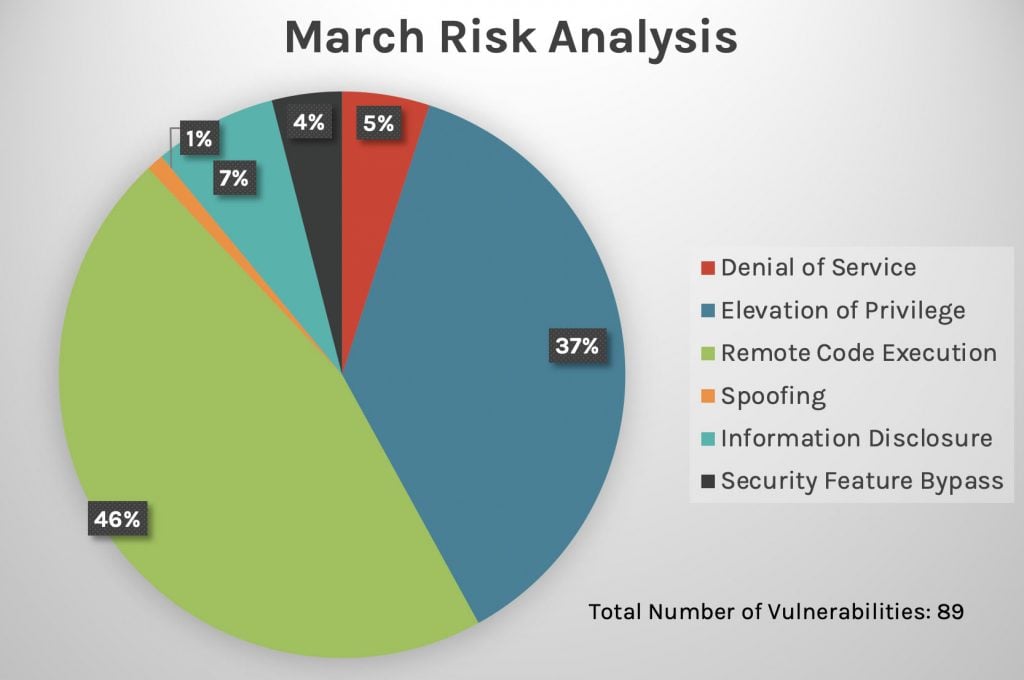 Figure 2. Risk analysis breakdown by vulnerability type, March 2021
Figure 2. Risk analysis breakdown by vulnerability type, March 2021
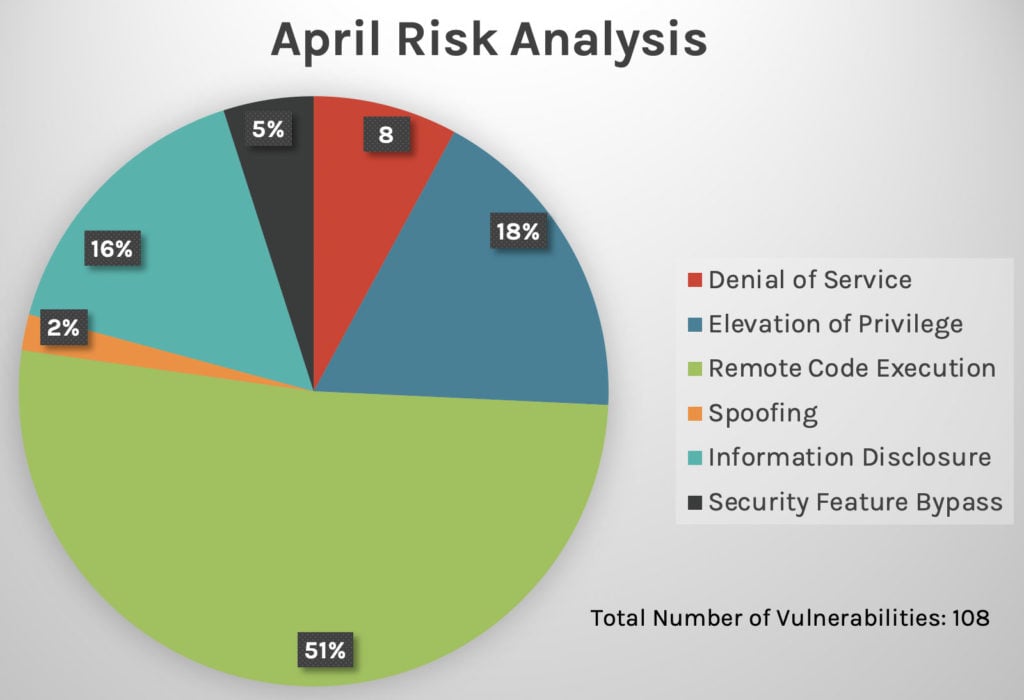 Figure 3. Risk analysis breakdown by vulnerability type, April 2021
Figure 3. Risk analysis breakdown by vulnerability type, April 2021
High-Ranking Vulnerabilities to Consider: Win32k Elevation of Privilege Vulnerability
CVE-2021-28310, an out-of-band (OOB) vulnerability found within a dynamic link library (DLL) that is part of Desktop Window Manager, has been confirmed to have active exploitation in the wild. Some sources speculate that the exploit may already be in use by multiple threat actors and is possibly being used by the BITTER APT group to target Pakistani nationals.
Note: An explanation of CVSS scores is included at the end of this blog.
Other important vulnerabilities to be aware of:
Let’s get started.
New Patches for 108 Vulnerabilities in April 2021
This year has seen a steady increase in the proportion of updates for remote code execution vulnerabilities — 51% in April vs. 38% in February and 46% in March. In the past three months, privilege elevation attack risks have also seen a large percentage of updates, as shown in Figures 1-3. See our February 2021 Patch Tuesday and March 2021 Patch Tuesday blogs for more analysis. Figure 1. Risk analysis breakdown by vulnerability type, February 2021
Figure 1. Risk analysis breakdown by vulnerability type, February 2021 Figure 2. Risk analysis breakdown by vulnerability type, March 2021
Figure 2. Risk analysis breakdown by vulnerability type, March 2021 Figure 3. Risk analysis breakdown by vulnerability type, April 2021
Figure 3. Risk analysis breakdown by vulnerability type, April 2021High-Ranking Vulnerabilities to Consider: Win32k Elevation of Privilege Vulnerability
CVE-2021-28310, an out-of-band (OOB) vulnerability found within a dynamic link library (DLL) that is part of Desktop Window Manager, has been confirmed to have active exploitation in the wild. Some sources speculate that the exploit may already be in use by multiple threat actors and is possibly being used by the BITTER APT group to target Pakistani nationals.Two new vulnerabilities affecting Win32k have been patched by Microsoft this month. These vulnerabilities affect the latest version of Microsoft Windows 10 20H2. Back in February, we saw another vulnerability affecting the same component, also being actively exploited.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2021-28310 | Win32k Elevation of Privilege Vulnerability |
| Important | 7 | CVE-2021-27072 | Win32k Elevation of Privilege Vulnerability |
Kerberos KDC Security Feature Bypass
CVE-2020-17049 is a type of security feature bypass vulnerability within Kerberos KDC. A compromised service configured to use KDC could be tampered with by a service ticket that is not valid for delegation in order to force KDC to accept it.It appears the release of this update removes the need to adjust the “PerformTicketSignature” setting to enable protection on Active Directory domain controller servers, as described in KB4598347. Support for Windows Server 2008 SP2 and Windows Server 2008 R2 has also been added.
There are three phases for patching this vulnerability: The first phase of updates occurred in November 2020, the second was released in this Patch Tuesday update, and the last phase — which will mandate Enforcement Mode, thereby permanently enabling protection — is scheduled to arrive in July 2021. Therefore, if you only have installed updates in November 2020 for KDC, you will need to continue the patching process as this service continues to be compromised by adversaries.
| Rank | CVSS Score | CVE | Description |
| Important | 6.6 | CVE-2020-17049 | Kerberos KDC Security Feature Bypass Vulnerability |
Microsoft Exchange: Four New Remote Code Execution Vulnerabilities
Following the list of vulnerabilities we revisited in Microsoft Exchange in March, four new remote code execution vulnerabilities for Microsoft Exchange have received patches this month.Fortunately, none of these vulnerabilities has seen exploitation. To protect against vulnerabilities such as these, CrowdStrike analysts have shared how Falcon Complete™ can stop exploits seeking to compromise Microsoft Exchange servers. The U.S. National Security Agency, which disclosed two of these vulnerabilities internally to Microsoft, urged organizations to apply updates as soon as possible, stating that exploiting these vulnerabilities could provide persistent access to and control of enterprise networks.
| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2021-28481 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2021-28480 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Critical | 9 | CVE-2021-28483 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2021-28482 | Microsoft Exchange Server Remote Code Execution Vulnerability |
Visual Studio and Visual Studio Code: Updates for Nine Remote Code Execution Vulnerabilities
This month, Microsoft Visual Studio Code received patches to update nine vulnerabilities, all of which could lead to remote code execution exploitation. Some of the vulnerabilities are present in plugins and tools, including those for integrating with GitHub, Maven and Kubernetes.| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2021-28473 | Remote Code Execution |
| Important | 7.8 | CVE-2021-28472 | Remote Code Execution |
| Important | 7.8 | CVE-2021-28471 | Remote Code Execution |
| Important | 7.8 | CVE-2021-28469 | Remote Code Execution |
| Important | 7.8 | CVE-2021-28448 | Remote Code Execution |
| Important | 7.8 | CVE-2021-28470 | Remote Code Execution |
| Important | 7 | CVE-2021-28477 | Remote Code Execution |
| Important | 7.8 | CVE-2021-28475 | Remote Code Execution |
| Important | 7.8 | CVE-2021-28457 | Remote Code Execution |
| Rank | CVSS Score | CVE | Description |
| Important | 8.1 | CVE-2021-28460 | Azure Sphere Unsigned Code Execution Vulnerability |
| Important | 8.1 | CVE-2021-28445 | Windows Network File System Remote Code Execution Vulnerability |
| Important | 7.8 | CVE-2021-28314 | Windows Hyper-V Elevation of Privilege Vulnerability |
| Important | 6.5 | CVE-2021-28442 | Windows TCP/IP Information Disclosure Vulnerability |
| Important | 6.5 | CVE-2021-28325 | Windows SMB Information Disclosure Vulnerability |
Further Recommendations
Besides critical and important vulnerabilities, Microsoft provided updates for more than 20 vulnerabilities affecting Microsoft Office, Excel, Word, SharePoint and other commonly used applications. These applications are often a target for attackers, as organizations typically rely on these applications for day-to-day business activities. Consider prioritizing updates for these applications if your business uses them. Read more about the specific applications affected here.Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Learn more on how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Read last month’s Patch Tuesday for more information on critical vulnerabilities your organization should prioritize.
- See how Falcon Complete stops Microsoft exchange server zero-day exploits.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)

































