Over the past few months CrowdStrike has conducted several investigations in the hospitality, food services, and gaming industries, helping organizations investigate and remediate attacks by criminal entities determined to steal credit card data for the purposes of financial gain. These attacks have included criminal groups responsible for the delivery of NewPosThings, However, be careful who you let behind those high city walls. Over the past few months CrowdStrike has also seen service providers become the initial entry point for attackers.
However, be careful who you let behind those high city walls. Over the past few months CrowdStrike has also seen service providers become the initial entry point for attackers.
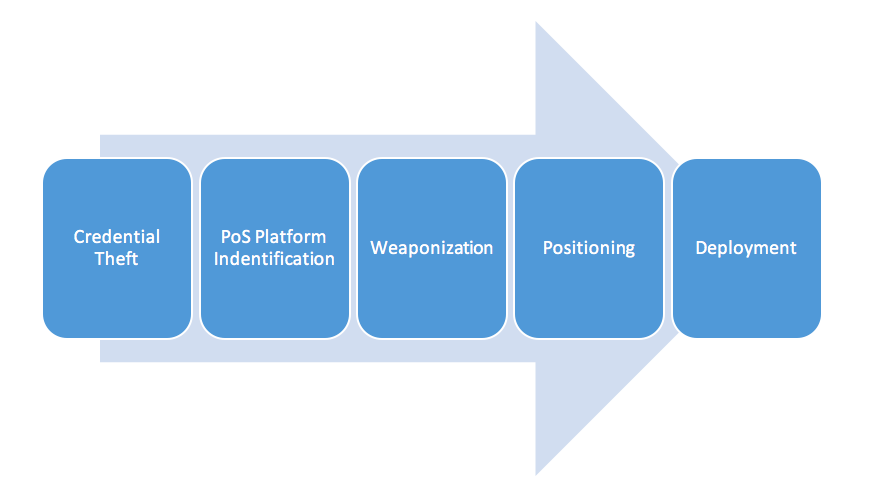 The viability of the attack is completely dependent on the theft and impersonation of legitimate credentials. This includes local, domain, and remote authentication credentials used to access and manage the corporate, franchise, and point of sale environments. From a security perspective, beyond the initial exploit, you are dealing with an insider threat problem. We have consistently seen the use of publicly available credential theft tools like Windows Credential Editor and Mimikatz to fulfill that need.
PoS Platform Identification and Weaponization is indicative of an attacker’s sophistication level. We have seen generic PoS malware capabilities, like process walking memory scrapers, as well as PoS malware that is weaponized against a single vendor. The generic use of process walking memory scraping malware is the security equivalent of the common cold and typically used by criminal organizations with low sophistication. The A-team operators are capable of weaponizing their PoS malware to target a specific vendor or platform. The ability to quickly generate targeted payloads is indicative of an effective synergy between reconnaissance and research and development. By employing targeted PoS malware, attackers reduce their chances of discovery by generic anti-virus or other defensive platforms. An additional benefit is the improved stability of the attack. The more sophisticated attackers can remain undetected for months, with the most common mode of discovery being notification from the credit card brands as opposed to a quarterly anti-virus update.
PCI DSS enforcement drives many merchants to employ MSSPs to implement a business’ boundary and host based defenses. Criminal organizations are aware of the commoditization of managed security and are transitioning their tactics to match. For instance, in a recent investigation, CrowdStrike analyzed a NewPoSThings sample that targeted a single point of sale vendor. The merchant employed a managed security service provider to implement boundary security in a PCI DSS compliant manner enforcing ingress and egress filtering. To ensure the campaigns viability the attacker weaponized the NewPoSThings sample to exfiltrate credit card data over the Domain Name Service (DNS) protocol. This effectively bypassed the managed security service providers firewall configurations for more than six months.
Additionally, to reduce the host-based forensic footprint, the NewPosThings sample refrained from writing a log file to the local disk to store stolen financial data for follow on exfiltration. Instead, the sample streamed data directly to command and control servers. Once the attacker has garnered enough credentials to effectively position his capabilities and make his deployment worthwhile, he begins propagating the attack. The most severe method is the use of third party service providers to deploy PoS malware capabilities to the target environment. For example, the criminal organization responsible for the deployment of NewPoSThings was able to compromise several hundred merchants belonging to a multi-national corporation through a third party payment service provider. The attackers were able to position themselves at a location inside our client’s architecture that facilitated a speedy deployment. While conducting the deployment of NewPoSThings the attackers averaged an infection rate that was less than one minute per system.
The viability of the attack is completely dependent on the theft and impersonation of legitimate credentials. This includes local, domain, and remote authentication credentials used to access and manage the corporate, franchise, and point of sale environments. From a security perspective, beyond the initial exploit, you are dealing with an insider threat problem. We have consistently seen the use of publicly available credential theft tools like Windows Credential Editor and Mimikatz to fulfill that need.
PoS Platform Identification and Weaponization is indicative of an attacker’s sophistication level. We have seen generic PoS malware capabilities, like process walking memory scrapers, as well as PoS malware that is weaponized against a single vendor. The generic use of process walking memory scraping malware is the security equivalent of the common cold and typically used by criminal organizations with low sophistication. The A-team operators are capable of weaponizing their PoS malware to target a specific vendor or platform. The ability to quickly generate targeted payloads is indicative of an effective synergy between reconnaissance and research and development. By employing targeted PoS malware, attackers reduce their chances of discovery by generic anti-virus or other defensive platforms. An additional benefit is the improved stability of the attack. The more sophisticated attackers can remain undetected for months, with the most common mode of discovery being notification from the credit card brands as opposed to a quarterly anti-virus update.
PCI DSS enforcement drives many merchants to employ MSSPs to implement a business’ boundary and host based defenses. Criminal organizations are aware of the commoditization of managed security and are transitioning their tactics to match. For instance, in a recent investigation, CrowdStrike analyzed a NewPoSThings sample that targeted a single point of sale vendor. The merchant employed a managed security service provider to implement boundary security in a PCI DSS compliant manner enforcing ingress and egress filtering. To ensure the campaigns viability the attacker weaponized the NewPoSThings sample to exfiltrate credit card data over the Domain Name Service (DNS) protocol. This effectively bypassed the managed security service providers firewall configurations for more than six months.
Additionally, to reduce the host-based forensic footprint, the NewPosThings sample refrained from writing a log file to the local disk to store stolen financial data for follow on exfiltration. Instead, the sample streamed data directly to command and control servers. Once the attacker has garnered enough credentials to effectively position his capabilities and make his deployment worthwhile, he begins propagating the attack. The most severe method is the use of third party service providers to deploy PoS malware capabilities to the target environment. For example, the criminal organization responsible for the deployment of NewPoSThings was able to compromise several hundred merchants belonging to a multi-national corporation through a third party payment service provider. The attackers were able to position themselves at a location inside our client’s architecture that facilitated a speedy deployment. While conducting the deployment of NewPoSThings the attackers averaged an infection rate that was less than one minute per system.
MalumPOS
and PoSeidon
point of sale Malware, as well as Carbanak
from the Russian criminal organization we track as Carbon Spider.
Where are your Vulnerabilities?
Attacks by these criminal organizations are not complex; most use publicly available Point of Sale (PoS) malware, backdoors, and credential theft software. So how are they so successful? Criminal organizations have learned to target vulnerabilities in your organizational structure that facilitate privileged access to your PoS environment. Specifically, these attackers have discovered methods to exploit existing seams in defenses created by franchise business models and third party service providers. Franchise networks present a unique security vulnerability for corporate environments. A franchise business is a business in which the owners, or "franchisors," sell the rights to their business logo, name, and model to third party retail outlets, owned by independent, third party operators, called "franchisees."What does this mean for security?
It means that franchises exist as independent legal entities not owned by the umbrella corporation, and are merely licensed. Therefore, information technology assets, security technology, and security policies are owned, operated, and developed by the franchise, not the corporate entity. This doesn’t mean franchisees have carte blanche authority to disregard security; they are still beholden to the laws and standards directed by organizational bodies like PCI SSC, PCI DSS, or other legal responsibilities. However, it does mean that corporate security plays little or no role in the defense of franchisees. As a result of these visibility gaps, the compromise of just one franchise typically leads to the breach of both the corporate environment and additional franchise locations. During a recent engagement at a large multinational corporation we saw an attacker exploit the relationship between the franchise and corporate parent by using the franchise network as a beachhead sanctuary from which to launch attacks. Efforts to investigate franchise assets were fiercely guarded by corporate lawyers exercising the protections afforded to an independent corporate entity. Using franchise computer systems suspected to be compromised through a phishing campaign, the attackers garnered legitimate credentials and began to launch an onslaught of infiltrations into the corporate network through dual-homed gateway systems that linked franchises to corporate networks. Their objective was the deployment of MalumPOS, a modular PoS attack framework targeting credit card data. Efforts to conduct an investigation into these point of origin systems located at franchise locations were slowed and eventually thwarted all together potentially leaving the corporate network vulnerable to attack even after a successful remediation. We get it. PCI DSS is a challenging hurdle to comply with for a small brick and mortar store. To ease the burden a business can transfer some of that responsibility to service providers. For a small franchise this is a cheap and easy solution to security and compliance. Hire a managed security service provider, payment processor, or IT organization to manage your network so you can focus on what your business does best. However, be careful who you let behind those high city walls. Over the past few months CrowdStrike has also seen service providers become the initial entry point for attackers.
However, be careful who you let behind those high city walls. Over the past few months CrowdStrike has also seen service providers become the initial entry point for attackers.
Why the service provider?
Service providers typically maintain privileged access, usually remote access, to a large swath of stores to facilitate the management and operations of the services they provide. They are a perfect inroad to a target environment where an attacker can mask the origin of his attack as well as establish an air of legitimacy while accessing systems. First, it can be difficult to notice malicious activity coming from a service provider due to the normal traffic originating from their networks. Second, service providers represent yet another independent legal entity that can significantly diminish your ability to respond by forcing organizations to dredge through a plethora of service agreements and legal requests to their various counsels.Tactics, Techniques, and Procedures
Investigating post exploitation methodologies used by PoS attackers consistently shows a well-rehearsed sequence of events. The viability of the attack is completely dependent on the theft and impersonation of legitimate credentials. This includes local, domain, and remote authentication credentials used to access and manage the corporate, franchise, and point of sale environments. From a security perspective, beyond the initial exploit, you are dealing with an insider threat problem. We have consistently seen the use of publicly available credential theft tools like Windows Credential Editor and Mimikatz to fulfill that need.
PoS Platform Identification and Weaponization is indicative of an attacker’s sophistication level. We have seen generic PoS malware capabilities, like process walking memory scrapers, as well as PoS malware that is weaponized against a single vendor. The generic use of process walking memory scraping malware is the security equivalent of the common cold and typically used by criminal organizations with low sophistication. The A-team operators are capable of weaponizing their PoS malware to target a specific vendor or platform. The ability to quickly generate targeted payloads is indicative of an effective synergy between reconnaissance and research and development. By employing targeted PoS malware, attackers reduce their chances of discovery by generic anti-virus or other defensive platforms. An additional benefit is the improved stability of the attack. The more sophisticated attackers can remain undetected for months, with the most common mode of discovery being notification from the credit card brands as opposed to a quarterly anti-virus update.
PCI DSS enforcement drives many merchants to employ MSSPs to implement a business’ boundary and host based defenses. Criminal organizations are aware of the commoditization of managed security and are transitioning their tactics to match. For instance, in a recent investigation, CrowdStrike analyzed a NewPoSThings sample that targeted a single point of sale vendor. The merchant employed a managed security service provider to implement boundary security in a PCI DSS compliant manner enforcing ingress and egress filtering. To ensure the campaigns viability the attacker weaponized the NewPoSThings sample to exfiltrate credit card data over the Domain Name Service (DNS) protocol. This effectively bypassed the managed security service providers firewall configurations for more than six months.
Additionally, to reduce the host-based forensic footprint, the NewPosThings sample refrained from writing a log file to the local disk to store stolen financial data for follow on exfiltration. Instead, the sample streamed data directly to command and control servers. Once the attacker has garnered enough credentials to effectively position his capabilities and make his deployment worthwhile, he begins propagating the attack. The most severe method is the use of third party service providers to deploy PoS malware capabilities to the target environment. For example, the criminal organization responsible for the deployment of NewPoSThings was able to compromise several hundred merchants belonging to a multi-national corporation through a third party payment service provider. The attackers were able to position themselves at a location inside our client’s architecture that facilitated a speedy deployment. While conducting the deployment of NewPoSThings the attackers averaged an infection rate that was less than one minute per system.
The viability of the attack is completely dependent on the theft and impersonation of legitimate credentials. This includes local, domain, and remote authentication credentials used to access and manage the corporate, franchise, and point of sale environments. From a security perspective, beyond the initial exploit, you are dealing with an insider threat problem. We have consistently seen the use of publicly available credential theft tools like Windows Credential Editor and Mimikatz to fulfill that need.
PoS Platform Identification and Weaponization is indicative of an attacker’s sophistication level. We have seen generic PoS malware capabilities, like process walking memory scrapers, as well as PoS malware that is weaponized against a single vendor. The generic use of process walking memory scraping malware is the security equivalent of the common cold and typically used by criminal organizations with low sophistication. The A-team operators are capable of weaponizing their PoS malware to target a specific vendor or platform. The ability to quickly generate targeted payloads is indicative of an effective synergy between reconnaissance and research and development. By employing targeted PoS malware, attackers reduce their chances of discovery by generic anti-virus or other defensive platforms. An additional benefit is the improved stability of the attack. The more sophisticated attackers can remain undetected for months, with the most common mode of discovery being notification from the credit card brands as opposed to a quarterly anti-virus update.
PCI DSS enforcement drives many merchants to employ MSSPs to implement a business’ boundary and host based defenses. Criminal organizations are aware of the commoditization of managed security and are transitioning their tactics to match. For instance, in a recent investigation, CrowdStrike analyzed a NewPoSThings sample that targeted a single point of sale vendor. The merchant employed a managed security service provider to implement boundary security in a PCI DSS compliant manner enforcing ingress and egress filtering. To ensure the campaigns viability the attacker weaponized the NewPoSThings sample to exfiltrate credit card data over the Domain Name Service (DNS) protocol. This effectively bypassed the managed security service providers firewall configurations for more than six months.
Additionally, to reduce the host-based forensic footprint, the NewPosThings sample refrained from writing a log file to the local disk to store stolen financial data for follow on exfiltration. Instead, the sample streamed data directly to command and control servers. Once the attacker has garnered enough credentials to effectively position his capabilities and make his deployment worthwhile, he begins propagating the attack. The most severe method is the use of third party service providers to deploy PoS malware capabilities to the target environment. For example, the criminal organization responsible for the deployment of NewPoSThings was able to compromise several hundred merchants belonging to a multi-national corporation through a third party payment service provider. The attackers were able to position themselves at a location inside our client’s architecture that facilitated a speedy deployment. While conducting the deployment of NewPoSThings the attackers averaged an infection rate that was less than one minute per system.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)

































