With cloud adoption surging and workforces becoming increasingly remote, it is more critical than ever for organizations to maintain comprehensive real-time visibility of their digital assets — regardless of location — to avoid any blind or weak spots that can be harnessed by bad actors and result in compromised or breached environments. Uncoordinated responses across devices and the network edge could result in two problems: 1) a waste of costly time and resources on alerts across multiple, siloed systems that do not talk to each other, and 2) even worse, threats that may go unattended for days and be weaponized for malicious intent.
Network detection and response (NDR) and endpoint detection and response (EDR) solutions form the two pillars of the SOC visibility triad to bring network and endpoint telemetry together for faster incident investigation and response, without negatively impacting productivity.
NDR products monitor east-west traffic (i.e., communications within the network) and apply advanced behavioral analytics with cloud-scale machine learning to rapidly detect, investigate and respond to threats that might otherwise remain hidden in unmanaged devices across on-premises, cloud and hybrid environments.
Modern EDR solutions provide continuous and comprehensive real-time visibility into what is happening on your endpoints, using behavioral analysis and actionable intelligence gleaned from rich endpoint data to stop an incident from turning into a breach.
CrowdStrike has released a pre-built, validated series of integrations with leading NDR and network threat analytics (NTA) partners. These integrations help organizations build a cohesive platform to create end-to-end visibility, and defend against any threats wherever those threats are encountered — from network edge to cloud and across endpoints and workloads. These integrations facilitate the sharing of contextual information and indicators of compromise (IOCs) across ecosystem vendors to help security teams become effective and efficient by providing early detection of complex attacks focused on endpoints or networks. The result is a well-coordinated response and remediation strategy.The Powerful Benefits of Integrating EDR and NDR Solutions
Overview of NDR Alliance Partners
CrowdStrike has partnered with NDR partners, including ExtraHop, Vectra, Awake Security, Darktrace, IronNet, Corelight and ThreatWarrior to help provide users with even more information for detecting advanced threats and making remediation decisions faster, strengthening the organization’s security posture from network edge to cloud.

The Powerful Benefits of Integrating EDR and NDR Solutions
- Enhanced visibility: Combining visibility in network communication with device telemetry gives customers broad visibility into and oversight of their networks and its devices and users, thus removing blind spots.
- Extended threat lifecycle management: Customized policies and real-time behavior-based discovery — using machine learning with aggregation of contextual network and endpoint telemetry — result in faster detection of anomalous behaviors and threats between devices and the network edge and within internal network traffic.
- Streamlined investigations and response: Seamless integrations and data aggregation break down silos across NDR and CrowdStrike® products by providing security analysts with a full range of incident information to use in their triaging and investigations and build response capabilities, ultimately speeding up incident response and mitigating risk.
- Frictionless automation: Create easy data schemes with contextual insights across endpoints and networks without manual rules, API changes or professional services engagements, achieving in scale and efficiency in responding to cyber threats.
Overview of NDR Alliance Partners
CrowdStrike has partnered with NDR partners, including ExtraHop, Vectra, Awake Security, Darktrace, IronNet, Corelight and ThreatWarrior to help provide users with even more information for detecting advanced threats and making remediation decisions faster, strengthening the organization’s security posture from network edge to cloud.

- ExtraHop provides cloud-native NDR for the hybrid enterprise with a breakthrough approach that analyzes all network interactions and applies cloud-scale machine learning for complete visibility, real-time detection and intelligent response. ExtraHop brings complete network intelligence to the CrowdStrike Falcon® platform with NDR, enriches network events with endpoint telemetry to help with device hygiene, detects threats anywhere in a hybrid, multi-cloud enterprise and leverages CrowdStrike response capabilities for quarantining compromised hosts for remediation.
- Vectra’s Cognito platform for NDR enables enterprises to immediately detect and respond to attacks across cloud, data center, enterprise and IoT networks. Vectra and CrowdStrike together provide threat intelligence, behavioral threat detection and automated response to help automatically triage and prioritize all detections based on the risk they pose, resulting in significantly reduced SOC workload. The integration allows users to pivot to the Falcon console’s Event Search to explore endpoint and workload
telemetry around any network event of interest. - Awake Security autonomously hunts and responds to both insider and external threats, delivering answers, not alerts. The combination of artificial intelligence (AI) and human expertise enables detection, forensics and incident response for the campus, data center, IoT and cloud. The Awake integration with Falcon allows users to correlate enriched endpoint telemetry using Falcon console’s Event Search for additional investigation into network events and provides network containment for response workflows.
- Darktrace Immune System, powered by self-learning AI, learns normal “patterns of life” to protect against unknown and unpredictable cyber threats. The platform integrates seamlessly with Falcon to extend self-learning visibility to the endpoint.
- Corelight Open NDR platform, powered by Zeek and Suricata, delivers fast answers to any question by a security analyst within a network and is fundamental for SOC strategy. The combination of Corelight’s Open NDR solutions enriched by CrowdStrike’s threat intelligence, plus the power of CrowdStrike’s newly acquired Humio capabilities, helps customers improve their defensive security infrastructure.
- IronNet delivers advanced network detection and response capabilities, enhanced by analytics, threat intelligence and a seamless ability to collaborate through collective defense. The Ironnet integration with Falcon allows users to correlate enriched endpoint telemetry using the Falcon console’s Event Search for additional investigation into network events, and it provides network containment for response workflows.
- ThreatWarrior identifies known threat signatures and anomalies in your network and software supply chain, including in your other security tools, using deep learning AI to provide threat intelligence and easy-to-miss threat identification. The integration with Falcon provides device information enrichment that helps streamline investigation capabilities.
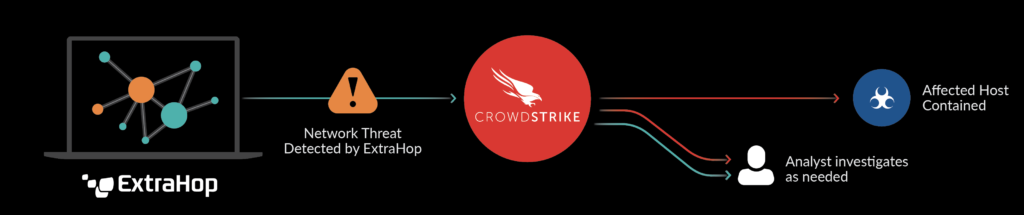
Customer Story: CrowdStrike + ExtraHop Deliver NDR for Full-spectrum Security
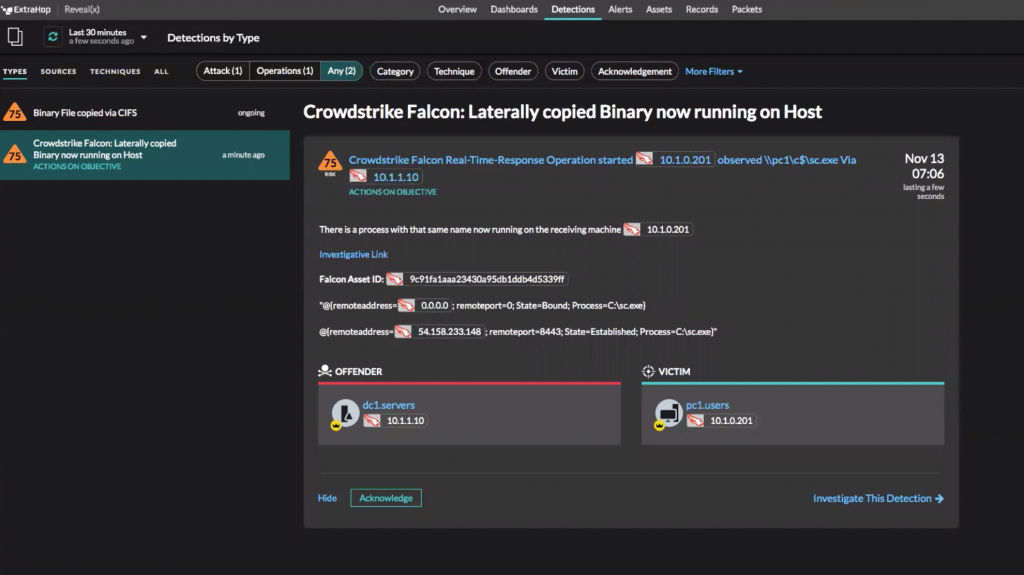
One of our joint customers is a large multinational retailer with one of the most sophisticated security postures in the world. It is always looking to innovate and improve its operations, as well as the tools and data on which it relies. In 2020, this retailer started using a series of integrations between CrowdStrike and our NDR partner, ExtraHop. From these integrations, the retailer gained a correlated view of the two most critical data sources for catching and stopping attackers: user and process behavior on every endpoint from CrowdStrike Falcon® Insight™EDR combined with the CrowdStrikeThreat Graph® database, enhanced with network behavior and fully decrypted forensic details from ExtraHop Reveal(x) 360. This integration enables key security use cases for our customer, including: Dynamic asset visibility: With dynamic asset discovery from ExtraHop Reveal(x) 360, the retailer was able to get real-time information about every device connected to the network, including whether that device was instrumented with the CrowdStrike Falcon® agent. The customer can quickly identify any IOT, unmanaged devices or shadow IT devices and deploy CrowdStrike for detection and response on the endpoint. Automated Falcon Real Time Response: Some attack tactics leave detectable signals on the network before they begin significantly impacting endpoints. Early attack behaviors detected by ExtraHop Reveal(x) 360 are fed to CrowdStrike Falcon® to automatically quarantine targeted endpoints. The integration offers fine-grained controls over which types of network threats result in autocontainment, delivering precision results based on high-fidelity data that minimizes both business disruption and risk for the retailer. Rapid forensic investigation: Forensic investigation of attack behaviors frequently requires both endpoint and network telemetry, but correlating these data sets to get a complete picture is often cumbersome and manual. To reduce this friction, our customer automatically pulls endpoint telemetry from Falcon Threat Graph into ExtraHop Reveal(x) 360 whenever a network threat is detected. Reveal(x) 360 correlates that endpoint data with relevant network behavior details for streamlined forensic analysis. This correlated data can also be sent to a SIEM for further analysis. As cyberattacks escalate in speed and sophistication, defenders need tools that help them stay ahead. When security solutions like ExtraHop Reveal(x) 360 and CrowdStrike Falcon® integrate seamlessly to make the right data available at the right time to the right people, and automate security tasks that once took manual intervention, security teams win. Get more details about how this customer and others are using ExtraHop and CrowdStrike to combat advanced threats and stop breaches faster.CrowdStrike’s Security Cloud is an open platform that enables seamless integration with best-of-breed solutions to help address customers’ real-world problems. To learn more about the Falcon platform, visit the platform architecture page. To learn more about all of these differentiated NDR integrations, please visit the CrowdStrike technology partner page.
Additional Resources
- Read the press release about CrowdStrike integration with network detection and response.
- Learn more about the integrations by visiting the webpage.
- Learn about CrowdStrike Falcon® platform by watching this on-demand product demo.
- Learn about the CrowdStrike Falcon® platform by visiting the webpage.
- Watch the demo with Extrahop and CrowdStrike with automated response use case.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)