Imagine this scenario: Your IT staff, pressed for time, checks for patches once every month after the Microsoft Patch Tuesday release. They spend a few minutes gathering intel and perhaps a few more minutes figuring out which patches should be prioritized based on your organization’s needs. The patches are included in the vulnerability management cycle and that’s about it. They move on to other important issues, and new patches are rarely considered until next month’s release is out.
This situation is common for many SecOps teams, but it might expose organizations to greater risk. Because of the regularly evolving nature of vulnerabilities and exploits, patching the top few vulnerabilities highlighted in Microsoft’s update every month may not provide you with the most robust security posture, according to the CrowdStrike analysis that follows.
With the first half of 2021 behind us, we took a retrospective deep dive into Microsoft’s vulnerability disclosures during that time period — those released in the regular Patch Tuesday updates and those released out-of-band (OOB). We discovered that while most Microsoft products received an update during the regular patch cycle, a staggering 30% of patched vulnerabilities occurred OOB.
With 612 CVEs affecting Microsoft’s products as of June 30 this year alone — a large quantity of them being OOB — it’s clear that reviewing both Patch Tuesday and OOB vulnerabilities should become a pivotal part of your vulnerability management lifecycle.
In this blog, we examine this vulnerability data in detail, share key insights and explore what the analysis might reveal for patching specific vulnerabilities — and what it might mean to an organization’s patching process. Our analysis of 2021 through June 30 covers:
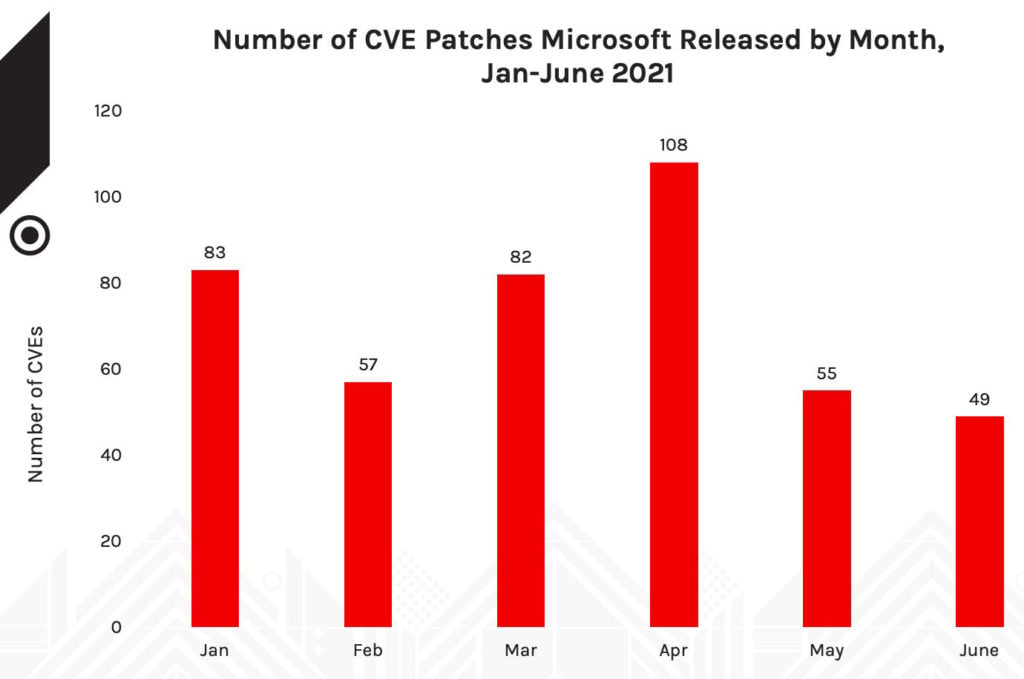 Figure 1. Number of CVEs that Microsoft released each month, January-June 2021
While April saw the greatest number of vulnerabilities patched (and was the only month to exceed 100), it's important to note that a greater number of vulnerabilities does not correlate to the highest risk or indicate a higher rate of exploitation, nor does it signify an increase in eCriminal behavior for a particular product or service.
When examining March and June in particular, as we discuss later under “Exploited Vulnerabilities,” we see in those months the highest number of actively exploited vulnerabilities patched by Microsoft. The actions resulting from each month’s exploited vulnerabilities differ — as what was reported, what was exploited and what was fixed may not be consistently updated. This presents a challenge for SecOps teams with little time to patch. Keep this in mind as we offer more insight below.
Figure 1. Number of CVEs that Microsoft released each month, January-June 2021
While April saw the greatest number of vulnerabilities patched (and was the only month to exceed 100), it's important to note that a greater number of vulnerabilities does not correlate to the highest risk or indicate a higher rate of exploitation, nor does it signify an increase in eCriminal behavior for a particular product or service.
When examining March and June in particular, as we discuss later under “Exploited Vulnerabilities,” we see in those months the highest number of actively exploited vulnerabilities patched by Microsoft. The actions resulting from each month’s exploited vulnerabilities differ — as what was reported, what was exploited and what was fixed may not be consistently updated. This presents a challenge for SecOps teams with little time to patch. Keep this in mind as we offer more insight below.Vulnerability Analysis by Microsoft Product Families
As we review the data displaying vulnerabilities affected by Microsoft product family (see Figure 2), the initial breakdown shows that nearly four out of 10 vulnerabilities affected Microsoft Windows. Closely following this are vulnerabilities that affected different browsers and Extended Security Updates (ESU) programs.
As stated previously, a higher number of patches for vulnerabilities does not necessarily correlate with exploitation; however, it can signal where most of the vulnerabilities are reported. In most cases, you should note that each one of the groups across Microsoft’s product families could be patched or remediated in different ways.
Moving a little further into this data, we see that Windows 10 and Windows Server received the most patches (addressing 260 and 257 vulnerabilities, respectively) for the May 2020 update (2004) version. However, within the browser product family, we see that Microsoft Edge (Chromium-based) received the highest number of updates, with 164 vulnerabilities having been patched.
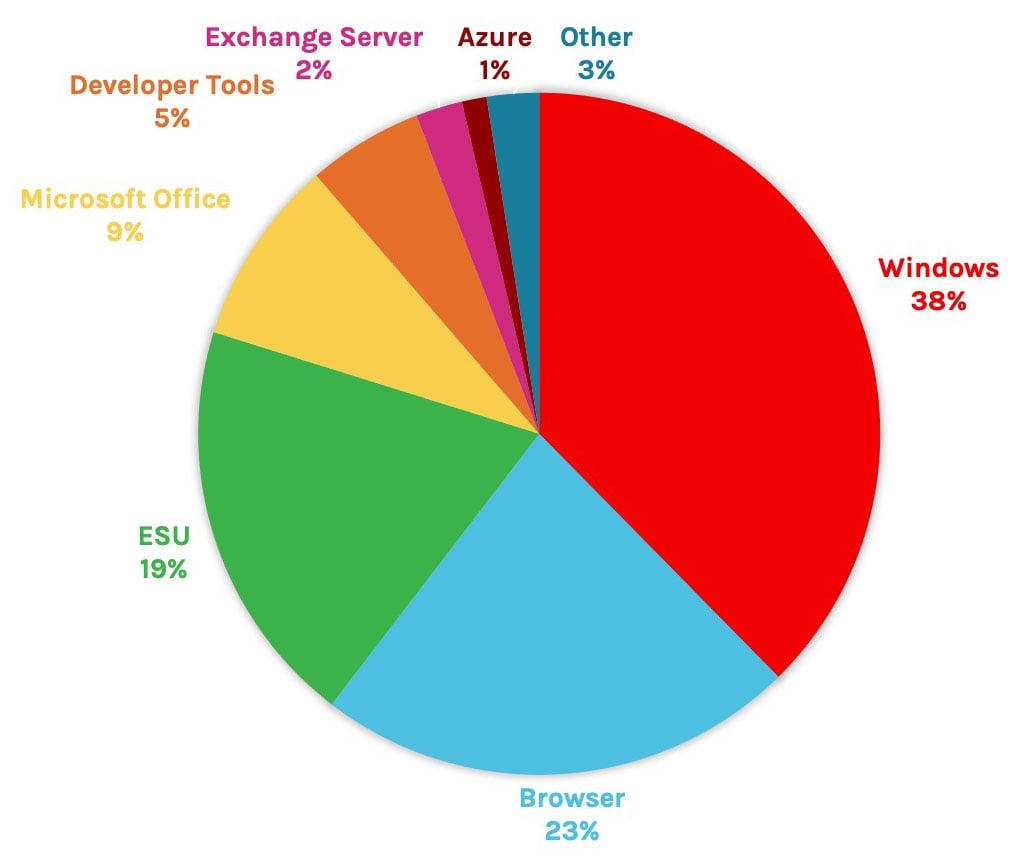 Figure 2. Number of vulnerability patches released by Microsoft product family, January-June 2021
Within the Windows product family alone, vulnerabilities affected 47 different products. In addition to the many flavors of supported operating systems, the myriad of products include HEVC Video Extensions and Windows Admin Center, among others.
Figure 2. Number of vulnerability patches released by Microsoft product family, January-June 2021
Within the Windows product family alone, vulnerabilities affected 47 different products. In addition to the many flavors of supported operating systems, the myriad of products include HEVC Video Extensions and Windows Admin Center, among others.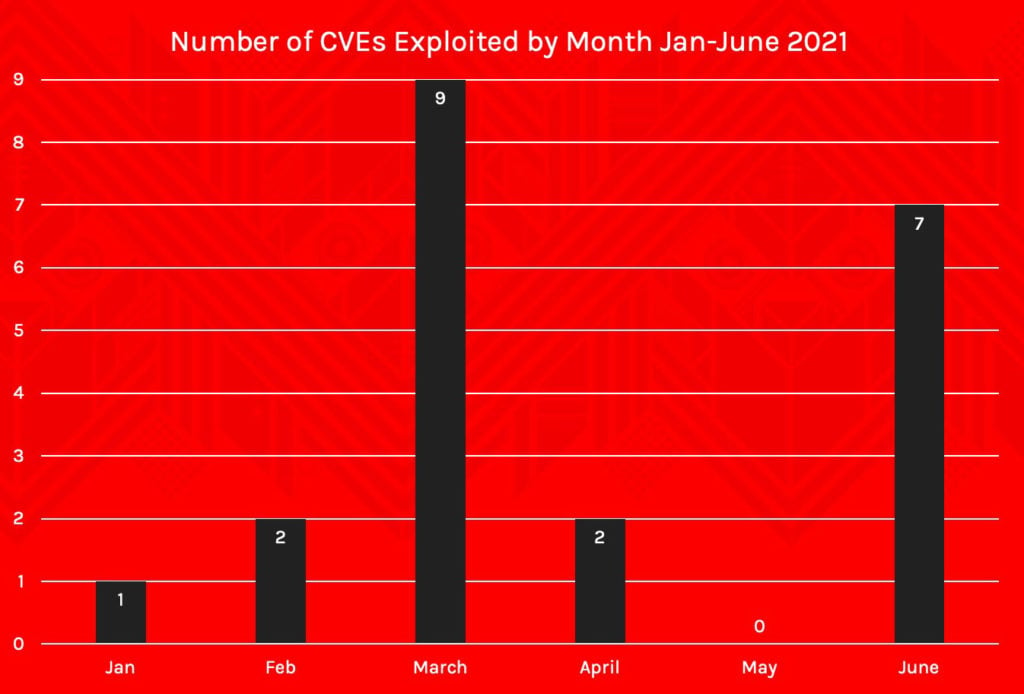 Figure 3. Number of CVEs that Microsoft reported as exploited by month, January-June 2021
Figure 3. Number of CVEs that Microsoft reported as exploited by month, January-June 2021
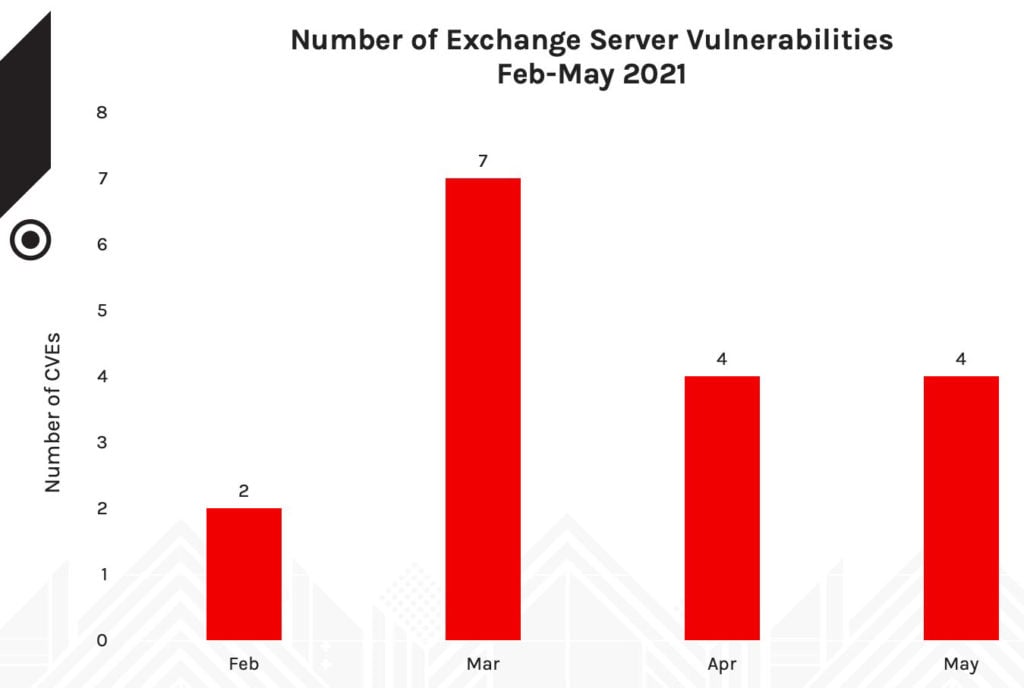 Figure 5. Number of Exchange Server Vulnerabilities, February-May 2021
As a result, patches for Microsoft Exchange Server vulnerabilities, due to their severity, became available OOB prior to the March Patch Tuesday update. While some organizations were quick to patch their systems, others did not, leaving their systems vulnerable and exposing them to attacks that lead to ransomware. The considerable size and impact of the campaign warranted additional guidance on how to patch older systems. Unfortunately, installation instructions from patches were subject to interpretation, and if the recommendations were not followed correctly, additional issues were then reported.
Figure 5. Number of Exchange Server Vulnerabilities, February-May 2021
As a result, patches for Microsoft Exchange Server vulnerabilities, due to their severity, became available OOB prior to the March Patch Tuesday update. While some organizations were quick to patch their systems, others did not, leaving their systems vulnerable and exposing them to attacks that lead to ransomware. The considerable size and impact of the campaign warranted additional guidance on how to patch older systems. Unfortunately, installation instructions from patches were subject to interpretation, and if the recommendations were not followed correctly, additional issues were then reported.
 Figure 6. Tweet from the NSA warning the public about exploited vulnerabilities included in the April 2021 Patch Tuesday update
Unfortunately, these vulnerabilities from March were not the only significant vulnerabilities with potential damaging impact to organizations. Between February and mid-May, several more Critical vulnerabilities were disclosed and patched, including four reported by U.S. National Security Agency (NSA), two having a CVSS score of 9.8, and 13 CVEs having remote code execution issues (see Figure 7).
Figure 6. Tweet from the NSA warning the public about exploited vulnerabilities included in the April 2021 Patch Tuesday update
Unfortunately, these vulnerabilities from March were not the only significant vulnerabilities with potential damaging impact to organizations. Between February and mid-May, several more Critical vulnerabilities were disclosed and patched, including four reported by U.S. National Security Agency (NSA), two having a CVSS score of 9.8, and 13 CVEs having remote code execution issues (see Figure 7).
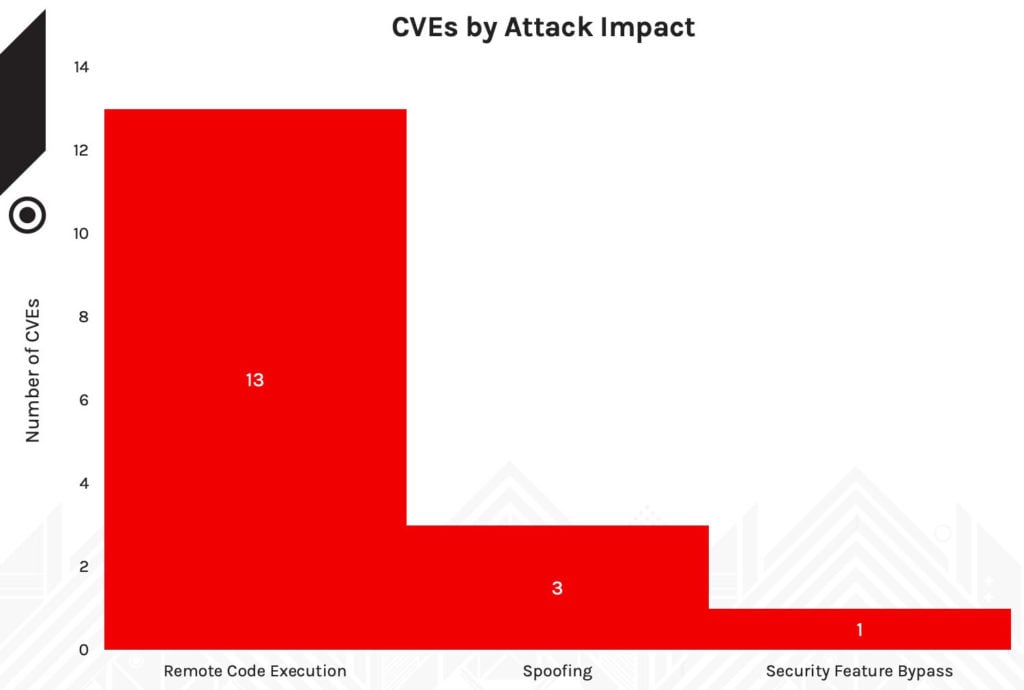 Figure 7. Attack impact of critical CVEs, February-May 2021
Of course, patching Microsoft Exchange Server comes with its challenges. The breadth of the affected versions (from Microsoft Exchange 2003 through Microsoft Exchange 2019) did not make the patching process a simple one. While the focus was placed on the four exploited CVEs, it’s important to highlight that if these vulnerabilities were not addressed in the release cycles between February and May, this would be a very critical issue that would need to be addressed by your security team.
Figure 7. Attack impact of critical CVEs, February-May 2021
Of course, patching Microsoft Exchange Server comes with its challenges. The breadth of the affected versions (from Microsoft Exchange 2003 through Microsoft Exchange 2019) did not make the patching process a simple one. While the focus was placed on the four exploited CVEs, it’s important to highlight that if these vulnerabilities were not addressed in the release cycles between February and May, this would be a very critical issue that would need to be addressed by your security team.
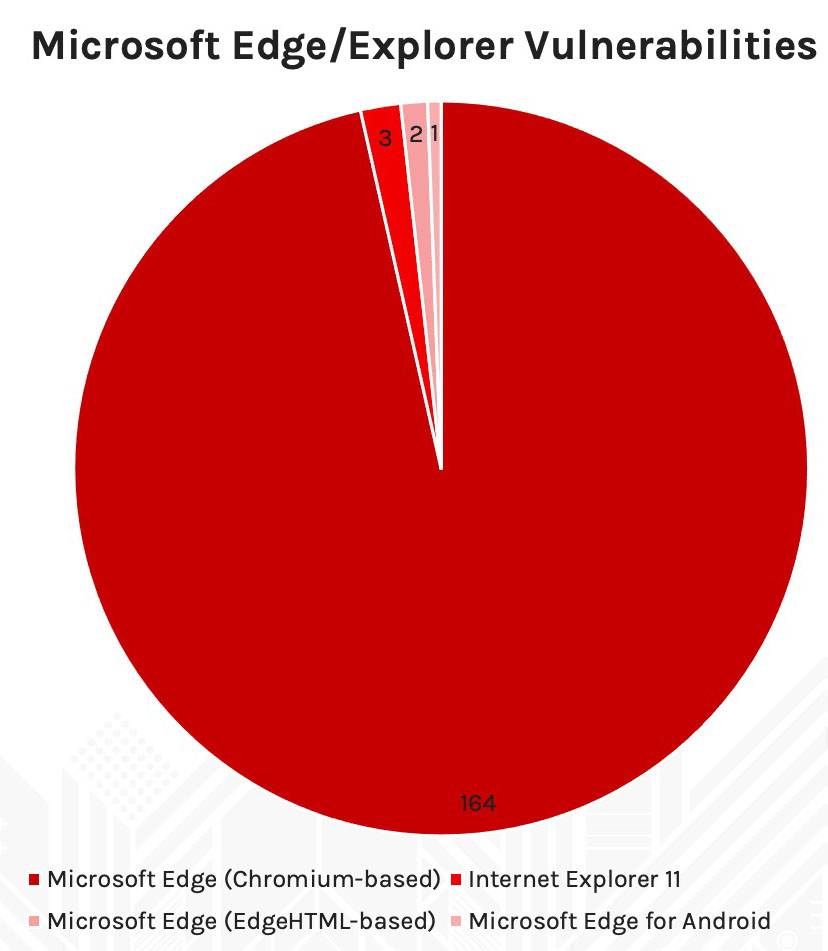 Figure 8. Microsoft Edge and Internet Explorer vulnerabilities, January-June 2021
Figure 8. Microsoft Edge and Internet Explorer vulnerabilities, January-June 2021
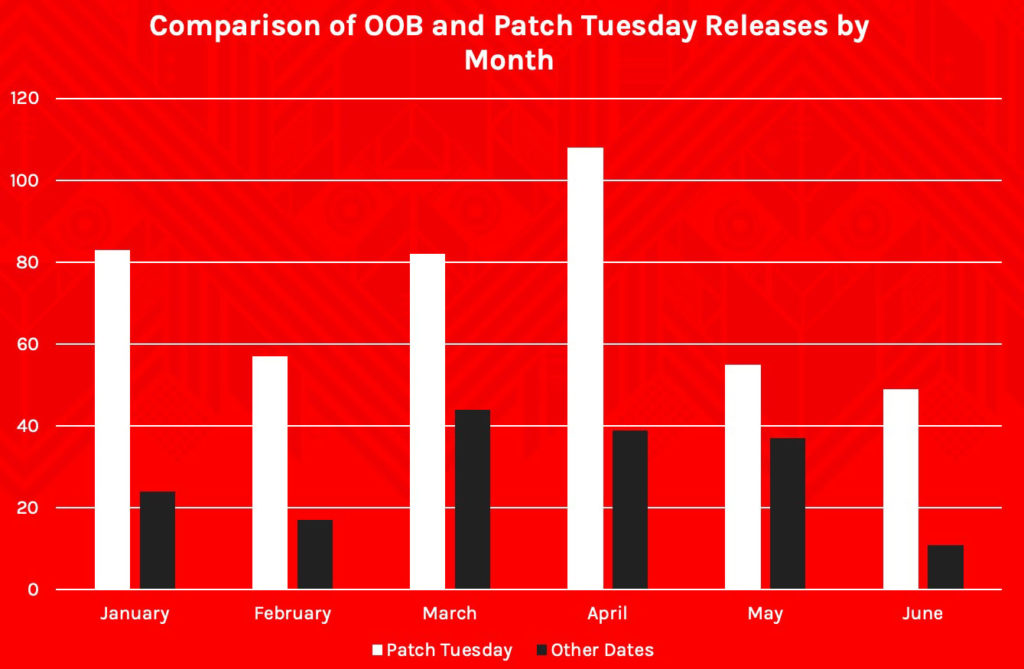 Figure 9. Comparison of OOB and Patch Tuesday releases by month, January-June 2021
Although confirming if an exploited vulnerability in one browser can be similarly triggered in the other presents a challenge when analyzing the data, understanding the risk it encompasses for organizations could be valuable. Microsoft Edge has a different update mechanism than other browsers — an “auto-update” feature that is turned on by default unless an organization has decided to manage it differently through a specific security policy.
It becomes easy for attackers to rely on a Chrome exploit to attack Microsoft Edge. Closing the gap between patching one and the other becomes critical for all organizations using these browsers.
Figure 9. Comparison of OOB and Patch Tuesday releases by month, January-June 2021
Although confirming if an exploited vulnerability in one browser can be similarly triggered in the other presents a challenge when analyzing the data, understanding the risk it encompasses for organizations could be valuable. Microsoft Edge has a different update mechanism than other browsers — an “auto-update” feature that is turned on by default unless an organization has decided to manage it differently through a specific security policy.
It becomes easy for attackers to rely on a Chrome exploit to attack Microsoft Edge. Closing the gap between patching one and the other becomes critical for all organizations using these browsers.
- Which products had the most vulnerability/patching activity
- Which vulnerabilities were exploited
- How frequently vulnerabilities were disclosed outside of Patch Tuesday
- How important these OOB disclosures are
Examining All Microsoft CVEs — Patched and Unpatched
It’s a bit misleading to rely on the number of CVEs that were patched by Microsoft within the analyzed time frame (434) when in reality, SecOps teams should look at the total number of vulnerabilities that affected Microsoft products (612). Vulnerabilities disclosed outside of Patch Tuesday have always been important because there tends to be a reason (e.g., in-the-wild exploitation) why Microsoft doesn’t wait for a scheduled event to patch them. Still, with the introduction of Chromium-based Edge, these vulnerabilities are more numerous than ever. (We explain why later under "The Lurking Danger of Microsoft Edge Browser Vulnerabilities.") We begin our analysis by examining Microsoft Patch Tuesday updates from January through June 2021. From here, we pull insights from the data about deployments, vulnerabilities and the information surrounding them. We then discuss OOB vulnerabilities. Figure 1. Number of CVEs that Microsoft released each month, January-June 2021
Figure 1. Number of CVEs that Microsoft released each month, January-June 2021
Vulnerability Analysis by Microsoft Product Families
As we review the data displaying vulnerabilities affected by Microsoft product family (see Figure 2), the initial breakdown shows that nearly four out of 10 vulnerabilities affected Microsoft Windows. Closely following this are vulnerabilities that affected different browsers and Extended Security Updates (ESU) programs.
As stated previously, a higher number of patches for vulnerabilities does not necessarily correlate with exploitation; however, it can signal where most of the vulnerabilities are reported. In most cases, you should note that each one of the groups across Microsoft’s product families could be patched or remediated in different ways.
Moving a little further into this data, we see that Windows 10 and Windows Server received the most patches (addressing 260 and 257 vulnerabilities, respectively) for the May 2020 update (2004) version. However, within the browser product family, we see that Microsoft Edge (Chromium-based) received the highest number of updates, with 164 vulnerabilities having been patched.
 Figure 2. Number of vulnerability patches released by Microsoft product family, January-June 2021
Figure 2. Number of vulnerability patches released by Microsoft product family, January-June 2021Depending on how you run Windows versions across your organization’s infrastructure, the actual total number of CVEs will vary, as will the strategy required to apply these updates. Of course, it's always important to patch as soon as you can, but when your team cannot, you should have security measures or mitigation processes in place to minimize your exposure to threats.
Exploited Vulnerabilities
According to the data reported by Microsoft (and other vulnerability reports affecting Google Chrome and Microsoft Edge), 21 CVEs were flagged with an exploited status. (Note that Microsoft does not appear to update the “exploit” label for vulnerabilities after publication.) Microsoft Exchange Server stole the spotlight earlier this year when a massive exploitation campaign was reported in March. The severity of this exploitation was enough that Microsoft pushed an OOB patch before the March Patch Tuesday update.Nevertheless, while Exchange Server was seeing mass exploitation issues, Windows and the various browser versions ended up having the greatest number of exploited vulnerabilities.
While June saw the highest number of vulnerabilities being exploited (all CVEs affecting specific components of Microsoft Windows), March contained the most exploited vulnerabilities, when vulnerabilities affecting Microsoft Office, Microsoft Edge and Internet Explorer are included alongside those related to Microsoft Exchange.
What does this data tell us? Three things:
- Patches for vulnerabilities that are released OOB should definitely be considered in your remediation plan, as they address serious exploits.
- OOB updates could indicate a possibly dangerous issue or set of issues.
- With an increase in OOB updates, there’s a corresponding increase in time and pressure put on your security teams. If more OOB updates are released in the coming months, you might need to reconfigure your patching process so as to not leave your organization vulnerable.
 Figure 3. Number of CVEs that Microsoft reported as exploited by month, January-June 2021
Figure 3. Number of CVEs that Microsoft reported as exploited by month, January-June 2021| Month | CVE | Affected Products |
| January 2021 | CVE-2021-1647 | Windows Defender |
| February 2021 | CVE-2021-1732 | Windows (OS) |
| February 2021 | CVE-2021-21148 | Microsoft Edge (Chromium-based) |
| March 2021 | CVE-2021-26855 CVE-2021-26857 CVE-2021-26858 CVE-2021-27065 | Microsoft Exchange |
| March 2021 | CVE-2021-27059 | Microsoft Office |
| March 2021 | CVE-2021-21166 CVE-2021-21193 | Microsoft Edge (Chromium-based) |
| March 2021 | CVE-2021-27085 | Internet Explorer 11 |
| March 2021 | CVE-2021-26411 | Internet Explorer 11, Internet Explorer 9, Microsoft Edge |
| April 2021 | CVE-2021-21220 | Microsoft Edge (Chromium-based) |
| April 2021 | CVE-2021-28310 | Windows (OS) |
| June 2021 | CVE-2021-30551 CVE-2021-30554 | Microsoft Edge (Chromium-based) |
| June 2021 | CVE-2021-31199 CVE-2021-31201CVE-2021-31955CVE-2021-31956CVE-2021-33739 CVE-2021-33742 | Windows (OS) |
Figure 4. Timeline graph, January-June 2021
How Important Are Out-of-band Vulnerability Updates? Very
Putting patch release dates into perspective, several vulnerabilities affecting Microsoft environments possess a different patching schedule. As stated above, while most products typically receive an update during the formal patch release cycle, our finding that a whopping 30% of vulnerabilities patched in the first half of 2021 happened outside of Patch Tuesday shows that you should consider addressing all OOB vulnerability updates.
A Note on PrintNightmare: Remote Code Execution on Print Spooler Service
An example of in- and out-of-band updates would be the recent PrintNightmare situation. An update in the June Patch Tuesday release included a fix for CVE-2021-1675. This CVE addresses a remote code execution vulnerability within Windows Print Spooler. This service had been the target of previous exploits; however, this time researchers reported that previous updates opened additional vulnerabilities relating to print spooler. As exploits associated with this vulnerability became public, Microsoft acknowledged the situation and assigned a new CVE (CVE-2021-34527). Recommendations include disabling the print spooler service and setting up different registry values to guarantee that attackers would not be able to rely on this vulnerability to compromise domain controllers. Microsoft released an OOB patch during the first days of July. After patches for CVE-2021-34527 were released, a local privilege escalation vulnerability that affected the same service was reported and Microsoft assigned a new CVE (CVE-2021-34481) that, as of July 15, was still under analysis.PrintNightmare continues to be under investigation, and though the remote code execution vulnerability has been patched, there are still vulnerabilities, which means this situation is still open and not resolved. If an organization only relied on Patch Tuesday releases, and used print spooler services within their business, they would be left open and vulnerable to an attack.
Spotlighting Microsoft Exchange Server Vulnerabilities
If your organization uses Microsoft Exchange Server, and your security team is not aware of the mass Microsoft Exchange Server exploitation campaign that occurred in March, you should learn about it and consider moving these vulnerabilities up in your prioritization schedule. (In summary, attackers aimed to drop an ASPX-based webshell onto vulnerable Microsoft Exchange servers by exploiting multiple zero-day vulnerabilities — CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065. To learn more, we recommend reading how the Falcon Complete Team handled this campaign.) Figure 5. Number of Exchange Server Vulnerabilities, February-May 2021
Figure 5. Number of Exchange Server Vulnerabilities, February-May 2021 Figure 6. Tweet from the NSA warning the public about exploited vulnerabilities included in the April 2021 Patch Tuesday update
Figure 6. Tweet from the NSA warning the public about exploited vulnerabilities included in the April 2021 Patch Tuesday update Figure 7. Attack impact of critical CVEs, February-May 2021
Figure 7. Attack impact of critical CVEs, February-May 2021Reviewing Other Exploited Windows Vulnerabilities
February and April each saw one Windows vulnerability being exploited, with the other six Windows vulnerabilities receiving updates on June’s Patch Tuesday. Vulnerabilities reported in February and April relate to a privilege escalation vulnerability affecting Win32k. CVE-2021-28310, reported in April as an OOB vulnerability, was speculated to be used by multiple threat actors. The June 2021 Patch Tuesday release had a different mix, with four of the six being privilege escalation vulnerabilities. One example, CVE-2021-33742, is a remote code execution vulnerability affecting the Windows MSHTML engine used in Microsoft Internet Explorer and other applications. Because ofthis scope, and because the vulnerability affects all supported Windows versions at the time of release, CrowdStrike highly recommends prioritizing this CVE and patching it as soon as possible. With the increase in exploited and OOB vulnerabilities, it stands to reason that organizations around the globe should immediately examine the vulnerabilities relating to CVE-2021-33742 and it’s associated patches.
The Lurking Danger of Microsoft Edge Browser Vulnerabilities
When it comes to the hidden dangers of OOB vulnerabilities and their associated patches, organizations that use the Chromium-based Microsoft Edge browser might face a significant threat in light of the vulnerabilities that have been affecting this browser. Why? Browsers are known to be high-ranking targets for attackers. In just the first half of this year alone, we’ve seen numerous zero-day vulnerabilities affecting browsers (five out of the six CVEs have been reported with in-the-wild exploits affecting Microsoft Edge). Our analysis found within the four unique products of the Microsoft browser family 170 vulnerabilities — 164 of them affecting Microsoft Edge (Chromium-based) (Figure 8 below shows the list of products affected). This product set follows an entirely different cadence of security updates that does not align with the Microsoft cycle of Patch Tuesday updates. Other than a patch for CVE-2020-17163 on Visual Studio Code, Microsoft has not provided additional updates for any other software within this set.Additionally, beyond being a favorite attack surface for criminal actors, Microsoft Edge is unfortunately approximately two days behind Chrome updates (because the Edge browser relies on the Chromium OS). In most cases, vulnerabilities affecting both browsers would get patched first on Google Chrome and then on Microsoft Edge. For example, CVE-2021-30551 was reported as exploited, and a patch was released on Google Chrome on June 9. The fix for Microsoft Edge arrived on June 11. This different release schedule for Microsoft browsers based on Chromium appears to be highly related to how vulnerabilities are reported and patched within the Chromium Project. There’s a higher cadence of updates than Patch Tuesdays. If this cadence isn’t followed, organizations using Microsoft Edge would be exposed to vulnerabilities already patched in Google Chrome. If your SecOps team has been treating Edge browsers like all other Microsoft products — as in rolling it in with a once-monthly patching cadence — you may be leaving your organization open to a higher security risk and more opportunity for attackers.
 Figure 8. Microsoft Edge and Internet Explorer vulnerabilities, January-June 2021
Figure 8. Microsoft Edge and Internet Explorer vulnerabilities, January-June 2021 Figure 9. Comparison of OOB and Patch Tuesday releases by month, January-June 2021
Figure 9. Comparison of OOB and Patch Tuesday releases by month, January-June 2021Conclusion
Microsoft Patch Tuesday is one of the most important events for an organization’s vulnerability management process. Every month, it drives actions across organizations, spread over numerous Microsoft products and applications. Most vulnerabilities are patched by applying operating system patches. In many cases, these updates require a reboot and need to be accounted for, especially for servers. Employees often require assistance to patch their devices to minimize an organization’s risk properly, but how organizations decide to approach this may vary. The more you can leverage and direct communication between your security teams by identifying the vulnerabilities and encouraging these teams to apply these patches, the more robust your organization’s security posture will be. Your vulnerability management and patching strategy should be reviewed regularly to handle these updates, both in- and out-of-band. In most scenarios, a regular cycle will help to manage the standard Patch Tuesday release cadence. However, if there is no flexibility for out-of-band patches, or if your applications update more frequently than known by security or IT teams, then this might be a riskier situation that needs to be addressed with more urgency.
Additional Resources
- Try a free trial of Falcon Spotlight™.
- Make prioritization painless and efficient. Watch how Falcon Spotlight enables IT staff to improve visibility with custom filters and team dashboards.
- Learn more on how Falcon Spotlight can help you discover and manage vulnerabilities in your environments.
- See how Falcon Complete stops Microsoft exchange server zero-day exploits.
- Learn about the recent Baron Samedit vulnerability and CrowdStrike’s custom dashboard.
- Test CrowdStrike next-gen AV for yourself. Start your free trial of Falcon Prevent™ today.






![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeincstage/Edward-Gonam-Qatar-Blog2-1)

































