Microsoft has released 73 security patches for its May Patch Tuesday rollout. One of the 73 CVEs addressed, Windows LSA Spoofing Vulnerability CVE-2022-26925, is ranked as Important and is under active exploitation. In this blog, the CrowdStrike Falcon® Spotlight™ team offers an analysis on this month’s vulnerabilities, highlighting those that are most severe and recommending how to prioritize patching.
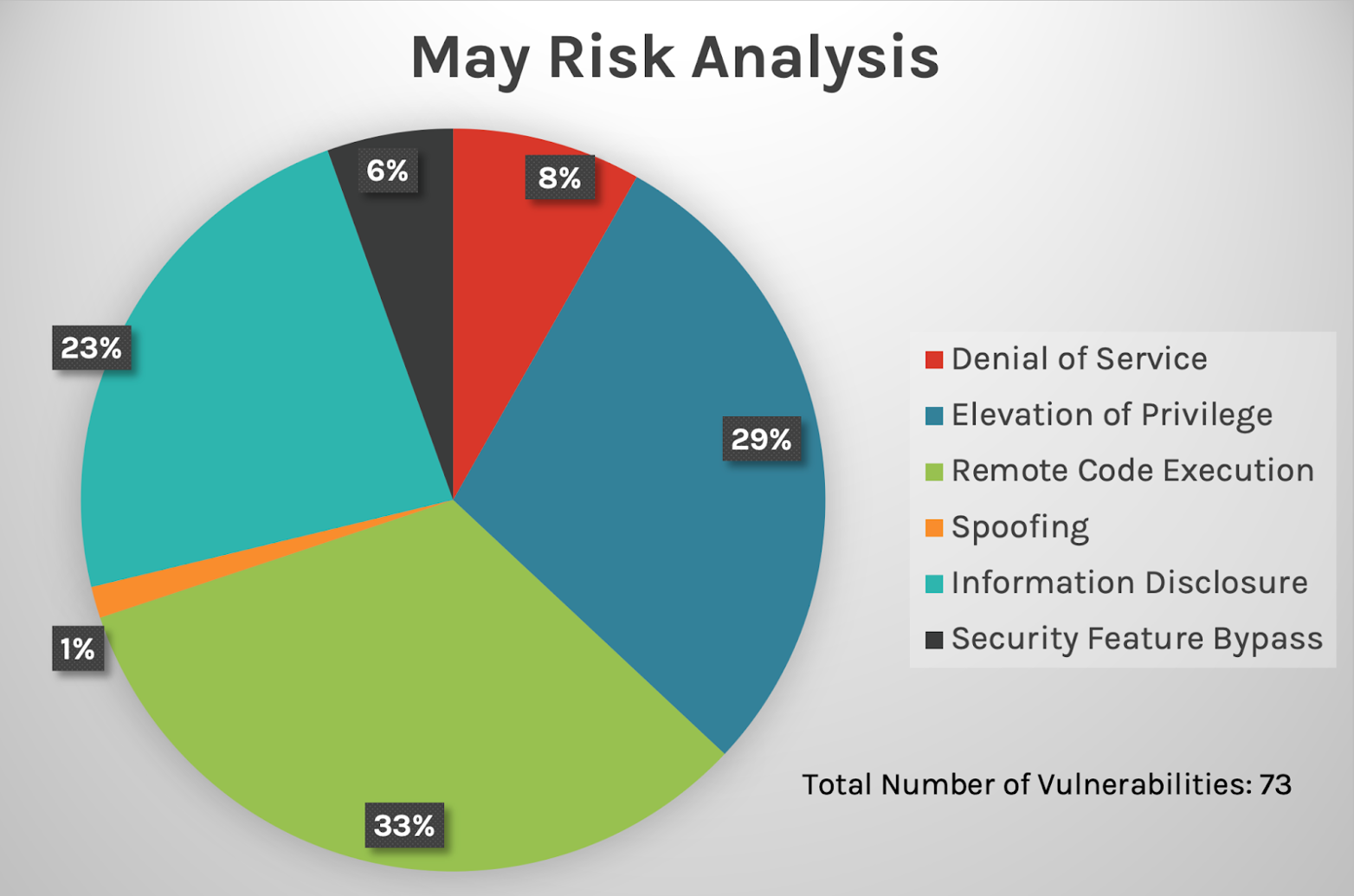 Figure 1. Breakdown of May 2022 Patch Tuesday attack types
The affected product families, however, differ greatly from last month. In May 2022, Developer Tools, including Visual Studio Code,Visual Studio 2019 and 2022, as well as Microsoft .NET Framework, saw a significant decrease in vulnerabilities patched. Microsoft Windows received the most patches this month, with Extended Security Updates following close behind. A single Microsoft Exchange update was also included in this month’s patching list.
Figure 1. Breakdown of May 2022 Patch Tuesday attack types
The affected product families, however, differ greatly from last month. In May 2022, Developer Tools, including Visual Studio Code,Visual Studio 2019 and 2022, as well as Microsoft .NET Framework, saw a significant decrease in vulnerabilities patched. Microsoft Windows received the most patches this month, with Extended Security Updates following close behind. A single Microsoft Exchange update was also included in this month’s patching list.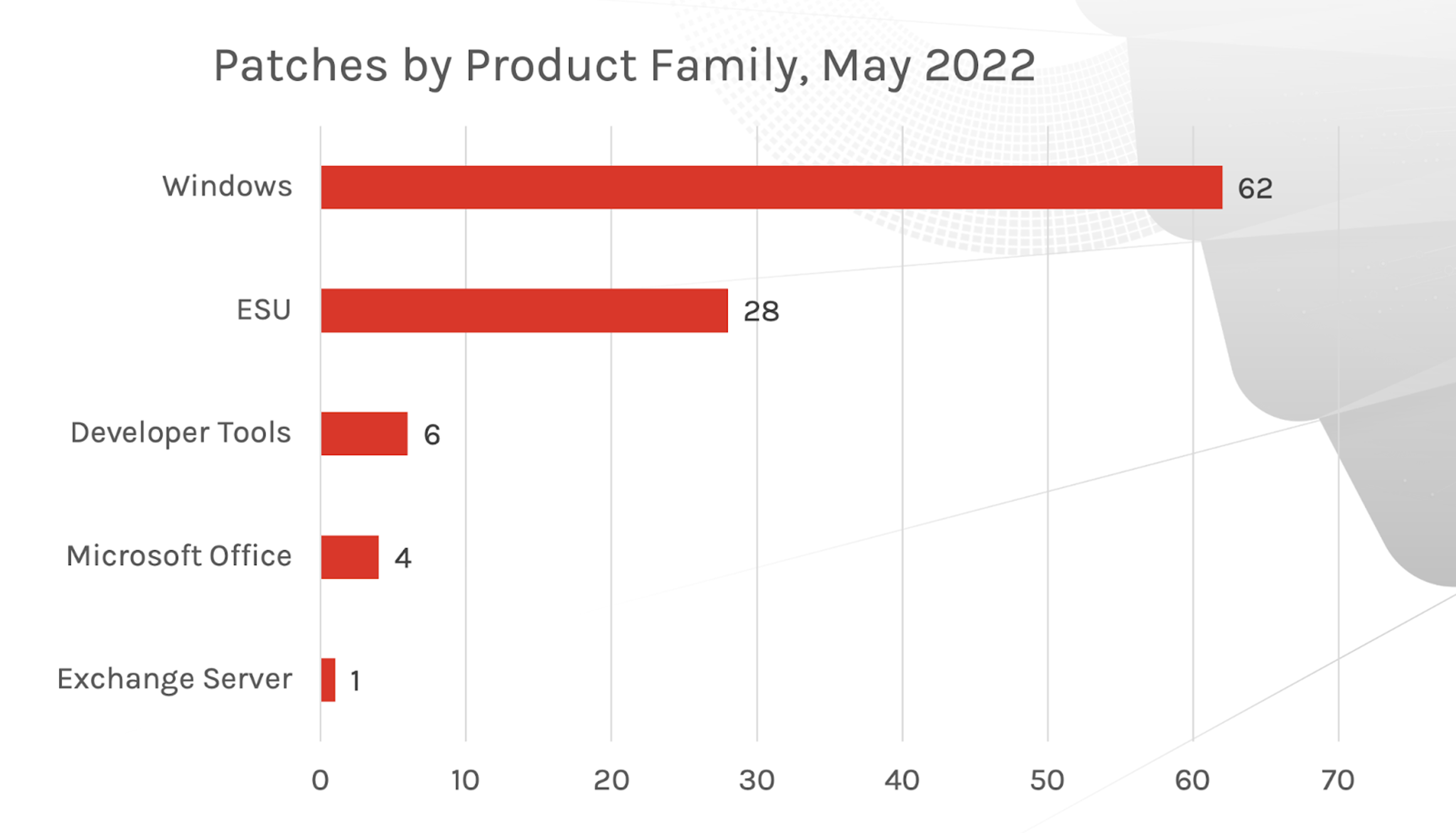 Figure 2. Breakdown of May 2022 Patch Tuesday affected product families
Figure 2. Breakdown of May 2022 Patch Tuesday affected product families
Two Important Vulnerabilities: LSA Spoofing CVE and Microsoft Exchange Server CVE
Two vulnerabilities involving LSA Spoofing and Microsoft Exchange Server received CVSS scores of 8.1 and 8.2 respectively and a rank of Important. Nonetheless, these vulnerabilities are relevant to any organization using the affected products.CVE-2022-26925: Windows LSA spoofing vulnerability, could allow an unauthenticated attacker to force a domain controller to authenticate against another server using Windows New Technology LAN Manager (NTLM). Microsoft notes this would be a CVSS 9.8 if combined with NTLM relay attacks, making this vulnerability potentially more severe. In addition to updating with the offered patch, sysadmins should review KB5005413 and Advisory ADV210003 to see what additional measures can be taken to prevent NTLM relay attacks.
CVE-2022-21978: Microsoft Exchange Server elevation of privilege vulnerability. Ranked as Important with a CVSS of 8.2, this vulnerability could allow an attacker with elevated privileges on the Exchange server to gain the rights of a Domain Administrator. This could allow access and controls outside of the expected scope of the targeted functionality. Additional steps should be taken in addition to applying the patch. For more details refer to this Microsoft guidance.
| Rank | CVSS Score | CVE | Description |
| Important | 8.1 | CVE-2022-26925 | Windows LSA Spoofing Vulnerability |
| Important | 8.2 | CVE-2022-21978 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
May 2022 Risk Analysis
The top three attack types — remote code execution (RCE), elevation of privilege and information disclosure — continue to dominate, with denial of service following at 8% (the same percentage as in April 2022). Figure 1. Breakdown of May 2022 Patch Tuesday attack types
Figure 1. Breakdown of May 2022 Patch Tuesday attack types
 Figure 2. Breakdown of May 2022 Patch Tuesday affected product families
Figure 2. Breakdown of May 2022 Patch Tuesday affected product familiesCritical Vulnerabilities Affecting Active Directory, NFS and More
Six vulnerabilities ranked as Critical received patches this month across a number of Microsoft products, most notably for Windows Network File System (NFS), Kerberos and Active Directory. Let’s review each of these vulnerabilities and how they could affect an organization’s environment.CVE-2022-26923: This Active Directory Domain Services elevation of privilege vulnerability with a CVSS of 8.8 exists within the issuance of certificates. By including crafted data in a certificate request, an attacker can obtain a certificate that allows them to authenticate to a domain controller with a high level of privilege. Essentially any domain authenticated user can become a domain admin if Active Directory Certificate Services are running on the domain. CVE-2022-26937: This Windows Network File System remote code execution vulnerability with a CVSS of 9.8 could allow remote, unauthenticated attackers to execute code in the context of the Network File System (NFS) service on affected systems. NFS isn’t on by default, but it’s prevalent in environments where Windows systems are mixed with other operating systems such as Linux or Unix.
| Rank | CVSS Score | CVE | Description |
| Critical | 8.8 | CVE-2022-26923 | Active Directory Domain Services Elevation of Privilege Vulnerability |
| Critical | 8.1 | CVE-2022-21972 | Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.1 | CVE-2022-23270 | Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-22017 | Remote Desktop Client Remote Code Execution Vulnerability |
| Critical | 7.5 | CVE-2022-26931 | Windows Kerberos Elevation of Privilege Vulnerability |
| Critical | 9.8 | CVE-2022-26937 | Windows Network File System Remote Code Execution Vulnerability |
Ten Windows LDAP Remote Code Execution Vulnerabilities
Ten RCE vulnerabilities affecting Windows Lightweight Directory Access Protocol (LDAP) received patches this month. All are ranked as Important, with two vulnerabilities that warrant additional attention: CVE-2022-22012 and CVE-2022-29130. The highest-ranked LDAP bugs, with a CVSS of 9.8, are only exploitable if the MaxReceiveBuffer LDAP policy is set to a value higher than the default value. Systems with the default value of this policy would not be vulnerable. Successful exploitation could result in the attacker's code running in the context of the SYSTEM account.| Rank | CVSS Score | CVE | Description |
| Important | 9.8 | CVE-2022-22012 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 9.8 | CVE-2022-29130 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-22013 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-22014 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-29128 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-29129 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-29131 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-29137 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-29139 | Windows LDAP Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-29141 | Windows LDAP Remote Code Execution Vulnerability |
More Print Spooler Vulnerabilities
Four out of the 17 information disclosure vulnerabilities patched in this month’s release impact Print Spooler, with CVSS scores ranging between 5.5 and 7.8. These bugs result from the lack of proper validation of a user-supplied path prior to using it in file operations. An attacker can leverage these vulnerabilities to disclose information in the context of SYSTEM. Most of the other information disclosure bugs in this release only result in leaks consisting of unspecified memory contents.Adversaries Are Becoming More Sophisticated — Your Patching Strategy Should Too
Adversaries are becoming more crafty and diligent in their efforts to exploit vulnerabilities, as discussed in the CrowdStrike 2022 Global Threat Report and reflected in the recent update to Cybersecurity and Infrastructure Security Agency’s (CISA) Known Vulnerabilities Catalog. Although Microsoft offers patches to some systems on a monthly basis, your organization may be using other operating systems and applications, and those are just as likely to be exploited.CrowdStrike always recommends reviewing your patching strategy and the methodology behind what gets patched first, but how to get it done often frustrates SecOps teams. That’s why we developed Falcon Spotlight ExPRT.AI: to succinctly predict which vulnerabilities pose the most risk to your environment so that you are able to patch before an attacker can penetrate your systems. Falcon Spotlight ExPRT.AI provides valuable data and insights for a more accurate understanding of how these vulnerabilities could affect your environment. This solution utilizes the intelligence of an always adapting AI model to help your team address the onslaught of vulnerabilities that must be reviewed every month. It can make a dramatic difference for your team and for protecting your organization — see how it can help you in this video.
Learn More
This video on Falcon Spotlight™ vulnerability management shows how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Learn how Falcon Identity Protection products can stop workforce identity threats faster.
- Download the CrowdStrike 2022 Global Threat Report to learn who and what is affecting your environment.
- Learn about the latest trending threat in Linux and how you can find it.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)
































