Microsoft has released its October 2021 updates covering a garden variety of vulnerabilities that threat actors can exploit using several attack types, from remote code execution to spoofing to privilege elevation and more. An active zero-day, CVE-2021-40449, should be one of the first that organizations prioritize in their patching cycle, and other vulnerabilities with Microsoft priority rankings should also be considered.
SecOps staff should carefully review the rankings that Microsoft and the National Vulnerability Database have provided for these vulnerabilities — some should be elevated beyond the industry-standard Common Vulnerability Scoring System (CVSS) rating assigned. But, additional review can be challenging for organizations, especially those with limited time and resources. Falcon Spotlight’s™ newly announced feature, the ExPRT.AI model, will help with that — it will be available to all Falcon Spotlight™ customers next week. This ever-adapting model will predict which vulnerabilities are truly critical for your organization to address.

Among other vulnerabilities reported this month, three affect Microsoft Sharepoint, a remote code execution vulnerability affects Windows DNS Server, and one is a Print Spooler vulnerability. CVE-2021-36970 is related to the Printing Service, and while it was given a score of Important by Microsoft, CVSS has scored it as an 8.8. SecOps staff should consider prioritizing the updates for these CVEs.
Microsoft Exchange Vulnerabilities: A Myriad of Attack Types
This month, there are four vulnerabilities associated with Microsoft Exchange Server, each with a different attack type. CVE-2021-26427 has the highest CVSS score, but Microsoft gave it only a rank of Important. It is utilized via remote code execution. This vulnerability should be prioritized — recall that Microsoft Exchange Servers impacted thousands of systems earlier this year after multiple zero-day vulnerabilities were discovered in March. Microsoft has even offered out-of-band updates to address this vital product.
Among the remaining high-priority vulnerabilities, CVE-2021-41348 is utilized by attackers through privilege elevation, CVE-2021-34453 through denial of service, and 2021-41350 through spoofing.
Additional Resources
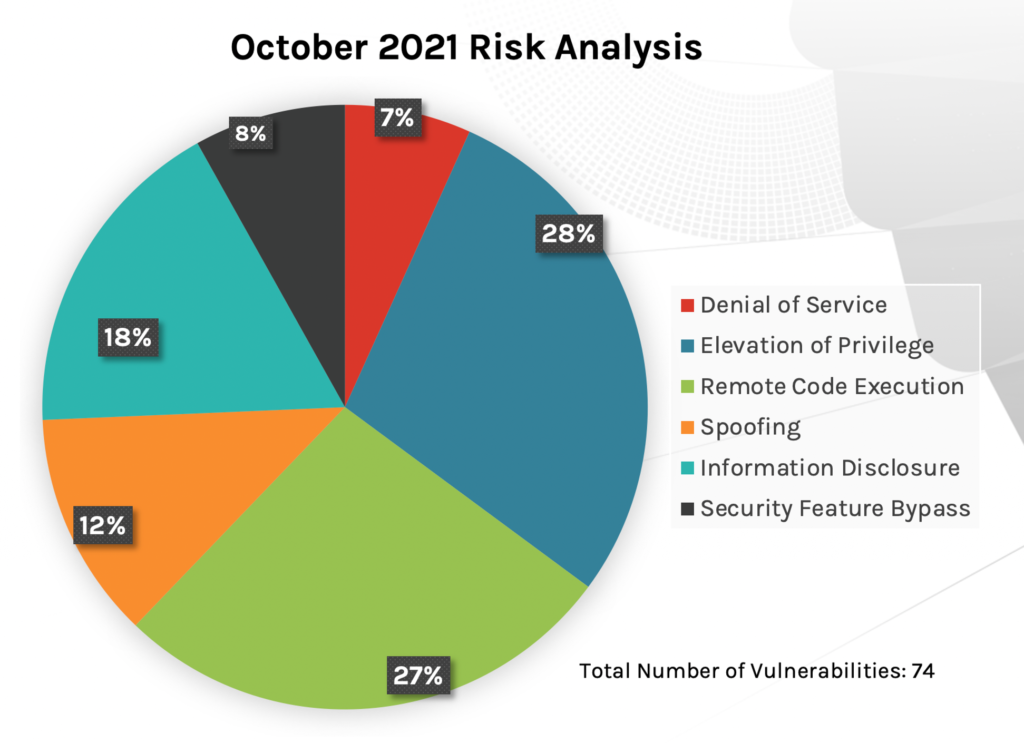
New Patches for 74 Vulnerabilities
This month’s Patch Tuesday updates include fixes for 74 vulnerabilities. Of these, Microsoft Exchange received four patches for remote code execution vulnerabilities. And, not surprisingly, another actively exploited vulnerability that received an update this month — CVE-2021-40449 — has been exploited using elevation of privilege. Attackers have been capitalizing on it by employing a use-after-free (UAF) vulnerability, which is a memory corruption bug. UAF is enabled by the mechanisms of dynamic memory allocation. If, after freeing a memory location, a program doesn’t clear the pointer to that memory location, an attacker may gain access to the program by capitalizing on that error. Customers can see the detection for this vulnerability within the Falcon Spotlight console. Other CVEs that received updates are another one affecting the Microsoft Print Spooler Service (the same service affected during PrintNightmare), multiple vulnerabilities for Sharepoint, and a Windows DNS vulnerability. As in September, Windows products and Extended Security Updates (ESU) continue to be the most affected and patched of Microsoft product families (see Figure 2).

Active Exploitation for CVE-2021-40449 Zero-Day
A use-after-free vulnerability affecting Win32k would allow an attacker to escalate privileges on the affected systems. This vulnerability has been reported as exploited by Microsoft, and there are public reports about it being leveraged by a threat actor group.According to the reporters of this zero-day, the vulnerability resides within the NtGdiResetDC function. Besides this vulnerability, researchers have become aware of two other privilege escalation vulnerabilities affecting Win32k, but these have not yet been exploited and there is currently no knowledge of exploits for them. Two points to note: Microsoft has rated them as important, and the CVSS Score for all three is 7.8.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2021-40449 | Win32k Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-41357 | Win32k Elevation of Privilege Vulnerability |
| Important | 7.8 | CVE-2021-40450 | Win32k Elevation of Privilege Vulnerability |
Other Critical Vulnerabilities to Prioritize
Again this month, there are three Critical vulnerabilities that organizations should consider prioritizing. It should be noted that Microsoft ranked these vulnerabilities even though the exploitability assessment has been determined to be Less Likely. As of this writing, none of these vulnerabilities have been exploited.CVE-2021-40461: This vulnerability was given a rating of Critical with a CVSS score of 8. It occurs on Windows Hyper-V, also known as Viridian. Hyper-V is a native hypervisor, meaning it can create virtual machines on x86-64 systems running Windows. For this vulnerability, attackers use remote code execution to gain access to the system. This vulnerability impacts both Windows 11 and Windows 10 as well as servers. CVE-2021-38672: This CVE is another Windows Hyper-V vulnerability that has also been given a Critical rating — attackers also use remote code execution to gain access. It affects Windows 11 and Windows Servers 2022. CVE-2021-40486: As with the above-listed vulnerabilities, attackers also use remote code execution for CVE-2021-40486. For this CVE, threat actors may use the Preview Pane in Windows as an attack vector.
While the CVSS score is lower, and Microsoft indicates that exploitation is Less Likely, these vulnerabilities, if left unpatched, could dramatically impact your organization. CrowdStrike encourages organizations to prioritize these vulnerabilities in their patching cycle.
| Rank | CVSS Score | CVE | Description |
| Critical | 8 | CVE-2021-40461 | Windows Hyper-V Remote Code Execution Vulnerability |
| Critical | 8 | CVE-2021-38672 | Windows Hyper-V Remote Code Execution Vulnerability |
| Critical | 7.8 | CVE-2021-40486 | Microsoft Word Remote Code Execution Vulnerability |
| Rank | CVSS Score | CVE | Description |
| Important | 8.1 | CVE-2021-40487 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Important | 7.6 | CVE-2021-40484 | Microsoft SharePoint Server Spoofing Vulnerability |
| Important | 5.3 | CVE-2021-40482 | Microsoft SharePoint Server Information Disclosure Vulnerability |
| Important | 7.2 | CVE-2021-40469 | Windows DNS Server Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2021-36970 | Windows Print Spooler Spoofing Vulnerability |
Microsoft Exchange Vulnerabilities: A Myriad of Attack Types
This month, there are four vulnerabilities associated with Microsoft Exchange Server, each with a different attack type. CVE-2021-26427 has the highest CVSS score, but Microsoft gave it only a rank of Important. It is utilized via remote code execution. This vulnerability should be prioritized — recall that Microsoft Exchange Servers impacted thousands of systems earlier this year after multiple zero-day vulnerabilities were discovered in March. Microsoft has even offered out-of-band updates to address this vital product.
Among the remaining high-priority vulnerabilities, CVE-2021-41348 is utilized by attackers through privilege elevation, CVE-2021-34453 through denial of service, and 2021-41350 through spoofing.
| Rank | CVSS Score | CVE | Description |
| Important | 9 | CVE-2021-26427 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| Important | 8 | CVE-2021-41348 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| Important | 7.5 | CVE-2021-34453 | Microsoft Exchange Server Denial of Service Vulnerability |
| Important | 6.5 | CVE-2021-41350 | Microsoft Exchange Server Spoofing Vulnerability |
When Ranking and Scores Don’t Match, Rely on Dynamic Scoring and Vulnerability Severity Prediction
It can be difficult for IT staff to determine which vulnerabilities will truly have a negative impact in their environment, especially considering the differences in scoring and ratings between Microsoft and CVSS for vulnerabilities this month. SecOps teams typically have a limited amount of time to determine which vulnerabilities will affect them the most, and with the wide variety of applications affected this month, many may experience a gap in their prioritization process. Recognizing this challenge, CrowdStrike offers a new rating process that not only quickly and more accurately rates vulnerabilities that are important to an organization, it can also predict which vulnerabilities will have the greatest impact in their environment. You can learn more about this new Exploit Prediction Rating via Falcon Spotlight in the announcement blog.
Learn More
Watch this video on Falcon Spotlight™ vulnerability management to see how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Learn more on how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- See how Falcon Complete stops Microsoft exchange server zero-day exploits.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Read last month’s Patch Tuesday for more information on critical vulnerabilities your organization should prioritize.
- Learn about the recent Baron Samedit vulnerability and CrowdStrike’s custom dashboard.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)
































