Microsoft has released 63 security patches for its September 2022 Patch Tuesday rollout. Five vulnerabilities are rated Critical, 57 are rated Important, one is Moderate, and one is rated Low in severity. This month’s release includes a bug discovered by CrowdStrike in conjunction with other security researchers: CVE-2022-37969 is publicly known and there is evidence it has been exploited in the wild.
In this blog, the CrowdStrike Falcon® Spotlight™ team analyzes this month’s vulnerabilities, highlights the most severe CVEs and recommends how to prioritize patching.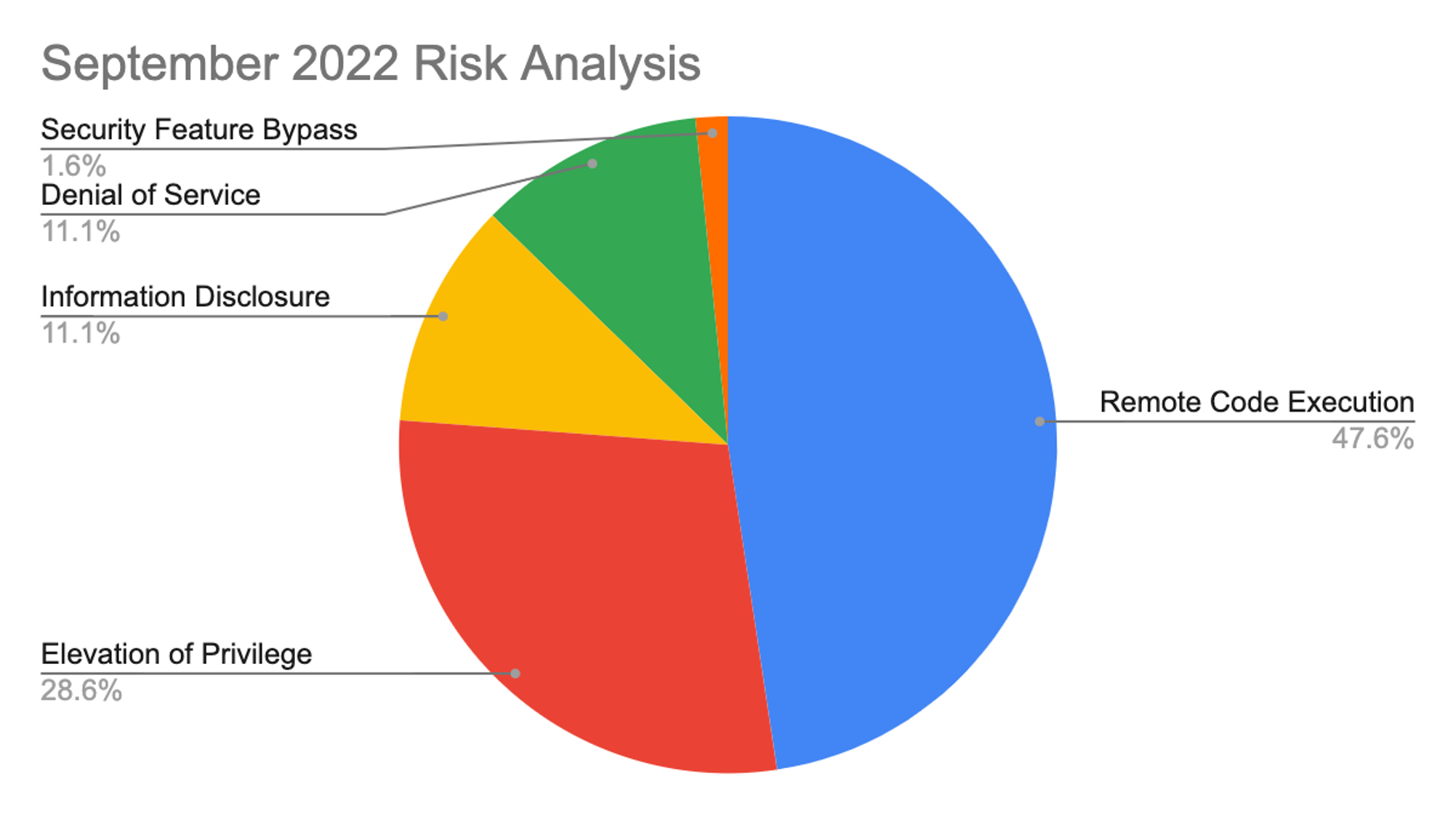 Figure 1. Breakdown of September 2022 Patch Tuesday attack types
The Microsoft Windows product family received the most patches this month with 48, followed by Extended Support Updates (36) and Microsoft Office products (7). One zero-day vulnerability being used in active attacks is also covered in the update. This CVE affects Windows Common Log File System Driver and is rated as Important with a CVSS of 7.8.
Figure 1. Breakdown of September 2022 Patch Tuesday attack types
The Microsoft Windows product family received the most patches this month with 48, followed by Extended Support Updates (36) and Microsoft Office products (7). One zero-day vulnerability being used in active attacks is also covered in the update. This CVE affects Windows Common Log File System Driver and is rated as Important with a CVSS of 7.8.
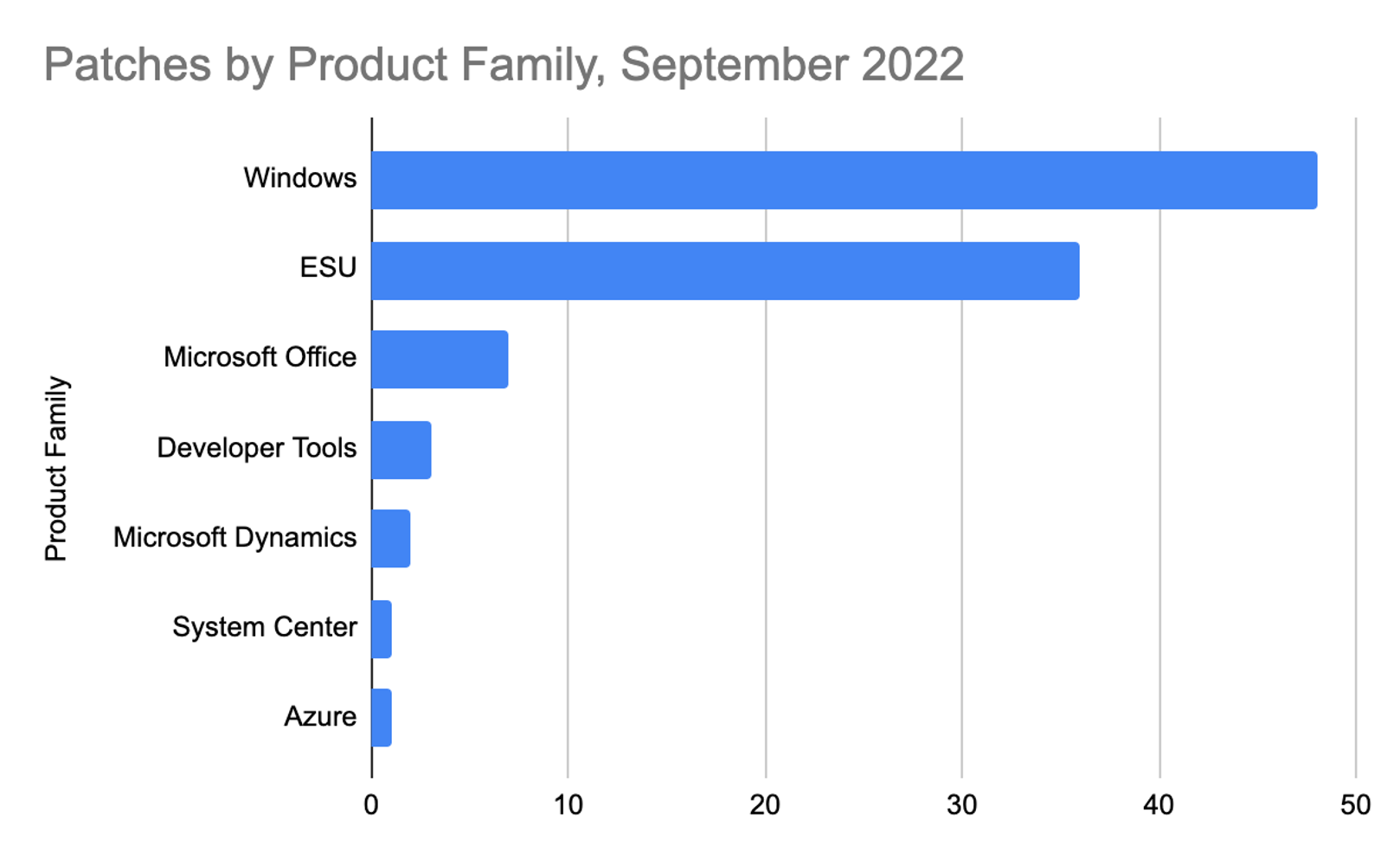 Figure 2. Breakdown of product families affected by September 2022 Patch Tuesday
Figure 2. Breakdown of product families affected by September 2022 Patch Tuesday
Active Attack: Zero-Day Vulnerability Affecting Windows Common Log File System Driver
There is a patch available for CVE-2022-37969, an actively exploited vulnerability in Microsoft Windows Common Log File System Driver. CrowdStrike reported this zero-day in a combined effort with other vendors (see acknowledgements section in the Microsoft advisory).
On August 29, 2022, the CrowdStrike Falcon® OverWatch™ threat hunting team observed malicious remote desktop protocol (RDP) activity against a consumer goods company via an undetermined initial access vector, allowing for delivery and execution of a binary. Preliminary analysis of the malicious tool showed it facilitates local privilege escalation (LPE) on fully patched Windows 10 systems; it should be noted that other Windows versions are also likely affected. As shown in Figure 3, this CVE is ranked as Important.
September 2022 Risk Analysis
This month’s leading risk type is remote code execution (48%), followed by elevation of privilege at nearly 29%, and information disclosure and denial of service, both at 11%. Remote code execution (RCE) vulnerabilities are among the most dangerous and high-impact vulnerabilities in existence. Many major cyberattacks have been enabled by RCE vulnerabilities, including Log4j. Rigorously enforcing the principle of least privilege and knowing where the most sensitive company data is stored are critical for creating a defensive security posture. Figure 1. Breakdown of September 2022 Patch Tuesday attack types
Figure 1. Breakdown of September 2022 Patch Tuesday attack types Figure 2. Breakdown of product families affected by September 2022 Patch Tuesday
Figure 2. Breakdown of product families affected by September 2022 Patch TuesdayActive Attack: Zero-Day Vulnerability Affecting Windows Common Log File System Driver
There is a patch available for CVE-2022-37969, an actively exploited vulnerability in Microsoft Windows Common Log File System Driver. CrowdStrike reported this zero-day in a combined effort with other vendors (see acknowledgements section in the Microsoft advisory).
On August 29, 2022, the CrowdStrike Falcon® OverWatch™ threat hunting team observed malicious remote desktop protocol (RDP) activity against a consumer goods company via an undetermined initial access vector, allowing for delivery and execution of a binary. Preliminary analysis of the malicious tool showed it facilitates local privilege escalation (LPE) on fully patched Windows 10 systems; it should be noted that other Windows versions are also likely affected. As shown in Figure 3, this CVE is ranked as Important.
| Rank | CVSS Score | CVE | Description |
| Important | 7.8 | CVE-2022-37969 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
Figure 3. Zero-day vulnerability patched in September 2022
The two Important vulnerabilities affecting Windows Kerberos this month are elevation of privilege CVEs, both with a CVSS of 8.1, as shown in Figure 4. In the context of Active Directory (AD), Kerberos is intended to be a more secure method of authentication when compared to NTLM. Instead of using passwords as NTLM does, Kerberos uses tickets to authenticate to services. Kerberos tickets contain a user’s logon information in an encrypted form.| Rank | CVSS Score | CVE | Description |
| Important | 8.1 | CVE-2022-33647 | Windows Kerberos Elevation of Privilege Vulnerability |
| Important | 8.1 | CVE-2022-33679 | Windows Kerberos Elevation of Privilege Vulnerability |
Figure 4. Windows Kerberos vulnerabilities in September 2022
Critical Vulnerabilities in TCP/IP, IKE and Microsoft Dynamics 365
Let’s explore this month’s critical vulnerabilities. CVE-2022-34718, a Windows TCP/IP remote code execution vulnerability, could allow a remote, unauthenticated attacker to execute code with elevated privileges on affected systems without user interaction. This officially puts it into the “wormable” category and earns it a CVSS rating of 9.8 and a rank of Critical. However, only systems with IPv6 enabled and IPSec configured are considered vulnerable. Two other Critical bugs for Windows Internet Key Exchange (IKE) Protocol Extensions could also be classified as “wormable,” but only systems running IPSec are affected. The remaining two vulnerabilities in this month’s list affect the on-premises version of Microsoft Dynamics 365 — they could allow an authenticated user to perform SQL injection attacks and execute commands as db_owner within their Dynamics 356 database. CrowdStrike recommends prioritizing these vulnerabilities within your patching strategy if your organization uses these products.| Rank | CVSS Score | CVE | Description |
| Critical | 9.8 | CVE-2022-34718 | Windows TCP/IP Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2022-34721 | Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability |
| Critical | 9.8 | CVE-2022-34722 | Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-34700 | Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability |
| Critical | 8.8 | CVE-2022-35805 | Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability |
Figure 5. Critical Vulnerabilities in TCP/IP, IKE and Microsoft Dynamics 365
Important Microsoft SharePoint Server Vulnerabilities
Four Important remote code execution vulnerabilities affecting Microsoft SharePoint Server are receiving patches this month. It’s important to note that Microsoft customers running SharePoint Enterprise Server 2013 Service Pack 1 should also install the wssloc update as it contains language pack updates (this applies to CVE-2022-38008) per Microsoft advisory.| Rank | CVSS Score | CVE | Description |
| Important | 8.8 | CVE-2022-38009 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-38008 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Important | 8.8 | CVE-2022-37961 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Important | 8.1 | CVE-2022-35823 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
Figure 6. Important Microsoft SharePoint Server vulnerabilities
Consider How Your Patching Strategy Affects Your Organization
Vulnerability management does not live in a vacuum. While it's vitally important to prioritize the vulnerabilities that are critical to the functions of your business, remember that vulnerability management lives within the broader context of security operations and subsequently within the cybersecurity organization.What gets patched and what is moved to the back burner should be taken into consideration in conjunction with other areas of a defensive security posture, including security hygiene and XDR. Your organization’s security strategy, and what is involved in your patching program, could have a direct impact on the strength of your organization’s security. It's important to develop a strategy that works together with the broader organization's security goals, not just within security operations.
Learn More
This video on Falcon Spotlight™ vulnerability management shows how you can quickly monitor and prioritize vulnerabilities within the systems and applications in your organization.
About CVSS Scores
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard that CrowdStrike and many other cybersecurity organizations use to assess and communicate software vulnerabilities’ severity and characteristics. The CVSS Base Score ranges from 0.0 to 10.0, and the National Vulnerability Database (NVD) adds a severity rating for CVSS scores. Learn more about vulnerability scoring in this article.
Additional Resources
- Find out more about today’s adversaries and how to combat them at Fal.Con 2022, the cybersecurity industry’s most anticipated annual event. Register now and meet us in Las Vegas, Sept. 19-21!
- Download the CrowdStrike 2022 Falcon OverWatch Threat Hunting Report to learn more about recent adversary tradecraft and tooling and get actionable tips for staying ahead of today's stealthiest, most sophisticated cyber threats.
- See how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- Learn how Falcon Identity Protection products can stop workforce identity threats faster.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Test CrowdStrike next-gen AV for yourself with a free trial of Falcon Prevent™.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)
































