Microsoft has released security updates for 60 vulnerabilities in its March 2024 Patch Tuesday rollout. There are two Critical vulnerabilities patched (CVE-2024-21407 and CVE-2024-21408), both of which affect the Hyper-V hypervisor.
Table 1. Critical vulnerabilities in Windows Hyper-V
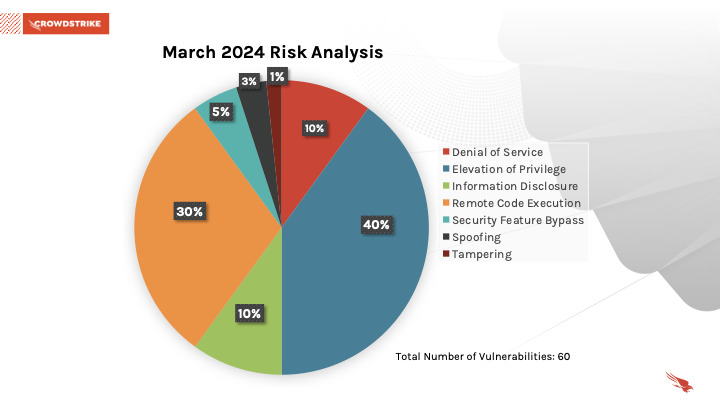
March 2024 Risk Analysis
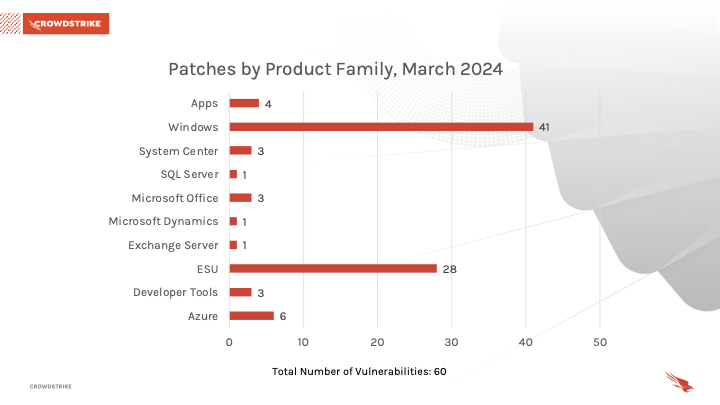
This month’s leading risk type is elevation of privilege (40%) followed by remote code execution (30%) and a tie between denial of service (10%) and information disclosure (10%).Windows products received the most patches this month with 41, followed by Extended Security Update (ESU) with 28 and Azure with 6.
Critical Vulnerabilities Affect Windows Hyper-V
CVE-2024-21407 is a Critical remote code execution (RCE) vulnerability affecting Microsoft Windows Hyper-V and has a CVSS score of 8.1. Successful exploitation of this vulnerability would allow the attacker to launch code execution on the host server from a Hyper-V guest. This vulnerability would require the attacker to be authenticated on a guest virtual machine and then send specially crafted operation requests aimed at the host. Successful exploitation requires a high level of attack complexity, but can result in code execution on the server and should be patched without delay. CVE-2024-21408 is a Critical denial of service (DoS) vulnerability affecting Microsoft Windows Hyper-V and has a CVSS score of 5.5. Successful exploitation of this vulnerability allows an attacker to target a Hyper-V guest virtual machine, which can affect the functionality of the Hyper-V host. Because this is a local DoS attack, Microsoft deems exploitation less likely.| Severity | CVSS Score | CVE | Description |
| Critical | 8.1 | CVE-2024-21407 | Windows Hyper-V Remote Code Execution Vulnerability |
| Critical | 5.5 | CVE-2024-21408 | Windows Hyper-V Denial of Service Vulnerability |
Not All Relevant Vulnerabilities Have Patches: Consider Mitigation Strategies
As we have learned with other notable vulnerabilities, such as Log4j, not every highly exploitable vulnerability can be easily patched. As is the case for the ProxyNotShell vulnerabilities, it’s critically important to develop a response plan for how to defend your environments when no patching protocol exists. Regular review of your patching strategy should still be a part of your program, but you should also look more holistically at your organization's methods for cybersecurity and improve your overall security posture. The CrowdStrike Falcon® platform regularly collects and analyzes trillions of endpoint events every day from millions of sensors deployed across 176 countries. Watch this demo to see the Falcon platform in action.Learn More
Learn more about how CrowdStrike Falcon® Exposure Management can help you quickly and easily discover and prioritize vulnerabilities and other types of exposures here.About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- For more information on which products are in Microsoft’s Extended Security Updates program, refer to the vendor guidance here.
- Read the CrowdStrike 2024 Global Threat Report
to learn how the threat landscape has shifted in the past year and understand the adversary behavior driving these shifts. - See how Falcon Exposure Management can help you discover and manage vulnerabilities and other exposures in your environments.
- Learn how CrowdStrike’s external attack surface module, CrowdStrike® Falcon Surface™, can discover unknown, exposed and vulnerable internet-facing assets, enabling security teams to stop adversaries in their tracks.
- Learn how CrowdStrike Falcon® Identity Protection products can stop workforce identity threats faster.
- Make prioritization painless and efficient. Watch how CrowdStrike Falcon® Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen antivirus for yourself with a free trial of CrowdStrike® Falcon Prevent™.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)