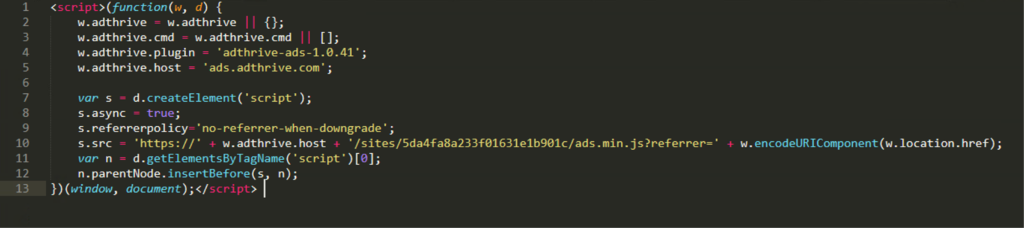
WebNavigatorBrowser is a web browser that meets the criteria of adware due to its injecting of ads into search results. The developer based it on Google’s free and open-source browser software project, Chromium. It is copyrighted and signed by Better Cloud Solutions LTD, a legally registered company in the U.K. And now it has fallen: Sectigo, (formerly known as Comodo) a well-known Certificate Authority (CA), revoked WebNavigatorBrowser’s certificate, as seen below.
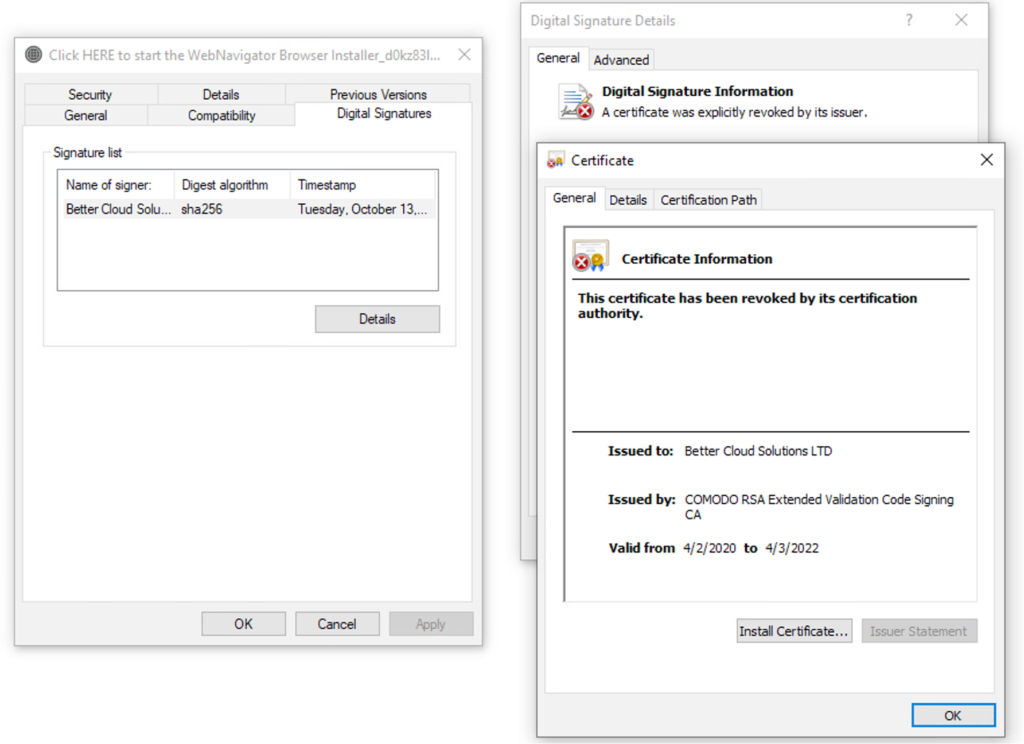 Figure 1. Revoked certificate
We began to see WebNavigatorBrowser back in November 2020 across multiple industries but observed it at a higher rate in the education vertical.
Figure 1. Revoked certificate
We began to see WebNavigatorBrowser back in November 2020 across multiple industries but observed it at a higher rate in the education vertical.
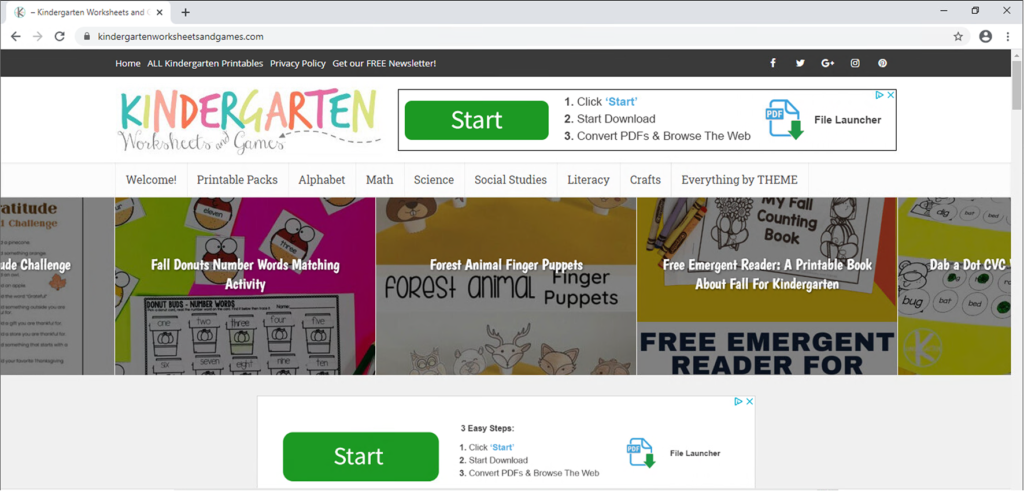 Figure 2. Kindergarten site containing ads that are pretexts to downloading WebNavigatorBrowser
CrowdStrike has found that one thing these websites had in common was that they were using AdThrive Ad Network, an advertising network that offers ad management and optimization to grow ad revenue.
Figure 2. Kindergarten site containing ads that are pretexts to downloading WebNavigatorBrowser
CrowdStrike has found that one thing these websites had in common was that they were using AdThrive Ad Network, an advertising network that offers ad management and optimization to grow ad revenue.
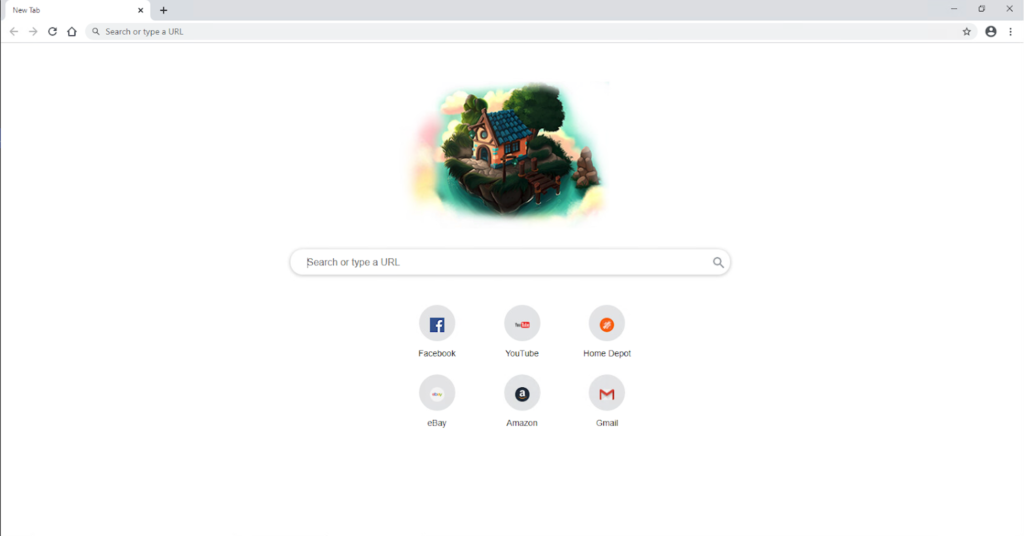 Figure 4. WebNavigatorBrowser new tab page
The page contains a script tag that hijacks the user's search to a Yahoo Host search results page.
Figure 4. WebNavigatorBrowser new tab page
The page contains a script tag that hijacks the user's search to a Yahoo Host search results page.
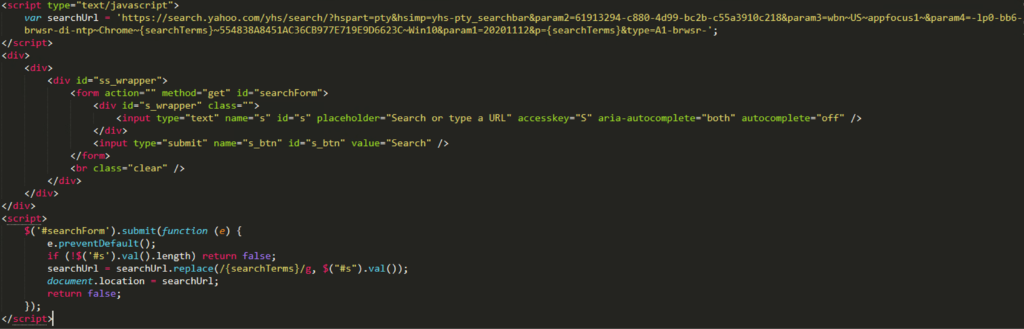 Figure 5. Script tag that will inject Better Cloud Solutions’ affiliated Yahoo Host search (Click to enlarge)
The search results page contains ads that are placed above the actual results, increasing the likelihood that the user will click on the ad and generate revenue for Better Cloud Solutions LTD.
Figure 5. Script tag that will inject Better Cloud Solutions’ affiliated Yahoo Host search (Click to enlarge)
The search results page contains ads that are placed above the actual results, increasing the likelihood that the user will click on the ad and generate revenue for Better Cloud Solutions LTD.
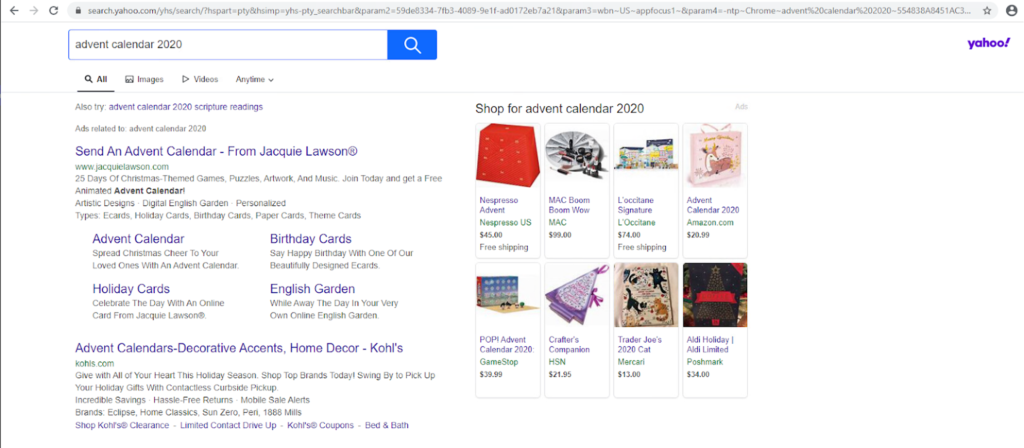 Figure 6. Ads displayed at the top of the search results page
Figure 6. Ads displayed at the top of the search results page
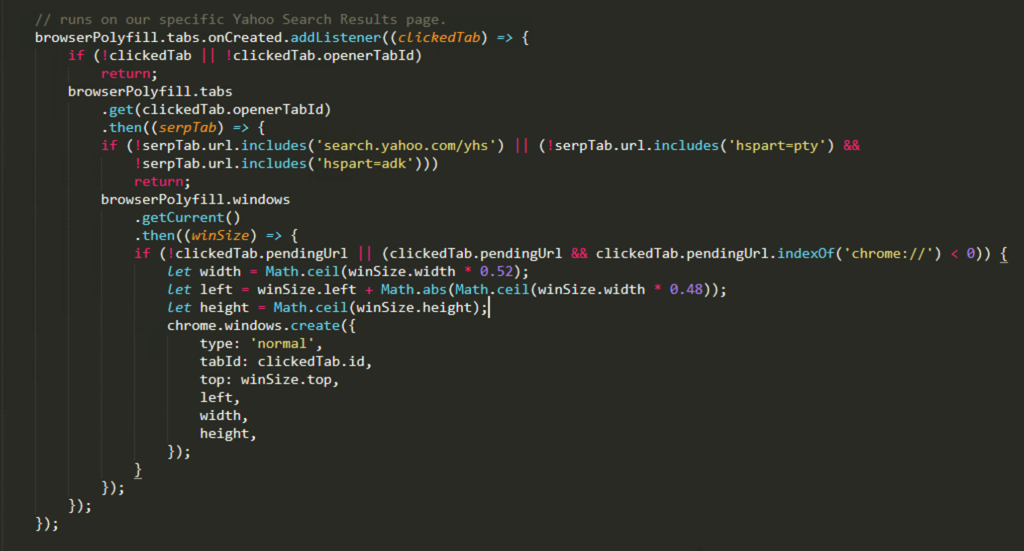 Figure 7.
In this case, it will run the
Figure 7.
In this case, it will run the
 Figure 1. Revoked certificate
Figure 1. Revoked certificateDeceptive Installation
In most cases, WebNavigatorBrowser is downloaded by users after they’ve been exposed to web ads that appear to be designed to attempt to trick them into downloading it. The most prevalent types of websites we observed serving these ads were sites targeting parents, homeschoolers and elementary school teachers. The sites offer free worksheets and games for kindergarten and preschool children but come with ads placed all over the site. Figure 2. Kindergarten site containing ads that are pretexts to downloading WebNavigatorBrowser
Figure 2. Kindergarten site containing ads that are pretexts to downloading WebNavigatorBrowserPost Installation Activities
Once installed, the adware will forcibly change the user's default browser to WebNavigatorBrowser and change the homepage for other browsers found on the machine to hxxps://webnavigator<.>co. It then creates a scheduled task called BetterCloudSolutions that launches WebNavigatorBrowser at login. Some versions of WebNavigatorBrowser will create a registry key in the following locations:- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- HKCU\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Run
 Figure 4. WebNavigatorBrowser new tab page
Figure 4. WebNavigatorBrowser new tab page Figure 5. Script tag that will inject Better Cloud Solutions’ affiliated Yahoo Host search (Click to enlarge)
Figure 5. Script tag that will inject Better Cloud Solutions’ affiliated Yahoo Host search (Click to enlarge) Figure 6. Ads displayed at the top of the search results page
Figure 6. Ads displayed at the top of the search results pageWinOpener Extension
WebNavigatorBrowser comes with a browser extension called WinOpener, located in:- %LOCALAPPDATA%\WebNavigatorBrowser\User Data\Default\Extensions\enlhdmhilhiklhomoeknchdlhdhamkfh\
lib/bg.js and has permission to access tabs, cookies and saved passwords. Bg.js contains code from https://github.com/mozilla/webextension-polyfill/, along with custom code to implement features that aren’t supported on Chromium.
 Figure 7.
Figure 7. browserPolyfill function seen in bg.js that will run on Better Cloud Solutions’ affiliated Yahoo Host search (Click to enlarge)browserPolyfill on Better Cloud Solutions’ affiliated Yahoo Search results to force open a new window instead of opening a new tab.
Based on the above behaviors — arriving on the machine after deceiving the user to install it, appearing as Chrome, hijacking the search session and installing a browser extension without the user’s knowledge or consent — CrowdStrike decided to mark WebNavigatorBrowser as adware. Others have done the same, such as in this example.
Recommendation
CrowdStrike detects WebNavigatorBrowser as adware, and we recommend that WebNavigatorBrowser be removed from machines. It is designed to generate ad revenue through displaying ads and convincing users to click on the ads. The presence of the browser extensions gives it the ability to collect users’ browsing data, cookies and saved passwords. The collected data can therefore be monetized to third parties (raising privacy concerns), or the data can be used to generate additional ad revenue. Since the extension runs a persistent background page, it can cause performance issues on some resource-limited machines because it constantly consumes system resources. It is important to note that the version of Chromium used by WebNavigatorBrowser came out in August 2020. It does not give the user the ability to update to a newer version of Chromium that includes several critical bug patches. For example, CVE-2020-15999, if combined with Windows kernel local elevation of privilege vulnerability CVE-2020-17087, will allow attackers to gain access to the machine with administrative privileges.Additional Resources
- Learn about recent intrusion trends, adversary tactics and highlights of notable intrusions in the 2020 Threat Hunting Report.
- Understand the trends and themes that we observed while responding to and remediating incidents around the globe in 2020 — download the latest CrowdStrike Services Cyber Front Lines Report.
- Learn more about the CrowdStrike Falcon® platform by visiting the product webpage.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)